-
- Endpoint Security Antivirus Explained
- Understanding Endpoints in Cybersecurity
- Why Endpoint Security Antivirus is Crucial for Modern Cybersecurity
- Endpoint Antivirus vs. Endpoint Security: What Is the Difference?
- Key Components of a Comprehensive Endpoint Security Solution
- How Endpoint Security Antivirus Works
- Implementing and Optimizing Endpoint Security Antivirus
- Choosing the Right Endpoint Security Antivirus Solution
- Challenges and Future Trends in Endpoint Security
- Endpoint Security Antivirus FAQs
Table of Contents
-
What Is Endpoint Security? EPP, EDR, and XDR Explained
- Key Data: Fronts of Attacks
- Why Endpoint Security Is Mandatory
- How Does Endpoint Security Work?
- Types of Endpoint Security: A Multi-Layered Approach
- Traditional Antivirus vs. Modern Endpoint Security
- Implementing Zero Trust for Endpoint Security
- Other Key Components
- Selecting the Optimal Endpoint Security Solution
- Strategic Endpoint Security: Challenges and Best Practices
- Endpoint Security FAQs
- What Is the Difference Between Advanced Endpoint Security and Antivirus (AV)?
-
What is Endpoint Security Awareness Training?
- Understanding Security Awareness Training
- Endpoint Security Awareness Training Explained
- What Does Endpoint Security Awareness Training Cover?
- Why Is Security Awareness Training Important?
- How to Build an Effective Endpoint Security Awareness Training Program
- Industry Awareness Training Case Studies and Success Stories
- The Future of Endpoint Security Awareness Training
- Endpoint Security Awareness Training FAQs
- What Is Endpoint Detection?
-
What Is Endpoint Security Software? How It Stops Cyberattacks
- Endpoint Security Software Explained
- Endpoint Security Software vs. Antivirus
- Core Components of Comprehensive Endpoint Security Software
- How Does Endpoint Security Software Protect a Network?
- What are the Key Features of Endpoint Security Software?
- EPP vs. EDR vs. XDR
- The Role of Threat Hunting in Endpoint Security
- Implementation Strategies for Enterprise Environments
- Defending Against Ransomware: A Use Case
- Endpoint Security Software FAQs
- What Is an Endpoint? Understand Devices, Risks & Security
-
What Is an Endpoint Protection Platform?
- Understanding Endpoint Protection Platforms (EPPs)
- The Importance of Endpoint Protection for Enterprises
- What Cybersecurity Practitioners and CISOs Need to Know About EPPs
- Traditional vs. Cloud Native EPPs
- EPP vs EDR: A Comparative Analysis
- Case Studies: Real-World Applications
- How to Choose the Best EPP
- Endpoint Protection Platform (EPP) FAQs
- What are the Types of Endpoint Security?
- What Is Next-Generation Antivirus (NGAV)
What Is Endpoint Security Antivirus?
5 min. read
Table of Contents
Endpoint security antivirus is a cybersecurity solution designed to protect endpoint devices, such as laptops, desktops, and mobile phones, from various cyber threats. It utilizes a combination of traditional signature-based detection, behavioral analysis, and advanced machine learning to identify, prevent, and remediate malware and other malicious activities in real time.
Key Points
- Core Function: Endpoint security antivirus safeguards individual devices from malware, viruses, and other cyber threats.
- Beyond Antivirus: It extends traditional antivirus capabilities with additional security measures, including firewalls, data loss prevention, and device control.
- Multi-Layered: Modern solutions employ multiple detection techniques, including signature matching, behavioral analysis, and machine learning, to enhance security.
- Centralized Management: Business-grade solutions offer centralized management for efficient deployment, monitoring, and policy enforcement across all devices.
- Crucial Protection: It is essential for protecting sensitive data, maintaining business operations, and preventing widespread network infections.
- Evolving Landscape: Endpoint security continuously adapts to combat new and sophisticated threats, including zero-day attacks and advanced persistent threats.
