- 1. What is the difference between a business and consumer proxy?
- 2. How do proxy servers work?
- 3. What are the benefits of proxy servers?
- 4. What are the limitations of proxy servers?
- 5. What are the different types of proxy servers?
- 6. Comparing proxy servers with other types of security technologies
- 7. Proxy server FAQs
- What is the difference between a business and consumer proxy?
- How do proxy servers work?
- What are the benefits of proxy servers?
- What are the limitations of proxy servers?
- What are the different types of proxy servers?
- Comparing proxy servers with other types of security technologies
- Proxy server FAQs
What Is a Proxy Server? [Definition & Explanation]
- What is the difference between a business and consumer proxy?
- How do proxy servers work?
- What are the benefits of proxy servers?
- What are the limitations of proxy servers?
- What are the different types of proxy servers?
- Comparing proxy servers with other types of security technologies
- Proxy server FAQs
A proxy server is a network-layer device that intercepts traffic between a client and a destination. It evaluates, forwards, or modifies that traffic based on how it's configured.
In business environments, proxy functionality is commonly built into security infrastructure like next-generation firewalls, load balancers, and web application firewalls.
What is the difference between a business and consumer proxy?
Before we get into the details of proxy servers, it's worth taking a moment to make a distinction between business and consumer grade proxy servers.
Consumer proxies are typically used by individuals who want more privacy or access to restricted content. They're often browser-based, limited in scope, and configured manually to mask the user's IP address or bypass geo-blocks.
Enterprise proxies are integrated into the network infrastructure itself. They operate at scale and support centralized control, traffic inspection, and policy enforcement.
Enterprise proxy functionality is often built into tools like next-generation firewalls, load balancers, or WAN optimizers.
How do proxy servers work?
The process differs slightly between business and consumer proxy server products.
Here's how a business proxy server works:
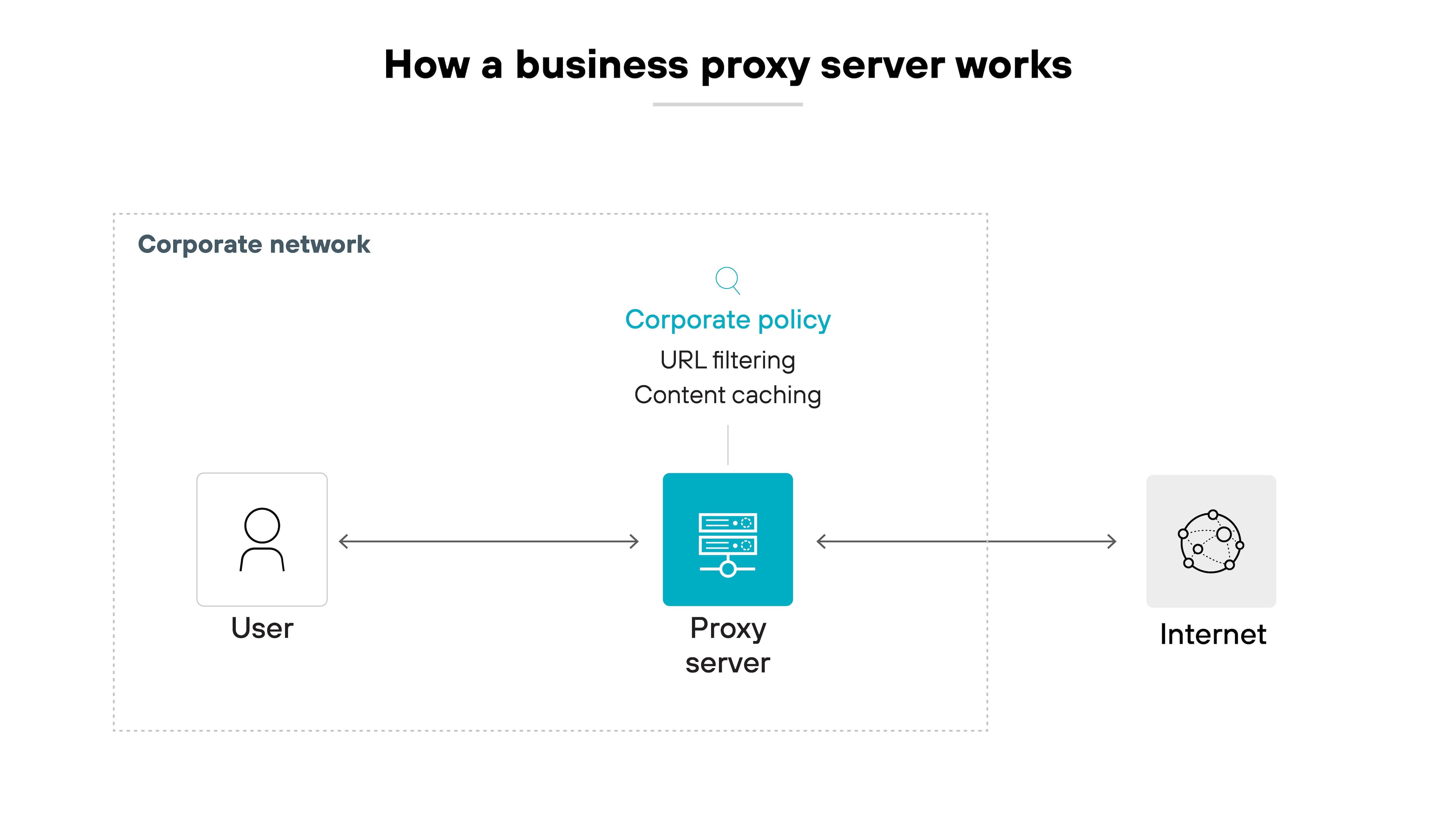
- A user sends a request, which the proxy intercepts.
