What Is Identity Threat Detection and Response (ITDR)?
Identity Threat Detection and Response (ITDR) is a cybersecurity framework and set of capabilities designed to protect identity and access infrastructure from cyber attacks. ITDR solutions actively monitor, detect, and respond to threats targeting user accounts, privileged credentials, and identity systems, safeguarding an organization's critical access pathways.
- With cloud adoption and remote work dissolving traditional perimeters, digital identities have become the primary control plane—and the most targeted vector in cyberattacks.
- Unlike IAM (which focuses on access control) or SIEM/XDR (which provide broad visibility), ITDR delivers deep, real-time insights and responses specifically for identity-based threats.
- ITDR uses AI/ML to detect anomalies in user behavior, helping identify sophisticated attacks like insider threats, lateral movement, and credential misuse that bypass traditional defenses.
- ITDR enables rapid detection and automated response—such as account isolation, access revocation, and step-up authentication—to stop identity threats before they escalate.
- ITDR will evolve to support Zero Trust Architecture, passwordless authentication, identity fabric, and quantum-resistant cryptography—ensuring identity security keeps pace with new technologies and threats.
Understanding ITDR
ITDR plays a critical role in modern cybersecurity. It focuses on how compromised identities pose a direct threat to an organization's digital assets, emphasizing proactive defense over reactive measures.
The Shifting Perimeter—Identity as the New Control Plane
Traditional cybersecurity models centered on network perimeters. Today, cloud adoption, remote work, and hybrid environments have dissolved these boundaries, elevating identity to the primary control plane. Users access resources from diverse locations and devices, making their identities—and the systems managing them—the most critical points of vulnerability. ITDR recognizes this fundamental shift, prioritizing the protection of digital identities as the foundation of secure operations.
Why Identity-Based Attacks Predominate
Attackers increasingly target identities because compromised credentials offer a direct, legitimate pathway into an organization’s systems, often bypassing other security layers. They understand that it is often simpler to steal or manipulate a valid identity than to breach a hardened network firewall. ITDR directly confronts this reality by providing specialized tools and processes designed to detect and respond to these identity-centric attacks, which form the entry point for most major breaches.
Bridging Security Gaps with ITDR
Many organizations rely on a patchwork of security solutions, leaving gaps in identity protection. ITDR integrates with existing security tools, such as Identity and Access Management (IAM) and Privileged Access Management (PAM) systems, to create a cohesive defense. This integration provides a holistic view of identity activity across the entire digital estate. It closes blind spots by correlating data from various sources, ensuring that anomalous behavior, whether in a cloud application or an on-premises directory, triggers immediate alerts and automated responses.
ITDR vs Other Security Concepts (IAM, XDR, SIEM)
Identity Threat Detection and Response (ITDR) often overlaps with other cybersecurity functions, but it maintains a distinct focus. Understanding its unique role compared to Identity and Access Management (IAM), Extended Detection and Response (XDR), and Security Information and Event Management (SIEM) clarifies its critical contribution to enterprise security.
ITDR versus Identity and Access Management (IAM)
IAM focuses on prevention—managing who has access to what. It enforces policies such as multi-factor authentication and role-based controls, aiming to prevent unauthorized access before it occurs. ITDR focuses on detection and response—it assumes identities can be compromised despite IAM.
ITDR actively monitors for misuses of legitimate credentials, privilege escalation, and lateral movement by attackers. It acts as a crucial safety net, catching threats that bypass preventive IAM measures.
ITDR versus Extended Detection and Response (XDR)
XDR offers a broad, unified approach to threat detection and response across diverse security layers: endpoints, networks, cloud, email, and identity. It correlates telemetry from these sources for comprehensive visibility.
ITDR is a specialized component within XDR. While XDR provides a wide lens, ITDR offers deep, granular insights into identity-centric threats. ITDR’s specialized identity data enhances XDR's ability to identify complex, multi-stage attacks where identity compromise is a central component.
ITDR versus Security Information and Event Management (SIEM)
SIEM platforms aggregate and analyze log data from nearly all IT and security systems, providing a centralized view for compliance and broad threat detection. ITDR differs in its specialized analytical depth for identity.
While SIEMs ingest identity logs, ITDR solutions are purpose-built to analyze identity-specific data—like authentication flows and directory changes—with sophisticated behavioral analytics. ITDR provides high-fidelity identity threat detections that a SIEM can then integrate to create a more comprehensive security picture.