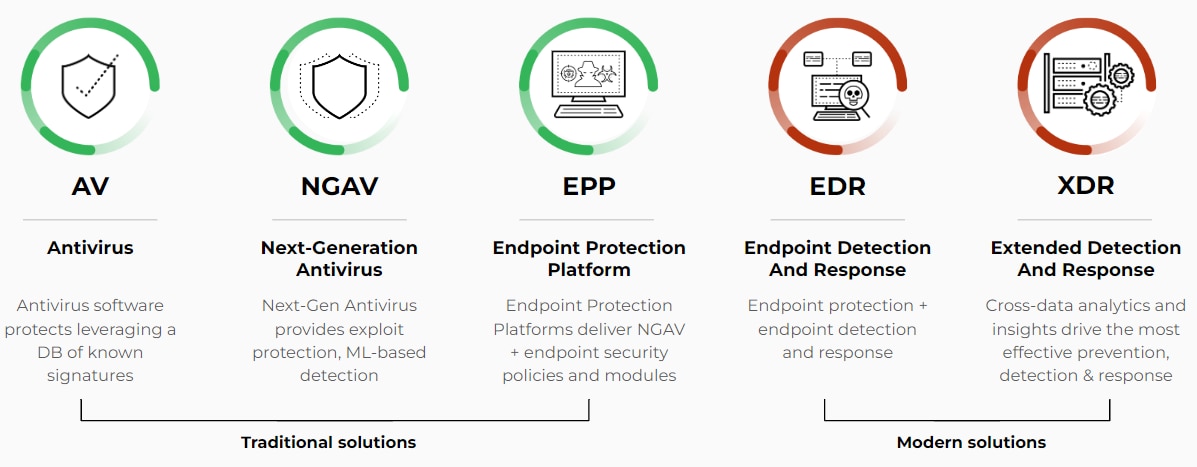
Figure 1: Endpoint security solutions available today
Endpoint Security Antivirus Explained
Modern endpoint security antivirus solutions extend far beyond traditional signature-based detection, integrating advanced capabilities to safeguard digital assets at their access points.
These sophisticated platforms prevent malware infections, detect suspicious activities, and enable rapid response to security incidents. Their importance stems from endpoints serving as common entry points for cyberattacks, making their protection foundational for enterprise security.
Effective endpoint security solutions incorporate multilayered defenses, including behavioral analysis, machine learning, and threat intelligence, to counter evolving cyber threats.
Understanding Endpoints in Cybersecurity
In the context of cybersecurity, an endpoint is any device that can connect to a network and exchange information. These devices represent the outer perimeter of a network, often serving as the initial point of compromise for cyberattacks.
Endpoints encompass a wide array of devices:
- Workstations: Desktops and laptops used by employees.
- Servers: Physical or virtual machines hosting applications and data.
- Mobile Devices: Smartphones and tablets.
- Internet of Things (IoT) Devices: Connected sensors, cameras, and industrial control systems.
- Cloud Workloads: Virtual machines and containers running in cloud environments.
Each endpoint represents a potential vulnerability. Securing these individual access points is crucial for preventing malicious actors from gaining unauthorized access to sensitive data or disrupting operations.
Why Endpoint Security Antivirus is Crucial for Modern Cybersecurity
In today's interconnected world, endpoint security antivirus is a fundamental necessity for any comprehensive cybersecurity strategy. Without strong endpoint defenses, a single compromised device can become a gateway, allowing attackers to access sensitive data, disrupt operations, and compromise an entire network.
Protecting Against Evolving Threats
The threat landscape is constantly evolving, with new forms of malware and attack techniques emerging daily. Traditional antivirus, while still important, is often insufficient on its own. Modern endpoint security solutions move beyond signature-based detection to proactively identify and block unknown threats, including zero-day exploits and fileless malware. This adaptability is critical in staying ahead of cyber adversaries who continually refine their attack methods.
Safeguarding Sensitive Data
Endpoints often store or access sensitive information, including intellectual property, financial records, and personal customer data. A breach at the endpoint level can result in significant data loss, regulatory fines, reputational damage, and a loss of customer trust. Endpoint security antivirus acts as the first line of defense, encrypting data, controlling access, and preventing unauthorized exfiltration of critical information.