- The proxy responds to the request back to the client to keep the session open, and opens a second connection to the destination.
- This gives the proxy full visibility into the traffic — allowing for decryption, inspection, filtering, and policy enforcement.
- Proxies may also cache content or reroute traffic for performance and reliability.
- Most enterprise proxies operate transparently, with no user configuration needed.
Here's how a consumer proxy works:
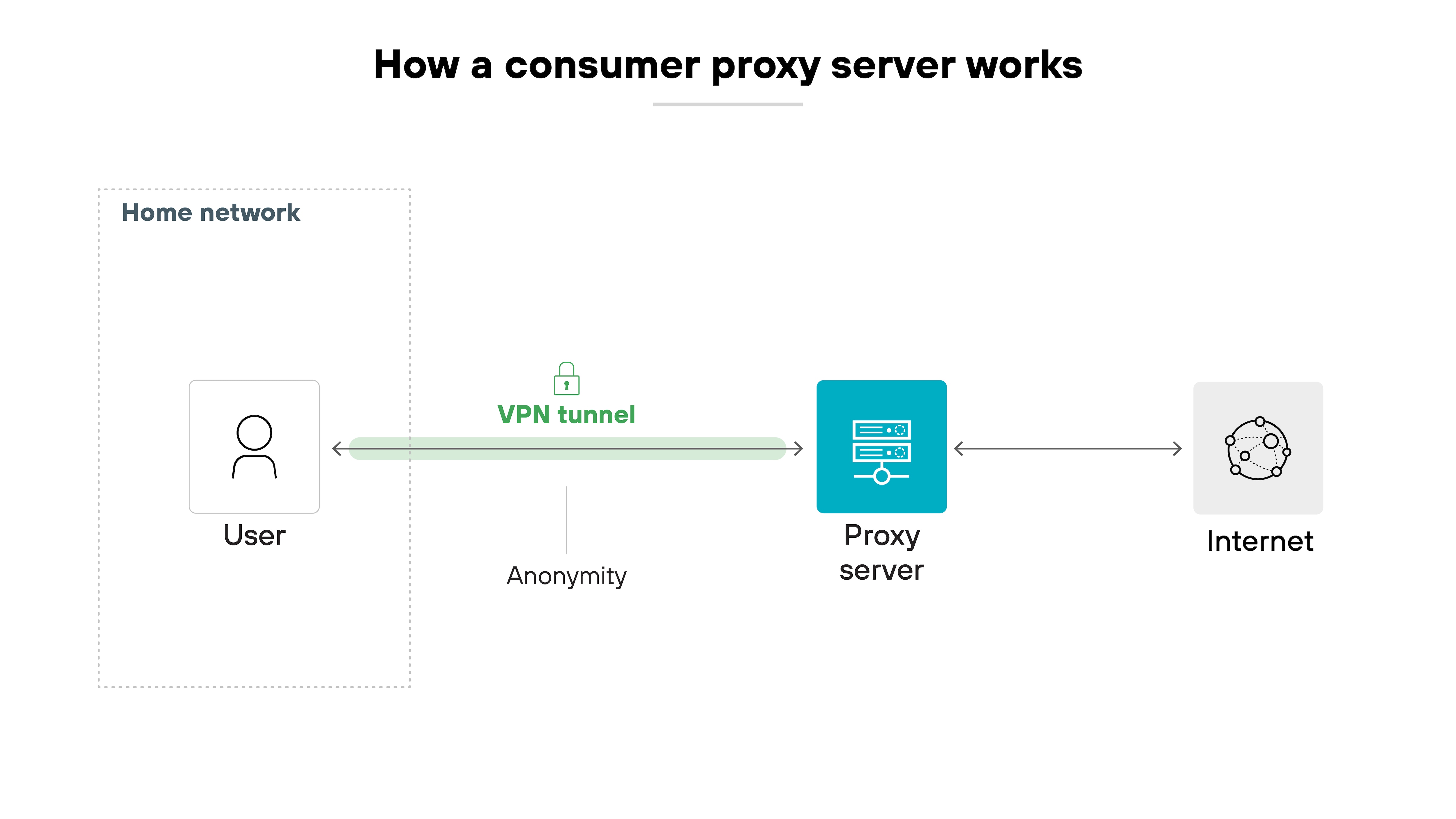
- The user configures a proxy in their browser or OS.
- All web requests are routed through the proxy server.
- The proxy replaces the user's IP address with its own and forwards the request to the destination site.
- It may return cached content or filter requests based on user-defined rules.
What are the benefits of proxy servers?
Proxy servers offer different benefits depending on where and how they're used.
The table below breaks down common benefits for both enterprise and consumer environments.
Proxy server benefits |
||
|---|---|---|
| Type | Benefit | Description |
| Enterprise proxy benefit | TLS decryption | Terminates encrypted sessions so tools can inspect HTTPS traffic. |
| App-layer policy enforcement | Applies URL filtering, application controls, and malware scanning. | |
| DLP and logging visibility | Logs traffic to show what data is in motion, by whom, and where it's going. | |
| Traffic routing and filtering | Supports SD-WAN, load balancing, and policy-based traffic control. | |
| Transparent operation | Works in-line without requiring any user configuration. | |
| Consumer proxy benefit | IP masking | Replaces the user's IP to make activity harder to trace. |
| Bypass content restrictions | Routes around blocked websites or network filters. | |
| Location spoofing | Makes traffic appear to originate from another country. | |
| Circumvent geo-blocking | Accesses region-specific sites by routing through a proxy. | |
| Reduce ISP tracking | Limits visibility into browsing activity, though without encryption. | |
What are the limitations of proxy servers?