“With the addition of ITDR, the XSIAM platform now integrates all identity data sources into a single security data foundation spanning endpoints, networks and cloud. This allows our customers to run comprehensive AI-driven threat detection to protect against stealthy identity-driven attacks.”
~Gonen Fink (Senior Vice President of Cortex Products at Palo Alto Networks)
Key Components of ITDR
ITDR solutions are built upon several core components that collectively enable their ability to monitor, detect, and respond to identity-based threats. These components work in concert to provide a comprehensive defense for an organization's identity infrastructure.
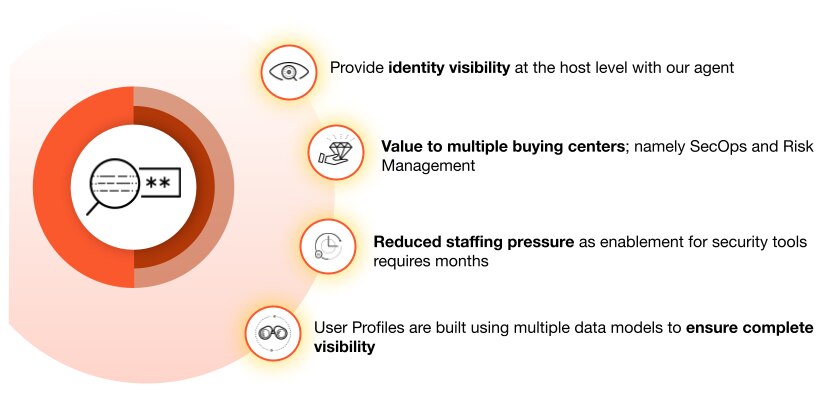
Continuous Identity Visibility and Monitoring
Effective ITDR begins with pervasive, real-time visibility into all identity-related activities across the entire IT landscape—on-premises, in the cloud, and across hybrid environments. This includes monitoring authentication attempts, access requests, privilege changes, directory modifications (e.g., Active Directory, Azure AD), and user behavior across applications and systems. It encompasses both human and non-human identities, such as service accounts and OAuth tokens, ensuring no identity goes unobserved.
Behavioral Analytics and Anomaly Detection
A cornerstone of ITDR, behavioral analytics establishes a baseline of normal identity behavior. It leverages machine learning (ML) and artificial intelligence (AI) to analyze patterns in user activity, such as login times, locations, device usage, and resource access.
Any significant deviation from this established baseline—like an unusual login from a new country, an attempt to access highly sensitive data outside regular working hours, or rapid privilege escalation—triggers an alert as a potential anomaly. This capability is crucial for identifying sophisticated attacks that might otherwise appear legitimate.
Threat Intelligence Integration
ITDR solutions integrate with external and internal threat intelligence feeds. This includes information on known attack techniques, indicators of compromise (IOCs) related to identity theft, and emerging identity-based threats. By correlating observed identity activity with threat intelligence, ITDR can identify known malicious patterns and prioritize threats, enabling faster and more informed responses.
Identity Security Posture Management (ISPM)
Beyond just detecting threats, ITDR solutions often include capabilities for assessing and managing the security posture of the identity infrastructure itself. This involves continuously identifying misconfigurations, excessive permissions, shadow IT identities, and other vulnerabilities that attackers could exploit. ISPM helps proactively harden identity systems, reducing the overall attack surface and minimizing the likelihood of successful identity-based attacks.
Automated and Manual Response Capabilities
Upon detecting a threat, ITDR facilitates rapid response. This can include automated actions like:
- Enforcing step-up authentication (e.g., requiring MFA) for suspicious logins.
- Temporarily blocking or disabling compromised accounts.
- Revoking suspicious sessions or access tokens.
- Isolating affected systems or users.
- Automatically resetting passwords.
In addition to automation, ITDR provides security teams with the necessary context and tools for manual investigation and remediation, such as detailed logs, forensic data, and guided workflows to contain and eradicate complex threats.
Integration with Existing Security Ecosystems
For maximum effectiveness, ITDR solutions integrate seamlessly with an organization's broader security stack. This includes feeding high-fidelity identity alerts to SIEMs for correlation with other security data, sharing context with XDR platforms for holistic threat investigation, and working with IAM and PAM systems to enforce and update access policies based on real-time threat intelligence. This interoperability ensures that identity security is a cohesive part of the overall cybersecurity strategy.
Implementing Effective ITDR Strategies
Successful ITDR implementation requires strategic planning, comprehensive tooling, and ongoing operational commitment. Organizations must strike a balance between security effectiveness and operational efficiency while maintaining user productivity.