Ensuring Business Continuity
Malware infections and cyber attacks can severely disrupt business operations, leading to system downtime, reduced productivity, and significant financial losses. By preventing successful attacks at the endpoint, these solutions help maintain operational continuity. They ensure that employees can work securely and efficiently, protecting the organization from costly interruptions and enabling a quicker recovery from any security incidents that might occur.
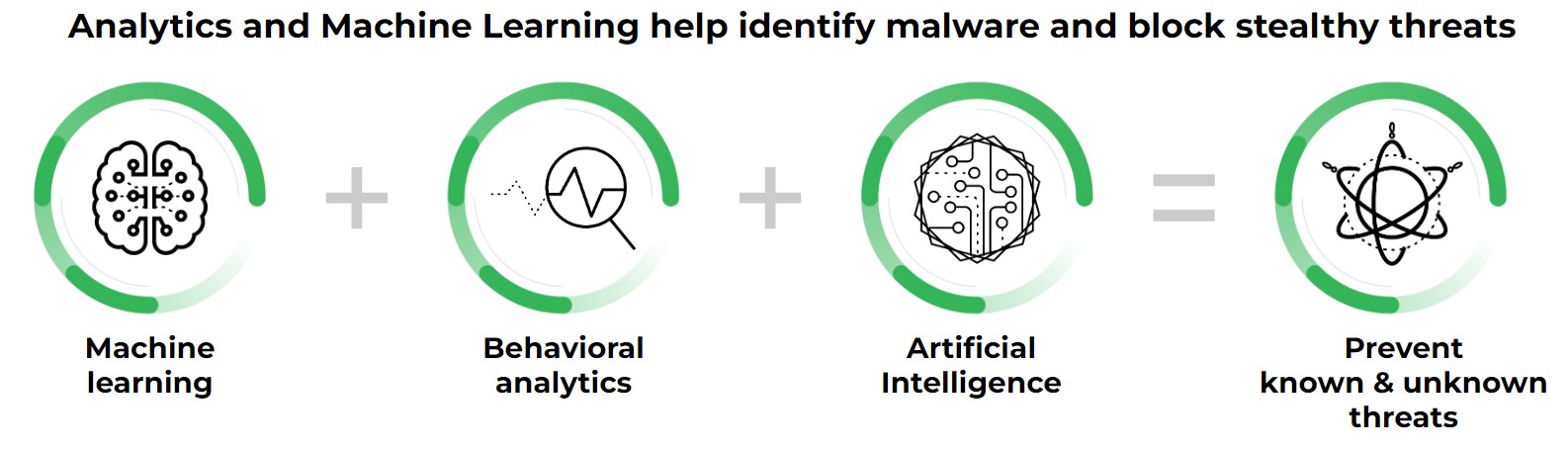
Figure 2: Analytics and machine learning help identify malware and block stealthy threats.
Endpoint Antivirus vs. Endpoint Security: What Is the Difference?
The terms "antivirus" and "endpoint security" are often used interchangeably, but they represent distinct, though related, concepts within cybersecurity. Understanding this difference is crucial for implementing effective protection measures. While traditional antivirus is a component of endpoint security, it does not offer the comprehensive protection required for modern threats.
Traditional Antivirus: A Foundational Layer
Traditional antivirus software is designed to detect, prevent, and remove malicious software, such as viruses, worms, and Trojans, on individual devices. It primarily relies on signature-based detection, comparing files and processes against a database of known malware signatures.
While effective against widespread, known threats, it often struggles with new or polymorphic malware variants that lack existing signatures. It typically operates as a standalone solution for a single device, with limited centralized management capabilities.
The Evolution to Endpoint Protection Platforms (EPPs)
Endpoint security has evolved from simple antivirus to a comprehensive platform known as an Endpoint Protection Platform (EPP). An EPP integrates various security technologies into a single, centrally managed solution. This shift reflects the need for a more holistic defense against sophisticated attacks that can bypass traditional antivirus. EPPs provide enterprise-wide visibility and control, allowing IT and security teams to monitor, manage, and secure numerous devices from a unified console.
Beyond Signatures: Next-Generation Antivirus (NGAV)
A key advancement within endpoint security is next-generation antivirus (NGAV). Unlike traditional antivirus, NGAV employs advanced techniques such as machine learning, artificial intelligence, behavioral analysis, and exploit prevention to detect and block both known and unknown threats.
