Vulnerability management
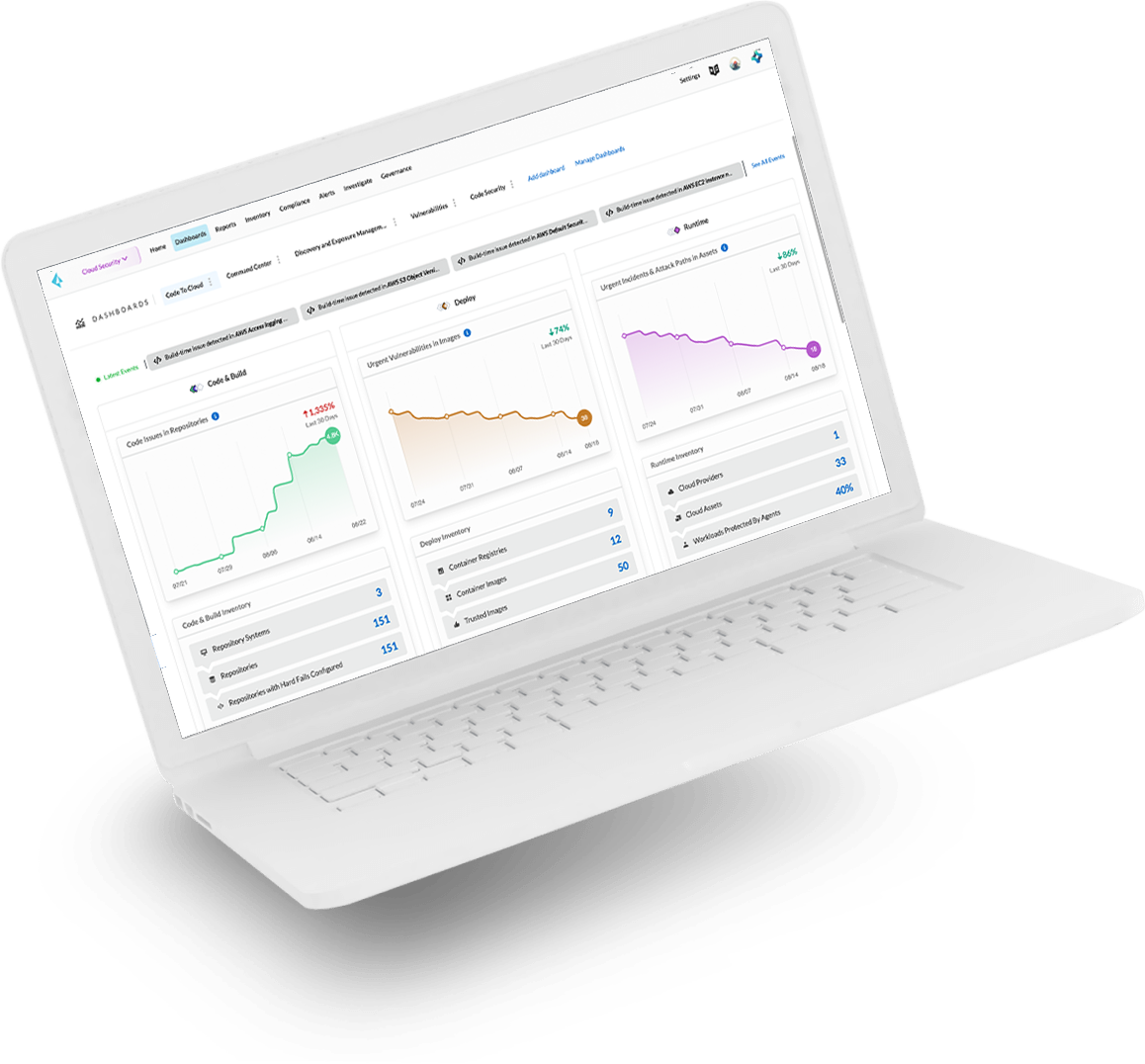
Improve your hygiene and reduce the risk of exposure in your cloud environments by identifying vulnerabilities continuously before and after deployment. Prisma Cloud finds, prioritizes and protects against vulnerabilities in real time from a centralized dashboard.
