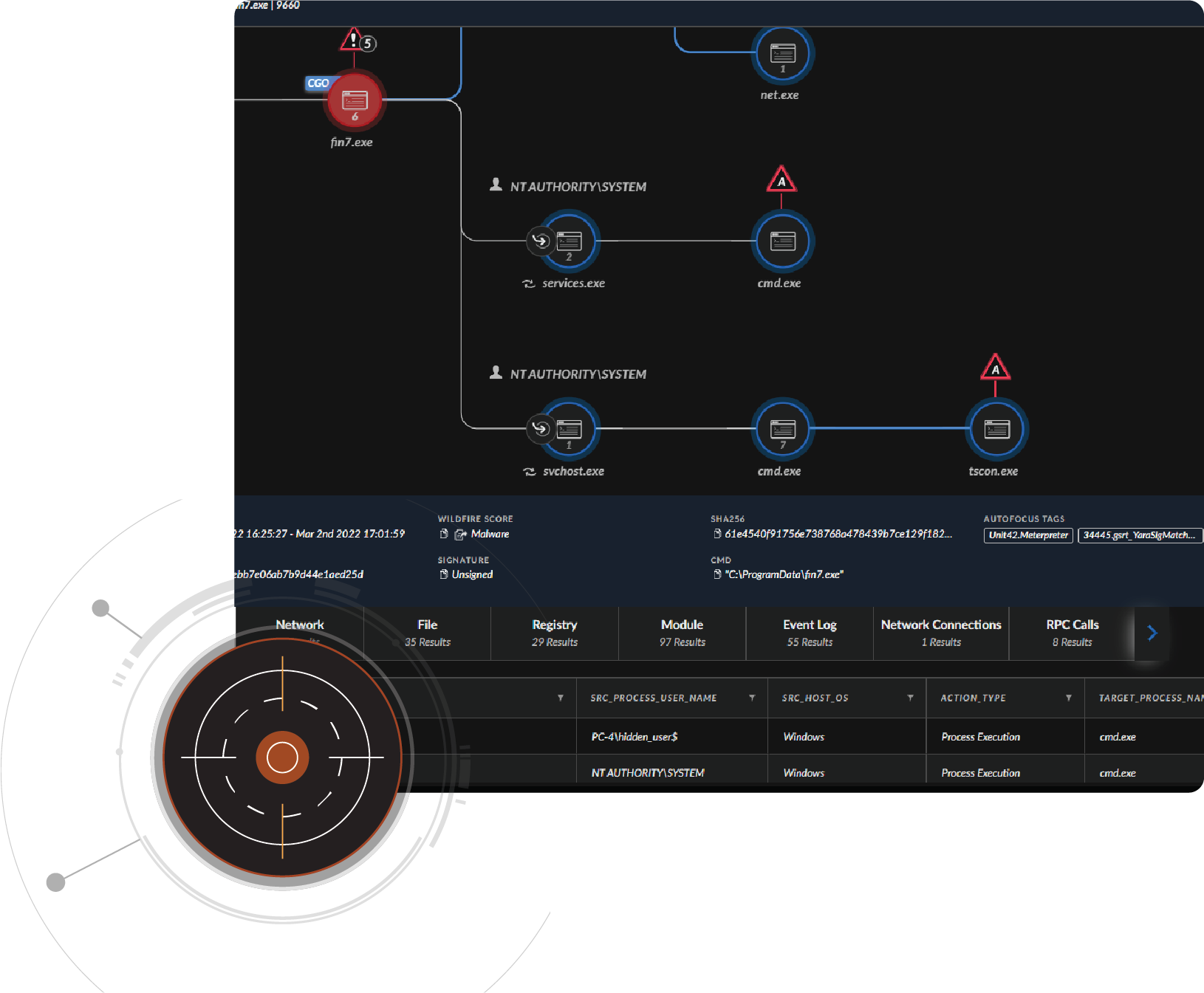
Gain peace of mind with on-demand access to our experts
With a Unit 42 Retainer, you make our experts an extension of your team. You place them on speed dial for incident response services with pre-negotiated terms and faster response times whenever you require assistance. Retainer credits can also be used toward cyber risk management services to help proactively improve your security posture.