NGAV can identify suspicious activities and patterns that indicate a new or emerging attack, even without a specific signature. This proactive approach significantly enhances protection against sophisticated and fileless malware that traditional methods often miss.
Figure 3: Cortex XDR Capabilities
Key Components of a Comprehensive Endpoint Security Solution
An extensive endpoint security solution provides comprehensive protection against diverse cyber threats by integrating multiple technologies. These components operate in unison to prevent, detect, investigate, and respond to security incidents at the endpoint level, forming a layered defense.
Endpoint Detection and Response (EDR)
Endpoint Detection and Response (EDR) tools go beyond prevention by continuously monitoring endpoint activity and collecting data on security events. EDR solutions provide deep visibility into what is happening on devices, allowing security teams to detect advanced threats that may have bypassed initial defenses.
They offer capabilities for incident data search and investigation, alert triage, threat hunting, and automated response actions, enabling rapid containment and remediation of active threats. This proactive monitoring and response capability is critical for identifying and mitigating silent failures, where attackers might dwell undetected within a network.
Data Loss Prevention (DLP)
DLP is a crucial component that prevents sensitive data from leaving the organization's control, whether intentionally or accidentally. Endpoint DLP solutions monitor, detect, and block the unauthorized transmission of sensitive information through various channels, such as email, cloud storage, USB drives, and web applications.
This helps organizations comply with data privacy regulations and protect intellectual property. For example, organizations have observed a significant reduction in sensitive data exfiltration attempts after deploying comprehensive DLP measures, with some reporting a 40% decrease in such incidents within the first year of implementation.
Firewall and Intrusion Prevention Systems (IPS)
Endpoint firewalls control network traffic to and from individual devices, blocking unauthorized access and preventing malicious connections. They act as a personalized perimeter defense for each endpoint.
Intrusion prevention systems (IPS), often integrated with firewalls, monitor network traffic for suspicious patterns or known attack signatures and can automatically block or alert on detected intrusions. These tools add an essential layer of network-level protection directly at the endpoint.
Device Control and Management
Device control features enable organizations to manage and restrict the use of external devices, such as USB drives, ensuring that only authorized devices can connect to endpoints. This prevents data theft and the introduction of malware through removable media.
Centralized device management also enables consistent policy enforcement, software deployment, and patch management across all endpoints, thereby significantly reducing the attack surface.
Cloud-Based Management and Scalability
Many modern endpoint security solutions leverage cloud-based management consoles. This provides a centralized platform for administrators to oversee security policies, monitor threats, and manage devices regardless of their location.
Cloud-based solutions offer significant advantages in terms of scalability, allowing organizations to easily expand their protection to a growing number of endpoints, including those used by remote and hybrid workforces. This approach also reduces the on-premises infrastructure burden and ensures that security definitions and updates are delivered efficiently.
How Endpoint Security Antivirus Works
Endpoint security antivirus functions as a proactive defense mechanism, meticulously inspecting and analyzing digital activities on devices to detect and neutralize cyber threats. It establishes a dynamic shield, constantly adapting its methods to protect against the ever-evolving landscape of malicious software and attack techniques.
Multi-Layered Threat Detection
The core of endpoint security antivirus lies in its ability to detect threats using multiple methods. This includes:
- Signature-Based Detection: This traditional method scans files and processes for known malware signatures, matching them against a regularly updated database. It remains effective against common, established threats.
- Behavioral Analysis: This technique monitors the behavior of applications and processes for suspicious activities, such as attempts to modify critical system files, unusual network connections, or unauthorized access to sensitive data. It can identify new or unknown malware by its actions rather than its signature.
- Machine Learning and Artificial Intelligence (AI): AI and machine learning algorithms analyze vast amounts of data to identify complex patterns indicative of malicious activity. These advanced capabilities enable solutions to detect polymorphic malware, fileless attacks, and zero-day threats that traditional methods might miss. By leveraging AI, endpoint security can often identify threats before they fully execute, providing a proactive defense.