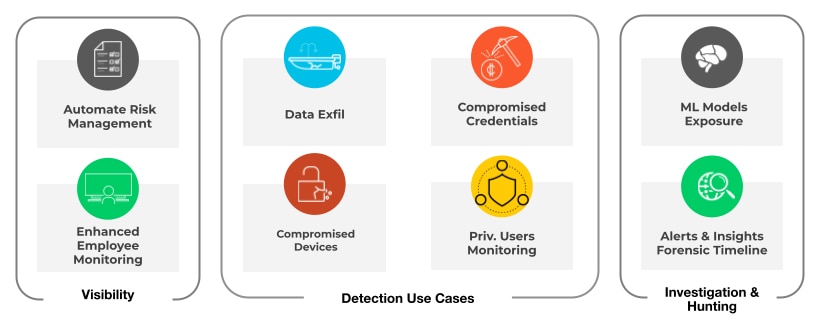
Developing a Comprehensive Cybersecurity Strategy
A strong cybersecurity strategy hinges on several key elements:
- Risk Assessment: This foundational step involves pinpointing critical assets, high-value accounts, and possible attack routes. Understanding the organization's specific risk landscape is crucial for effective resource allocation and prioritizing security measures.
- Integration Planning: ITDR solutions should integrate smoothly with the current security setup. Successful deployments utilize data from various sources, including network security tools, endpoint protection, and identity management, to achieve broad threat visibility.
- Policy Development: Establishing clear guidelines for acceptable use, access protocols, and incident response is essential. Well-defined policies enable automated systems to distinguish between regular activity and potential threats, while also guiding the security team's actions.
- Stakeholder Alignment: Collaboration among IT, security, HR, and business executives is crucial for developing effective governance structures and response plans. This cross-departmental approach ensures ITDR efforts support business goals while upholding necessary security standards.
Solutions for Managing Identity Threats
Effective ITDR relies on sophisticated capabilities that automate responses, streamline investigations, prioritize risks, and maintain continuous oversight of identity-related activities. These features enable security teams to manage the dynamic landscape of identity threats efficiently.
Automated Response Capabilities
Automated response functions enable rapid threat containment without requiring immediate human intervention. Systems can automatically disable suspicious accounts, enforce additional authentication requirements, or restrict access to sensitive resources. This swift action helps to limit an attacker's window of opportunity while security teams investigate potential incidents.
Investigation Workflows
Streamlined investigation workflows simplify the process of analyzing security alerts and performing forensic analysis. Integrated platforms provide security analysts with crucial context, relevant historical data, and recommended actions. This information helps accelerate incident response activities and ensures a more thorough understanding of the threat.
Risk Scoring Mechanisms
Risk scoring mechanisms prioritize security alerts based on their potential impact and the likelihood of a successful attack. These scoring systems help security teams focus attention on the most critical threats, effectively managing alert fatigue and optimizing resource allocation.
Continuous Monitoring Frameworks
Continuous monitoring frameworks deliver ongoing visibility into identity-related activities across the entire IT environment. Comprehensive monitoring covers authentication events, permission changes, data access patterns, and administrative activities. This constant oversight enables organizations to detect anomalous behavior as it occurs, providing a resilient defense against evolving identity threats.
Enhancing Security Posture through Visibility and Monitoring
Effective Identity Threat Detection and Response (ITDR) significantly enhances an organization's security posture by providing unparalleled visibility and robust monitoring capabilities. These tools transform raw data into actionable intelligence, enabling swift identification and remediation of identity-based threats.
Centralized Dashboards
Centralized dashboards aggregate identity security metrics and threat indicators into unified, easy-to-assess interfaces. Effective dashboards highlight critical alerts, trend analysis, and key performance indicators, providing a clear overview without overwhelming security teams with excessive detail. This consolidation enables security professionals to assess their current identity security standing quickly.
Forensic Capabilities
Comprehensive forensic capabilities enable detailed investigation of security incidents through comprehensive logging and extensive data retention. Analysts can reconstruct attack timelines, identify affected systems, and determine the scope of potential compromises. These features are vital for understanding how breaches occurred and for ensuring the complete eradication of threats.
Compliance Reporting
ITDR solutions generate essential documentation for regulatory requirements and internal governance processes. Automated reporting capabilities reduce administrative overhead, enabling organizations to demonstrate adherence to various security standards and frameworks. This streamlines audit preparations and proves due diligence in protecting identities.
Performance Metrics
Tracking performance metrics allows organizations to measure the effectiveness of their ITDR implementations. Measurable indicators include detection rates, response times, and false favorable ratios. Regular assessment of these metrics enables continuous improvement of security operations, ensuring the ITDR strategy remains optimized and responsive to evolving threats.