Proxy servers play a critical role in both consumer and enterprise environments, but they aren't without limitations. Some of the most common concerns are misunderstood or misattributed, especially when consumer and enterprise use cases are conflated.
In enterprise environments, proxying is a foundational mechanism that enables deeper visibility, control, and traffic enforcement. But it comes with tradeoffs — not in terms of security flaws, but in terms of scale, complexity, and compatibility.
In consumer settings, proxy servers are often used for privacy, location masking, or bypassing content restrictions. But when these services are unvetted — especially free proxies — they introduce a different set of limitations, often tied to trust, transparency, and security.
The tables below break down the most common limitations of proxy servers in both enterprise and consumer contexts.
Proxy server limitations |
||
|---|---|---|
| Type | Limitation | Description |
| Enterprise proxy limitation | Scalability | Decrypting and inspecting traffic at scale requires significant processing power and memory. |
| Latency | Session termination and inspection can add delay, especially with deep inspection and logging. | |
| Management complexity | Certificate handling, session timeouts, and exception management can add operational overhead. | |
| Application compatibility | Some legacy apps or apps with certificate pinning may break or require reconfiguration. | |
| Consumer proxy limitation | Traffic logging and data resale | Some services collect and sell user data, including IP addresses and browsing activity. |
| Lack of trust and transparency | Users may not know who operates the proxy or whether it's secure or ethical. | |
| No encryption guarantees | Basic proxies don't encrypt traffic, exposing data on public or untrusted networks. | |
| Malvertising and content injection | Free proxies may inject ads or alter content, potentially exposing users to malware. | |
What are the different types of proxy servers?
Proxy servers can be categorized based on their role in the network, how visible they are to users, or the kinds of traffic they support.
By network role
Forward proxy
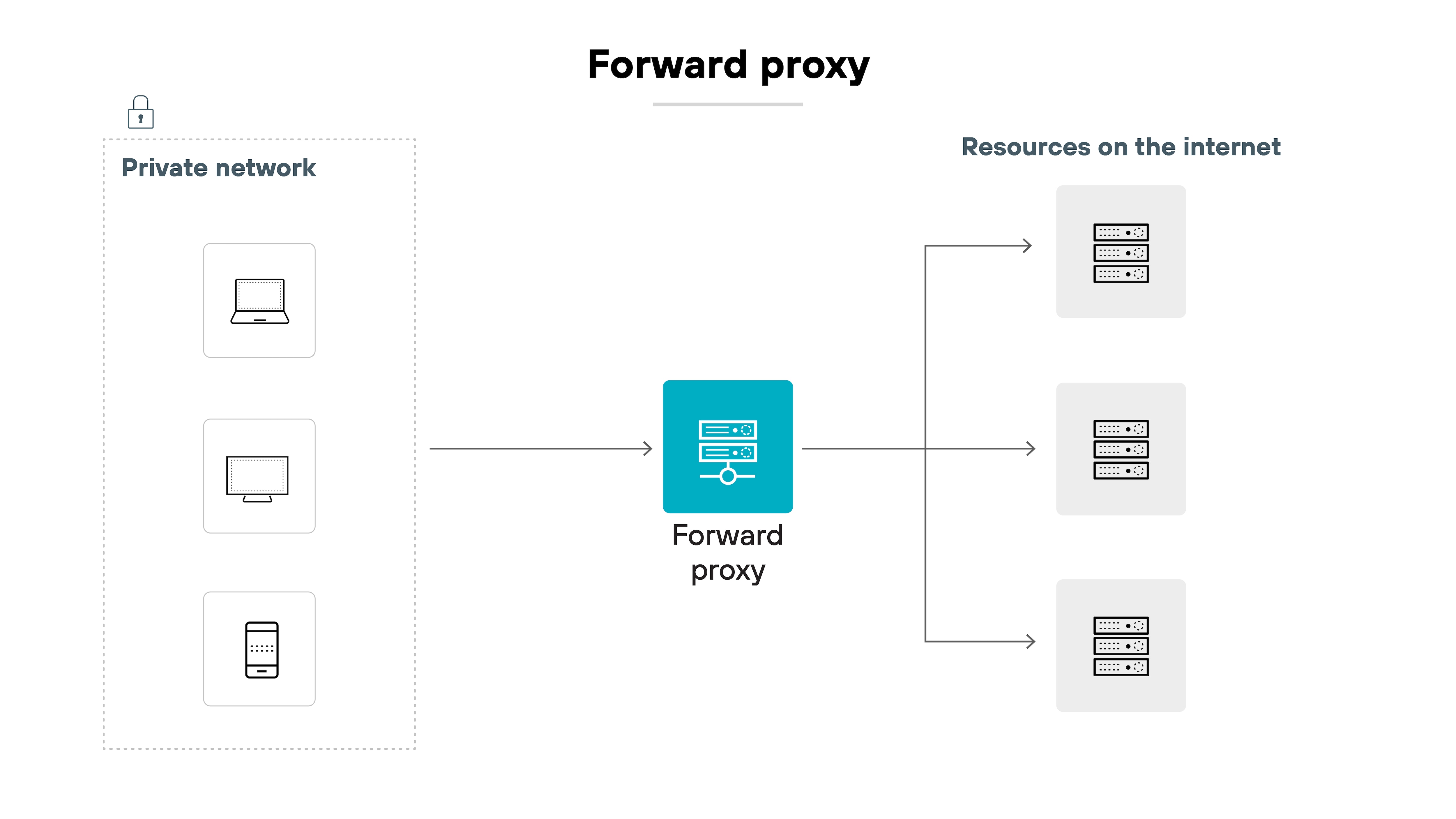
A forward proxy acts on behalf of the client. It sits between internal users and external services, forwarding client requests to the internet. This is the most common type of proxy in enterprise networks, where it's used for traffic filtering, TLS decryption, policy enforcement, and user activity logging.