Real-Time Monitoring and Analysis
Endpoint security solutions continuously monitor all activities on a device, from file access and process execution to network connections and user behavior. This real-time monitoring generates a stream of data that is then analyzed for anomalies or indicators of compromise (IoCs). Advanced analytics engines process this data to identify threats, often correlating events across multiple endpoints to detect more complex, coordinated attacks. This constant vigilance allows for immediate detection and response.
Automated Response and Remediation
Upon detecting a threat, endpoint security antivirus can initiate automated response actions to contain and neutralize the malicious activity. These actions may include:
- Quarantining: Isolating infected files or processes to prevent them from causing further harm.
- Blocking: Preventing malicious executables, URLs, or network connections from operating.
- Rollback: Reverting system changes made by malware to restore the endpoint to a clean state.
- Alerting: Notifying security teams of detected threats, providing detailed context for further investigation. This automation significantly reduces the time it takes to respond to incidents, thereby minimizing potential damage and workload for security personnel.
Implementing and Optimizing Endpoint Security Antivirus
Effective implementation and ongoing optimization are crucial for maximizing the protective capabilities of an endpoint security antivirus solution. A strategic approach ensures consistent security across all devices and adapts to evolving threats.
Centralized Management and Policy Enforcement
Centralized management is a cornerstone of modern endpoint security. It involves deploying and managing security policies, updates, and monitoring across all endpoints from a single console. This streamlined approach:
- Ensures consistency in security posture.
- Reduces administrative overhead.
- Allows for rapid deployment of new protections or responses to emerging threats.
Policies can be tailored to different user groups or device types, enforcing appropriate levels of security while maintaining operational flexibility. Organizations that implement comprehensive, centralized policy management report a 25% increase in their ability to respond quickly to endpoint-related security incidents.
Regular Updates and Patch Management
Keeping endpoint security software, operating systems, and applications consistently up to date is paramount. Software updates often include patches for newly discovered vulnerabilities that attackers could exploit. Automated patch management systems ensure that all endpoints receive necessary security updates promptly, significantly reducing the attack surface. Regular updates to antivirus signatures and machine learning models are also vital for detecting the latest threats.
Integration with Broader Security Frameworks
For maximum effectiveness, endpoint security antivirus should not operate in isolation. Integrating it with other security solutions, such as Security Information and Event Management (SIEM) systems, threat intelligence platforms, and network access control (NAC) solutions, creates a more cohesive and resilient security ecosystem.
This integration provides a unified view of security events, enhances threat correlation, and facilitates automated responses across the entire infrastructure, thereby improving overall security visibility and response capabilities.
Deployment Strategies
The method of deployment can significantly impact the success of the rollout and user experience.
- Phased Rollout: Implement the solution in stages, starting with a pilot group (e.g., the IT department or a specific team) to identify and resolve issues before deploying it more broadly.
- Pilot Programs: Test the solution on a small, representative set of endpoints to validate performance, compatibility, and efficacy in the organization's specific environment.
- On-Premises vs. Cloud-Based: Decide whether to host the management server on-site or leverage a cloud-based solution. Cloud-based options typically offer easier scalability and maintenance.
- Automated Deployment: Utilize existing endpoint management tools (e.g., SCCM, Intune, GPO) for automated agent deployment across the enterprise, minimizing manual effort.
Choosing the Right Endpoint Security Antivirus Solution
Selecting an endpoint security solution requires careful consideration of an organization's unique needs, threat landscape, and operational environment. The ideal solution provides comprehensive protection without imposing excessive management overhead or impacting user productivity.
Category |
Description |
Key Considerations |
|---|---|---|
Alignment with Business Needs and Risk Profile |
The chosen endpoint security solution must align with the organization's specific requirements and risk appetite. |
|
Industry and Compliance |
Different industries have varying regulatory requirements. |
Ensure the solution supports compliance with standards relevant to your sector (e.g., HIPAA for healthcare, PCI DSS for retail). |
Organizational Size and Complexity |
The solution should scale effectively for businesses of all sizes, from small to large enterprises with thousands of distributed endpoints. |
Consider its ability to manage diverse operating systems (Windows, macOS, Linux) and mobile devices. |
Critical Assets and Data |
Prioritize solutions that offer advanced protection for endpoints hosting sensitive data or critical business applications. |
|
Budgetary Constraints |
Evaluate the total cost of ownership (TCO). |
This includes licensing, deployment, training, and ongoing management to ensure it fits within the allocated cybersecurity budget. |
Table: How to Choose the Right Endpoint Security Antivirus Solution
Alignment with Business Needs and Risk Profile
The chosen solution must align with the organization's specific requirements and risk appetite.