Identity-Based Attacks: Challenges and Solutions
Identity-based attacks present unique challenges that require specialized approaches and dedicated resources. Organizations must overcome technical, operational, and organizational obstacles to implement effective identity threat protection.
Common Identity-Based Threats
Credential stuffing attacks: exploit reused passwords across multiple services by testing large volumes of username-password combinations against target systems. Attackers leverage credential databases from previous breaches to gain unauthorized access to organizational resources.
Phishing campaigns: target users with sophisticated social engineering techniques designed to steal credentials or trick users into installing malware. Modern phishing attacks frequently impersonate trusted services, utilize legitimate-looking domains, and incorporate personalized content to enhance their success rates.
Privilege escalation: involves attackers who have gained initial access attempting to obtain higher-level permissions within target systems. Successful privilege escalation enables attackers to access sensitive data, modify system configurations, and establish persistent access mechanisms.
Account takeover: occurs when attackers gain complete control of legitimate user accounts through various mean, including credential theft, session hijacking, or exploitation of authentication vulnerabilities. Compromised accounts provide attackers with legitimate access paths that bypass many traditional security controls.
Malicious insider activities: encompass a range of threats from current or former employees who abuse their authorized access privileges. Insider threats can involve data theft, sabotage, fraud, or unauthorized disclosure of sensitive information.
Overcoming Challenges in Identity Protection
Implementing and maintaining strong ITDR faces common hurdles. Organizations must address challenges such as alert fatigue, false positives, scalability, and skill shortages to realize the benefits of their ITDR investments fully.
Alert Fatigue
Security teams often grapple with overwhelming volumes of alerts, leading to alert fatigue and potentially missed genuine threats. Advanced ITDR solutions combat this through intelligent alert prioritization, automated triage capabilities, and risk-based scoring. This approach enables analysts to focus their attention on the most critical threats, thereby improving operational efficiency and response times.
False Positive Reduction
Minimizing false positives—i.e., benign activities incorrectly flagged as malicious—is crucial for maintaining trust in ITDR systems and preventing unnecessary investigations. This requires sophisticated analytics engines that deeply understand normal business operations and user behaviors. Machine learning algorithms continuously refine detection capabilities, reducing noise while maintaining sensitivity to actual security threats.
Scalability Concerns
As organizations expand and their identity infrastructures grow increasingly complex, scalability concerns become prominent. Cloud-native ITDR platforms address this by providing the necessary scalability to monitor large user populations and distributed IT environments without experiencing performance degradation. These platforms adapt to changing demands, ensuring consistent protection.
Skills Shortage
The widespread cybersecurity skills shortage impacts many organizations trying to implement and operate advanced security technologies. To overcome these staffing constraints, organizations can leverage managed ITDR services or platforms with built-in intelligence. These solutions offer expert-level detection and response capabilities, eliminating the need for extensive in-house expertise and bridging the talent gap.
Case Studies: Successful ITDR Implementations
Real-world applications demonstrate the tangible benefits of a well-executed ITDR strategy. These examples highlight how ITDR directly safeguards critical assets and prevents potentially catastrophic security incidents.
Financial Services Organization
A major financial services organization implemented comprehensive ITDR to protect sensitive customer data and ensure regulatory compliance. Their ITDR solution successfully detected a sophisticated insider threat involving unauthorized access to customer financial records. This proactive detection prevented a significant data breach, avoiding substantial regulatory penalties and severe reputational damage.
Healthcare System
A large healthcare system deployed ITDR technologies to secure electronic health records and protect patient privacy. The ITDR system identified anomalous access patterns that revealed staff members were unauthorizedly viewing celebrity patient records. This detection enabled swift corrective action, effectively preventing potential HIPAA violations and maintaining patient trust.
Technology Company
A leading technology company utilized ITDR solutions to safeguard its intellectual property and critical development environments. The ITDR platform detected suspicious file access patterns indicating a compromised developer account was actively stealing proprietary source code. Security teams contained the incident before significant data loss occurred, protecting vital company assets.
Future Trends in Identity Threat Detection and Response
Identity security continues evolving as organizations adopt new technologies and attackers develop more sophisticated techniques. Future ITDR capabilities will need to address emerging challenges while leveraging advanced technologies to improve detection and response effectiveness.
Emerging Technologies in ITDR
Several key technological advancements will shape the future of ITDR, pushing its capabilities further into proactive and adaptive defense.