Build golden pipelines by identifying vulnerable machine images.
Scan VM images prior to deployment to alert on or block vulnerabilities from being deployed.
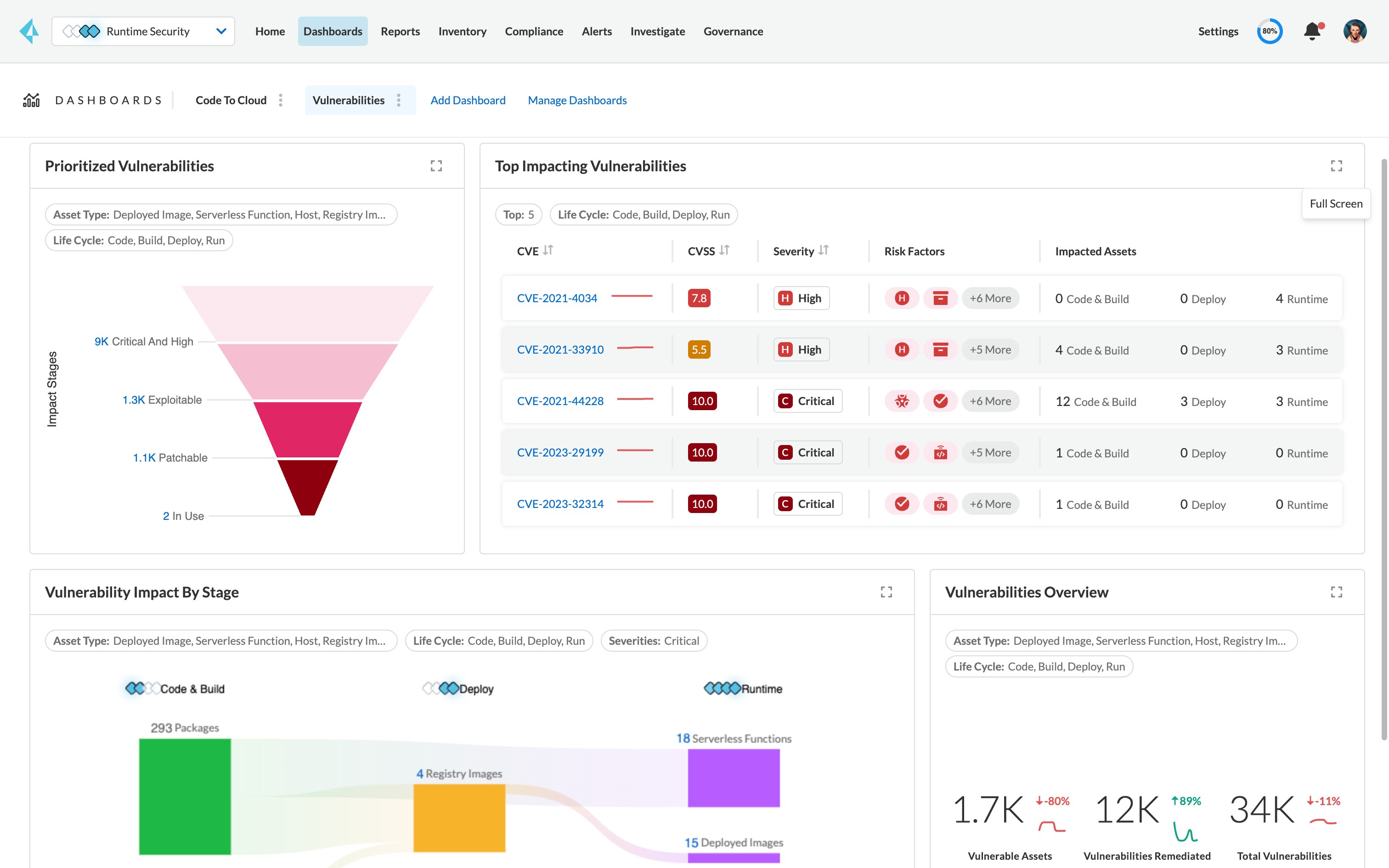