Applies to: Business
Reverse proxy
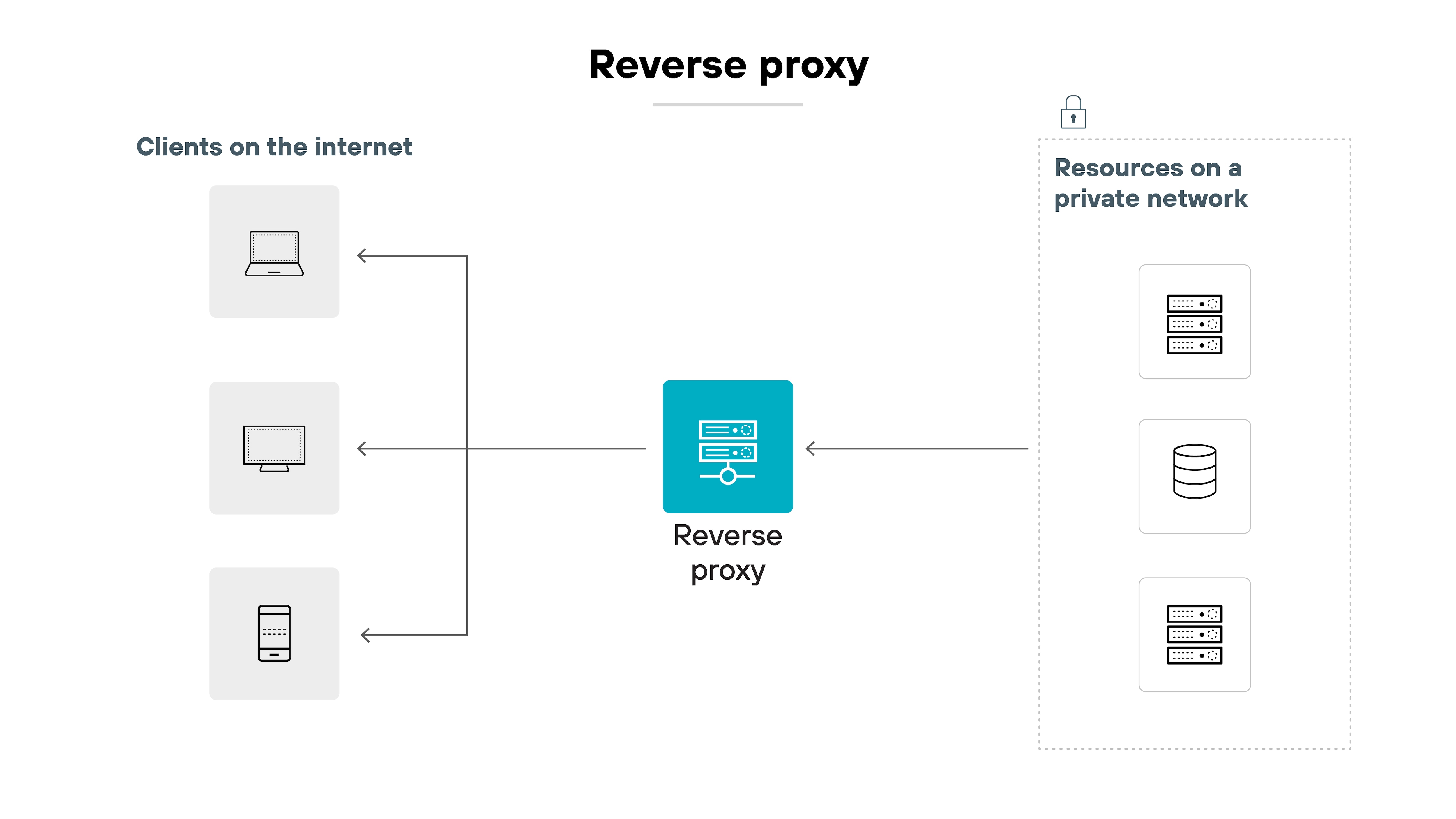
A reverse proxy acts on behalf of a server or service. It receives incoming requests from external clients and routes them to backend systems. Reverse proxies are typically used for load balancing, TLS termination, traffic steering, and web application protection.