Zero Trust Architecture
Zero Trust Architecture fundamentally changes how organizations approach identity security. It eliminates implicit trust, requiring continuous verification of user and device identities regardless of their location. ITDR solutions will need to integrate more deeply with Zero Trust frameworks to provide granular access controls and continuous risk assessment based on real-time identity and device posture.
Passwordless Authentication
Passwordless authentication significantly reduces reliance on traditional credentials, utilizing methods such as biometric authentication, hardware tokens, and cryptographic certificates. ITDR platforms must adapt to monitor these new authentication methods effectively. They will need to detect attempts to bypass or compromise passwordless systems, ensuring these advanced methods do not introduce new vulnerabilities.
Identity Fabric
The concept of an identity fabric represents a distributed approach to identity management, spanning multiple environments and platforms. Future ITDR solutions will need to provide seamless visibility and control across complex identity fabrics that encompass on-premises, multicloud, and hybrid environments. This ensures consistent security posture and threat detection regardless of where an identity or resource resides.
Quantum-Resistant Cryptography
As quantum computing capabilities advance, they pose a significant threat to current encryption standards. Quantum-resistant cryptography will become essential to secure communications and data. ITDR systems must prepare for the transition to quantum-resistant algorithms while maintaining compatibility with existing identity infrastructure. This proactive approach will safeguard identity systems against future cryptographic attacks.
The Role of AI and Machine Learning in Enhancing ITDR
AI and machine learning (ML) are not just buzzwords in Identity Threat Detection and Response (ITDR)—they are fundamental to its evolution. These technologies empower ITDR to move beyond traditional, rule-based detection, enabling more sophisticated analysis, predictive capabilities, and rapid, intelligent responses to identity threats.
Advanced Behavioral Analytics
ITDR will leverage increasingly sophisticated AI algorithms for advanced behavioral analytics. These algorithms will detect even the most subtle anomalies in user behavior that might indicate compromise or malicious intent. Deep learning models will analyze complex patterns across multiple data sources, uncovering threats that traditional rule-based systems simply cannot identify. This means catching insider threats and highly disguised external attacks.
Predictive Threat Modeling
AI will enable ITDR systems to perform predictive threat modeling. This allows ITDR to anticipate potential attacks based on environmental factors, current threat intelligence, and historical attack patterns. These predictive capabilities will help organizations implement proactive defenses, shifting from a purely reactive stance to one that anticipates and prepares for identity-based threats before they fully materialize.
Automated Incident Response
As AI systems mature, automated incident response will become far more sophisticated. AI will gain the ability to make complex decisions about threat containment and remediation, dramatically reducing response times. This advanced automation will ensure that appropriate actions are taken based on the specific threat severity and an organization's pre-defined security policies, freeing up human analysts for more complex tasks.
Natural Language Processing
Natural Language Processing (NLP) will significantly improve threat intelligence analysis and incident documentation. NLP will automatically process vast amounts of unstructured data, including security reports, threat feeds, and internal communications. This capability helps ITDR systems quickly identify relevant security information and context, allowing analysts to piece together incident details more efficiently and accurately.
Preparing for Future Cybersecurity Challenges
The cybersecurity landscape continues to evolve rapidly, presenting new challenges for identity protection. ITDR must adapt and expand its scope to address these emerging threats and ensure long-term resilience.
Supply Chain Security
Supply chain attacks are increasingly common, making supply chain security a critical area for ITDR. Future solutions will need to monitor third-party access and vendor activities more closely. Organizations require granular visibility into how external partners and suppliers access their systems and data to detect and prevent compromises originating from extended networks.
IoT and Operational Technology (OT) Integration
The growing integration of IoT and operational technology (OT) will expand the scope of identity security beyond traditional IT environments. This includes industrial control systems, smart devices, and other connected technologies that often have limited inherent security capabilities. ITDR will need to extend its monitoring and response to these devices and the identities associated with them, securing critical infrastructure.
Evolving Regulatory Compliance
Regulatory compliance requirements will continue to evolve as governments implement new privacy and security regulations globally. ITDR platforms must provide the robust documentation and controls needed to demonstrate adherence to emerging regulatory frameworks, such as enhanced data privacy laws or industry-specific mandates. This ensures organizations can prove due diligence in protecting identities and sensitive information.
Skills Development
Skills development will remain critical. Organizations must focus on building internal capabilities for managing advanced identity security technologies. Comprehensive training programs and certification paths will help security professionals develop the essential expertise in ITDR implementation, operation, and incident response, bridging the talent gap in this specialized field.