- Industry and Compliance: Different industries have varying regulatory requirements. Ensure the solution supports compliance with standards relevant to your sector (e.g., HIPAA for healthcare, PCI DSS for retail).
- Organizational Size and Complexity: The solution should scale effectively, whether for a small business or a large enterprise with thousands of distributed endpoints. Consider whether it can manage diverse operating systems (Windows, macOS, Linux) and mobile devices.
- Critical Assets and Data: Prioritize solutions that offer advanced protection for endpoints hosting sensitive data or critical business applications.
- Budgetary Constraints: Evaluate the total cost of ownership (TCO), including licensing, deployment, training, and ongoing management, to ensure it fits within the allocated cybersecurity budget.
Challenges and Future Trends in Endpoint Security
The landscape of cybersecurity is ever-changing, presenting ongoing challenges for endpoint security while also driving innovation and new trends.
Combating Advanced Persistent Threats (APTs)
Advanced Persistent Threats (APTs) pose a significant challenge because they are designed to evade detection over long periods, often using sophisticated techniques and zero-day exploits. Endpoint security solutions must continually evolve to combat these highly targeted and stealthy attacks.
This involves leveraging advanced analytics, behavioral monitoring, and threat intelligence to identify subtle indicators of compromise that signify an APT in progress, rather than relying solely on signature-based detection.
Securing Remote and Hybrid Workforces
The widespread adoption of remote and hybrid work models has dramatically expanded the attack surface, making endpoint security more critical than ever.
Employees working from various locations and often using personal devices introduce new vulnerabilities. Endpoint security solutions must provide solid protection regardless of network location, offering secure access, data encryption, and centralized management for devices outside the traditional corporate perimeter. This includes protecting against unsecured home networks and public Wi-Fi risks.
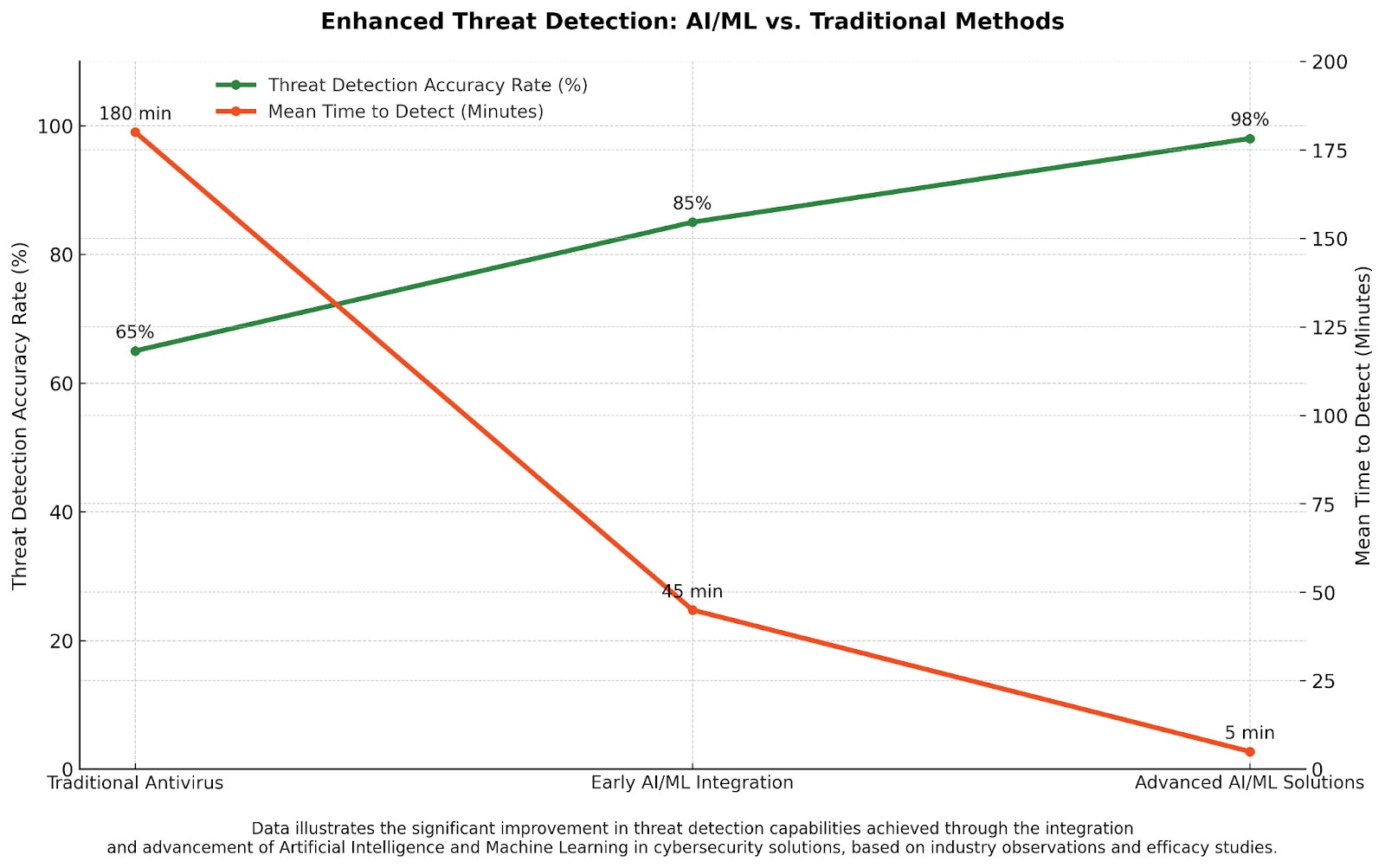
Figure 4: The significant improvement in threat detection capabilities achieved through the integration and advancement of AI and ML based on industry observations and efficacy studies.
The Role of AI and Machine Learning
The future of endpoint security is heavily reliant on AI and ML. These technologies are continuously being refined to enhance threat detection, improve anomaly detection, and automate response actions.