Applies to: Business
By transparency and behavior
Transparent proxy
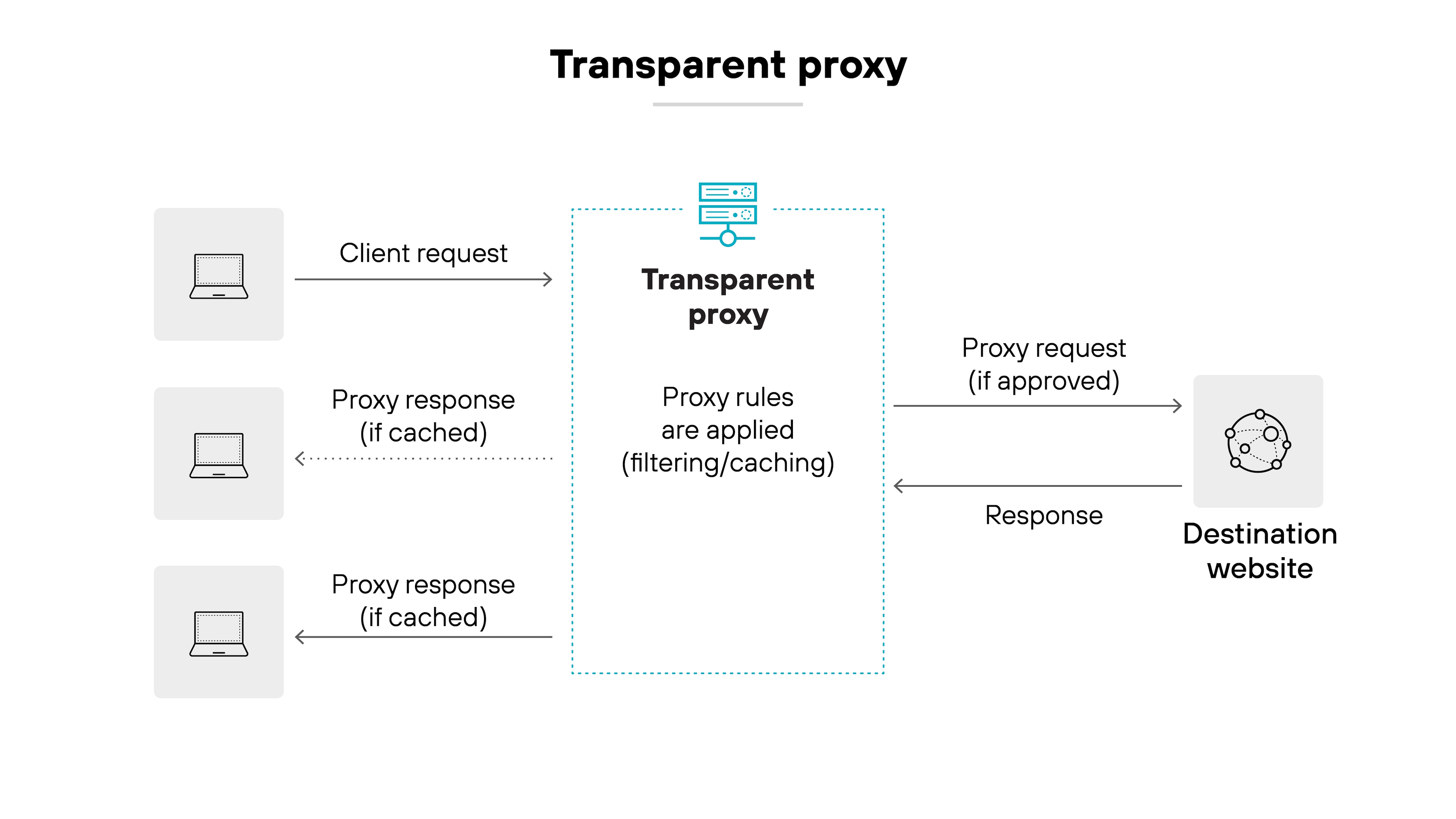
Transparent proxies intercept traffic without requiring users to manually configure proxy settings. They're common in enterprise deployments because they simplify user experience while allowing centralized policy enforcement. Despite being “invisible” to the user, they still inspect, filter, and log traffic.
Applies to: Business
Explicit proxy
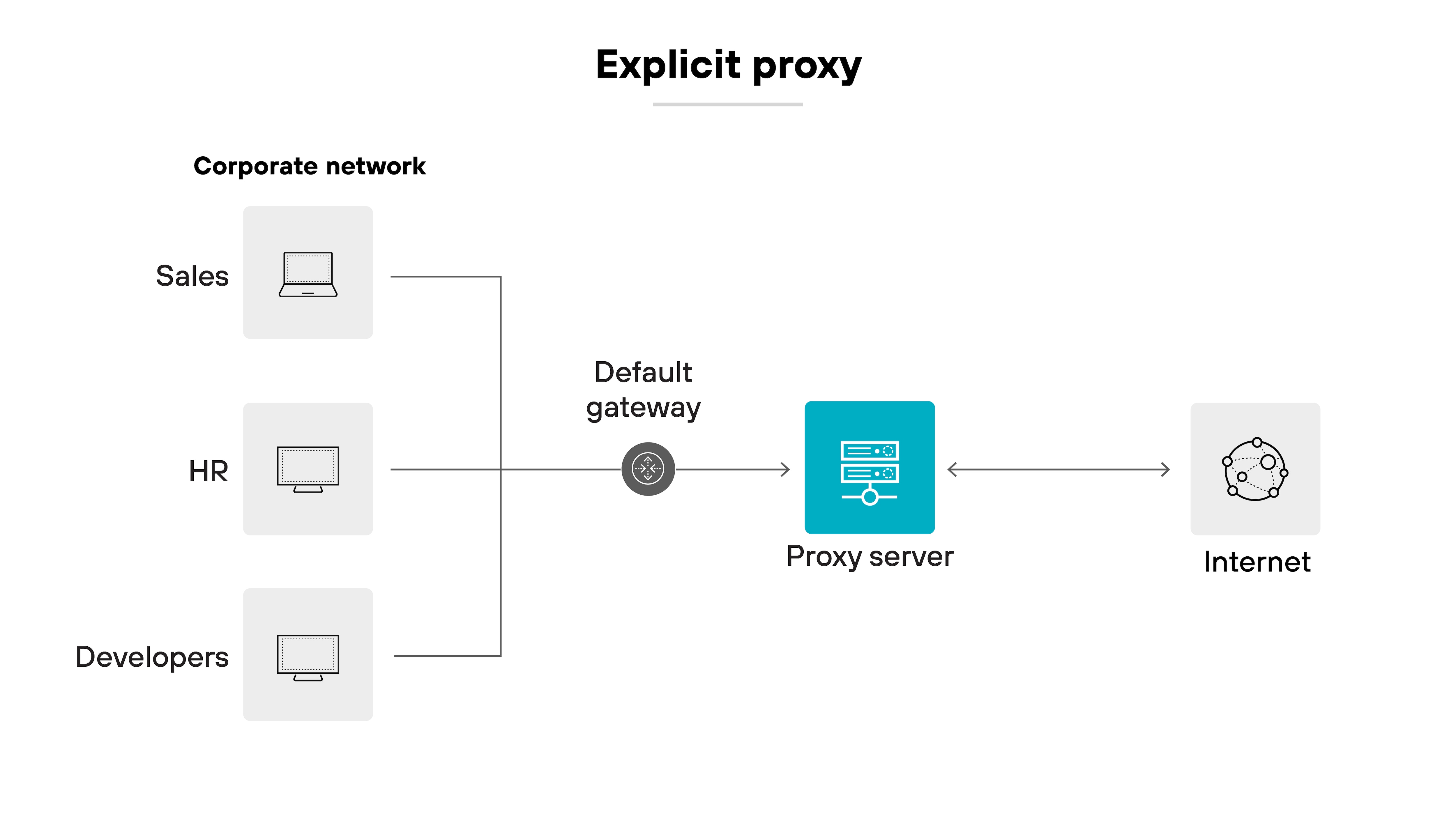
An explicit proxy requires the client device or application to be configured with the proxy's address. While more rigid from a usability standpoint, explicit proxies give organizations tighter control over which traffic is proxied and how it's handled.
Applies to: Business
Anonymous proxy
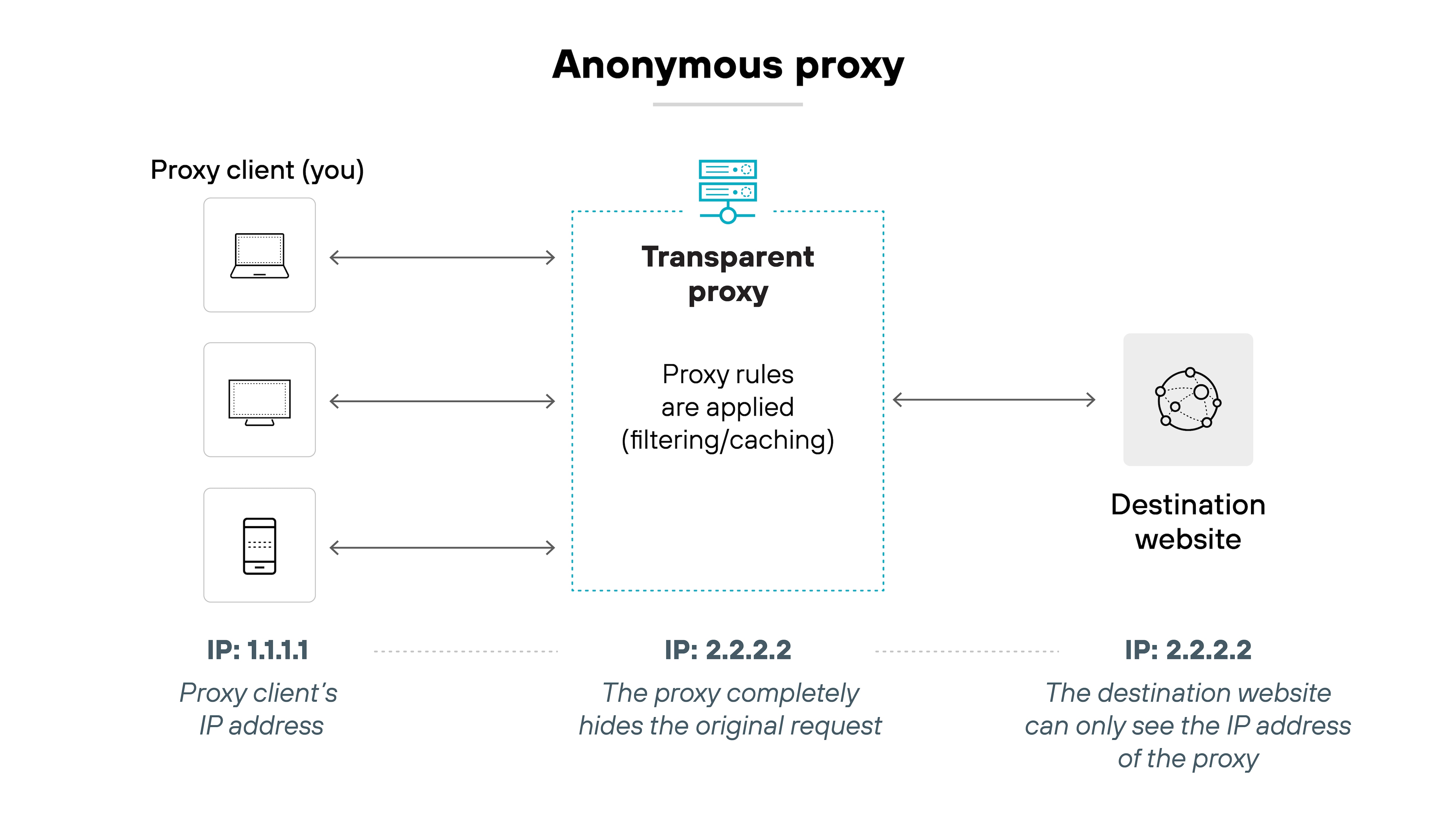
Anonymous proxies mask a user's IP address to increase online privacy or bypass content restrictions. These are rarely used in enterprise environments and often lack the inspection, control, or trust models required for secure deployment.