AI and ML enable endpoint security solutions to adapt to new attack vectors, analyze vast amounts of data in real time, and predict potential threats with greater accuracy. They are instrumental in moving endpoint security from a reactive to a proactive approach, empowering systems to identify and neutralize threats at unprecedented speeds.
Over the past two years, advancements in AI and ML have led to a 110% increase in the detection rate of previously unknown threats in some endpoint protection platforms, highlighting the transformative impact of these technologies.
Endpoint Security Antivirus FAQs
Traditional antivirus primarily focuses on detecting and removing known malware signatures on a single device. Modern endpoint security, or Endpoint Protection Platforms (EPPs), offers a more comprehensive, multi-layered approach that includes advanced threat detection (like NGAV and EDR), data loss prevention, centralized management, and protection against both known and unknown threats across an entire network of devices.
Businesses face sophisticated threats like ransomware, fileless attacks, and advanced persistent threats (APTs) that traditional antivirus often cannot detect. Endpoint security provides a broader defense by integrating various tools, offering centralized management, and enabling real-time monitoring and response across all devices, crucial for protecting sensitive data and maintaining business operations.
Next-Generation Antivirus (NGAV) is an advanced form of antivirus that uses technologies like machine learning, artificial intelligence, and behavioral analysis to detect and prevent malware. Unlike traditional signature-based antivirus, NGAV can identify and block new and unknown threats by analyzing their characteristics and behaviors, rather than relying solely on predefined signatures.
Yes, modern endpoint security solutions are designed with multiple layers of protection against ransomware. They employ behavioral analysis to detect ransomware activities, such as unauthorized file encryption, and can often quarantine or roll back affected files to prevent widespread damage. Many solutions also include anti-ransomware features to block known and unknown variants.
Absolutely. With the rise of remote and hybrid work, endpoint security is more critical than ever. Cloud-based endpoint security solutions provide centralized management and continuous protection for devices regardless of their location, ensuring that remote workers' devices are secured against threats even when they are outside the traditional corporate network.