Applies to: Consumer
By protocol support
HTTP/HTTPS proxy
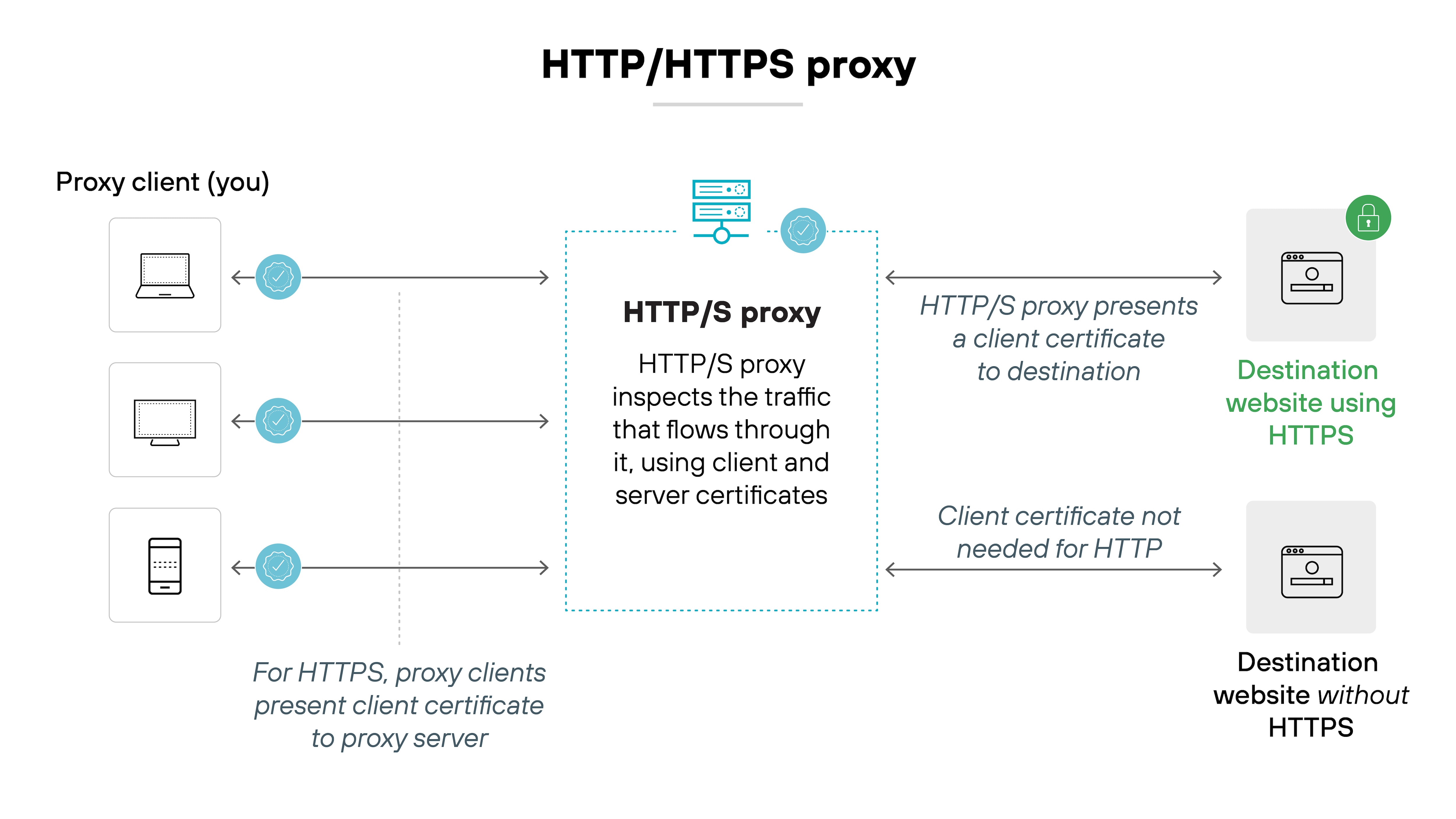
These proxies are designed for web traffic. HTTP proxies can inspect unencrypted traffic, while HTTPS proxies can decrypt and inspect TLS-encrypted traffic if configured with the appropriate certificates. They're widely used in enterprise firewalls and secure web gateways.
Applies to: Business
SOCKS proxy
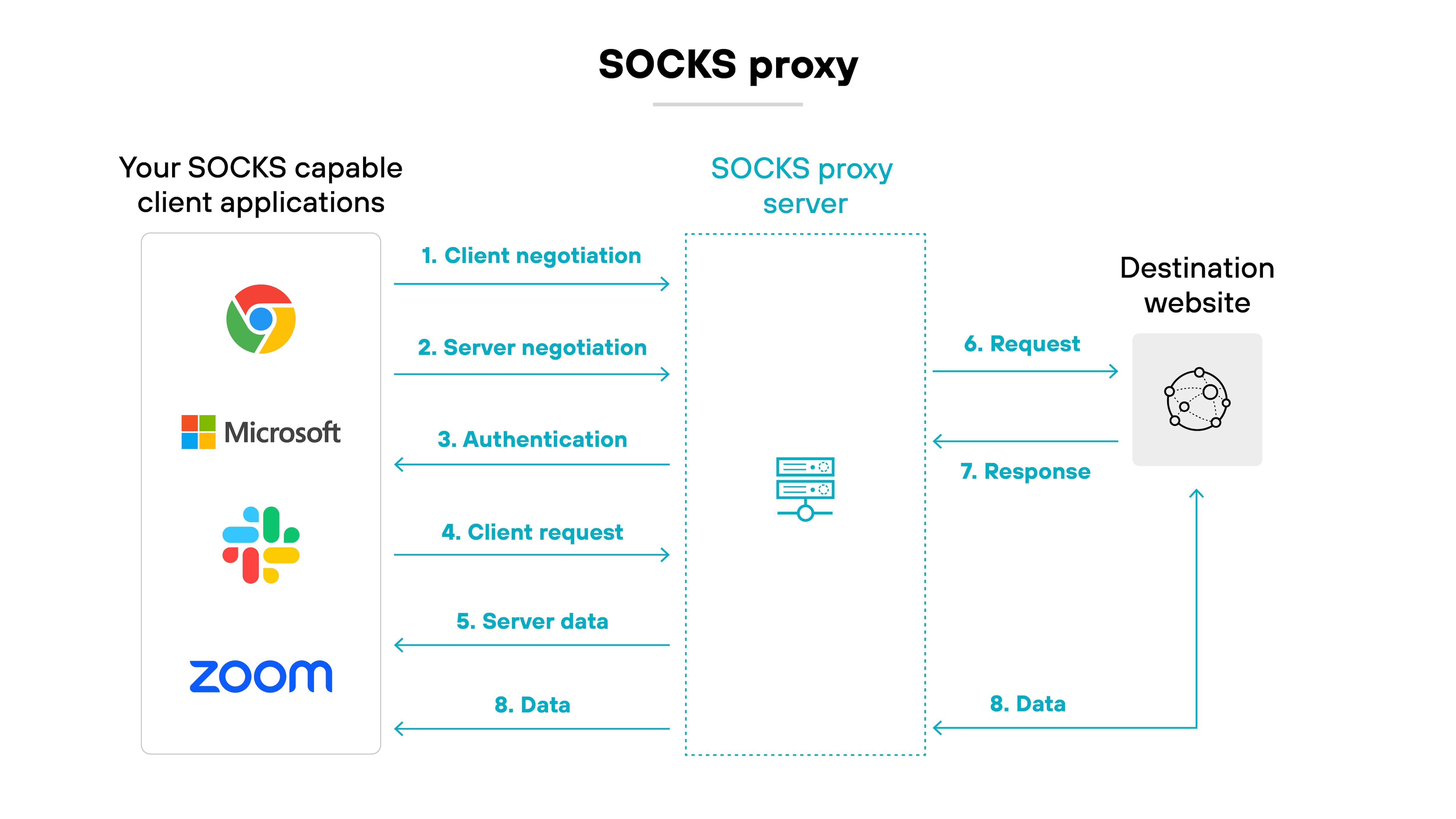
A protocol-agnostic proxy that forwards traffic from any TCP or UDP connection. SOCKS proxies don't inspect traffic — they simply pass it through. They're used more often for location masking or circumvention, not enterprise-grade traffic control or visibility.
Applies to: Consumer
Comparing proxy servers with other types of security technologies
Proxy servers aren't the only technology that reroutes or inspects traffic.
To understand how they fit into broader security architectures, it's useful to compare them with three common alternatives: VPNs, secure web gateways (SWGs), and secure access service edge (SASE) solutions.
Each technology offers different levels of visibility, encryption, and control.
| Parameter | Proxy server | VPN | SWG (secure web gateway) | SASE (secure access service edge) |
|---|---|---|---|---|
| Traffic encryption | None by default | Full encryption of all traffic | Encrypts and inspects HTTP/HTTPS traffic | Encrypts and inspects all traffic across protocols |
| Traffic scope | Application-level | System-level | Web traffic (HTTP/HTTPS) only | All ports, protocols, users, and locations |
| IP address masking | Yes | Yes | Yes (as part of proxy-based inspection) | Yes (via integrated identity and access controls) |
| Data privacy | Limited — data not encrypted | Strong — encrypted in transit | Moderate — focused on web data inspection | High — encryption plus identity-aware policy enforcement |
| Performance impact | Low (may use caching) | Moderate (due to encryption overhead) | Moderate — depends on inspection depth | Moderate to high — depends on architecture and implementation |
| Setup complexity | Requires per-app or per-device config | One-time setup for all apps | Deployed as part of cloud or on-prem network perimeter | Delivered as a unified cloud service, can replace multiple point solutions |
| Primary use case | Privacy, IP masking, content filtering | Secure remote access, privacy, data protection | Web security and filtering, agentless inspection | Converged networking and security for remote and hybrid workforces |
| Enterprise role | Used in isolation or within SWG/SASE stacks | Used for secure remote employee access | Provides controlled access to web content, malware defense | Full-featured secure connectivity platform with networking and security in one |
As the table shows, proxy servers offer lightweight traffic control, while VPNs, SWGs, and SASE provide broader security coverage depending on organizational needs.