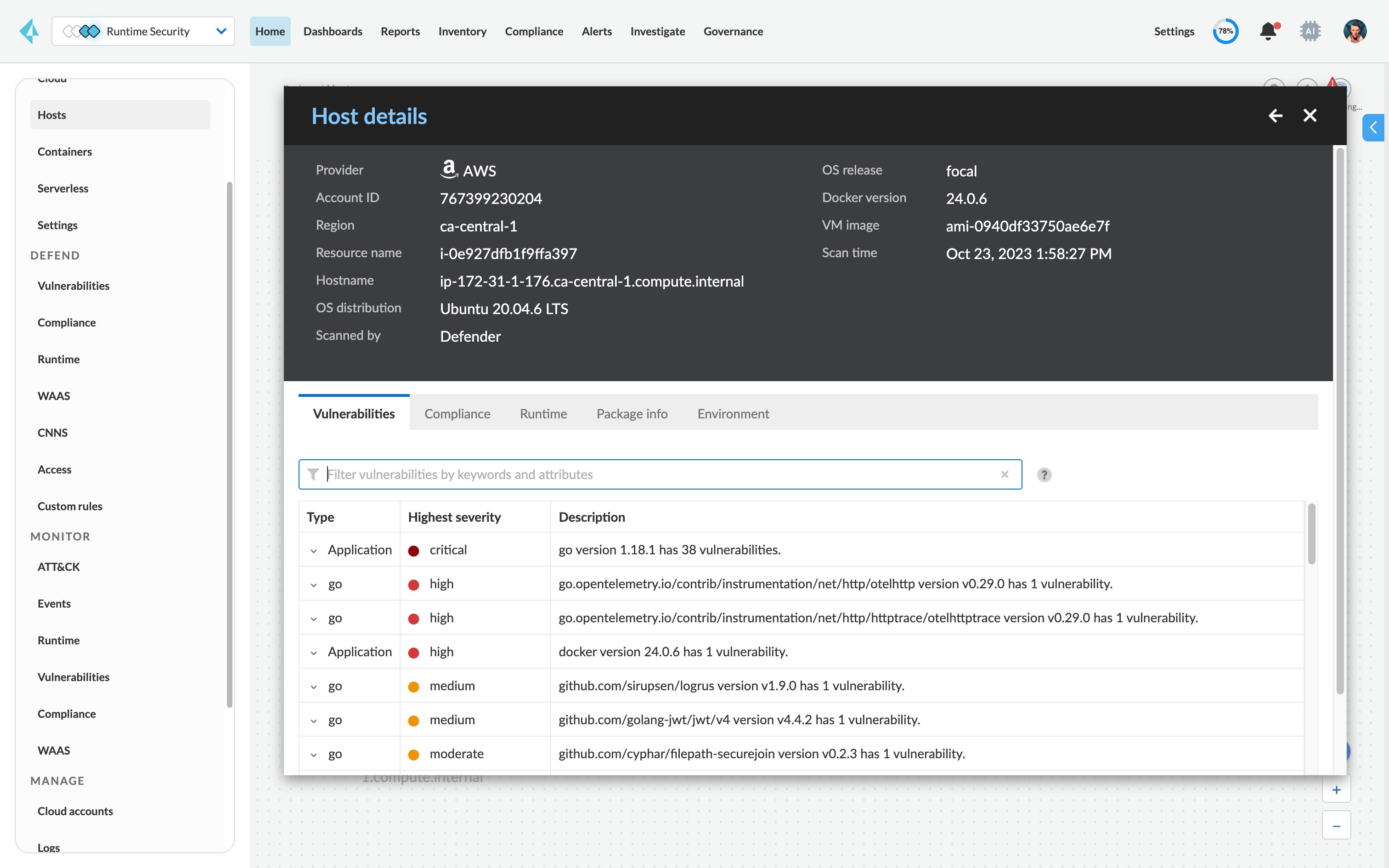
Rank vulnerabilities by risk for prioritization.
Prioritize vulnerabilities based on risk score and risk factors based on your applications’ configurations.
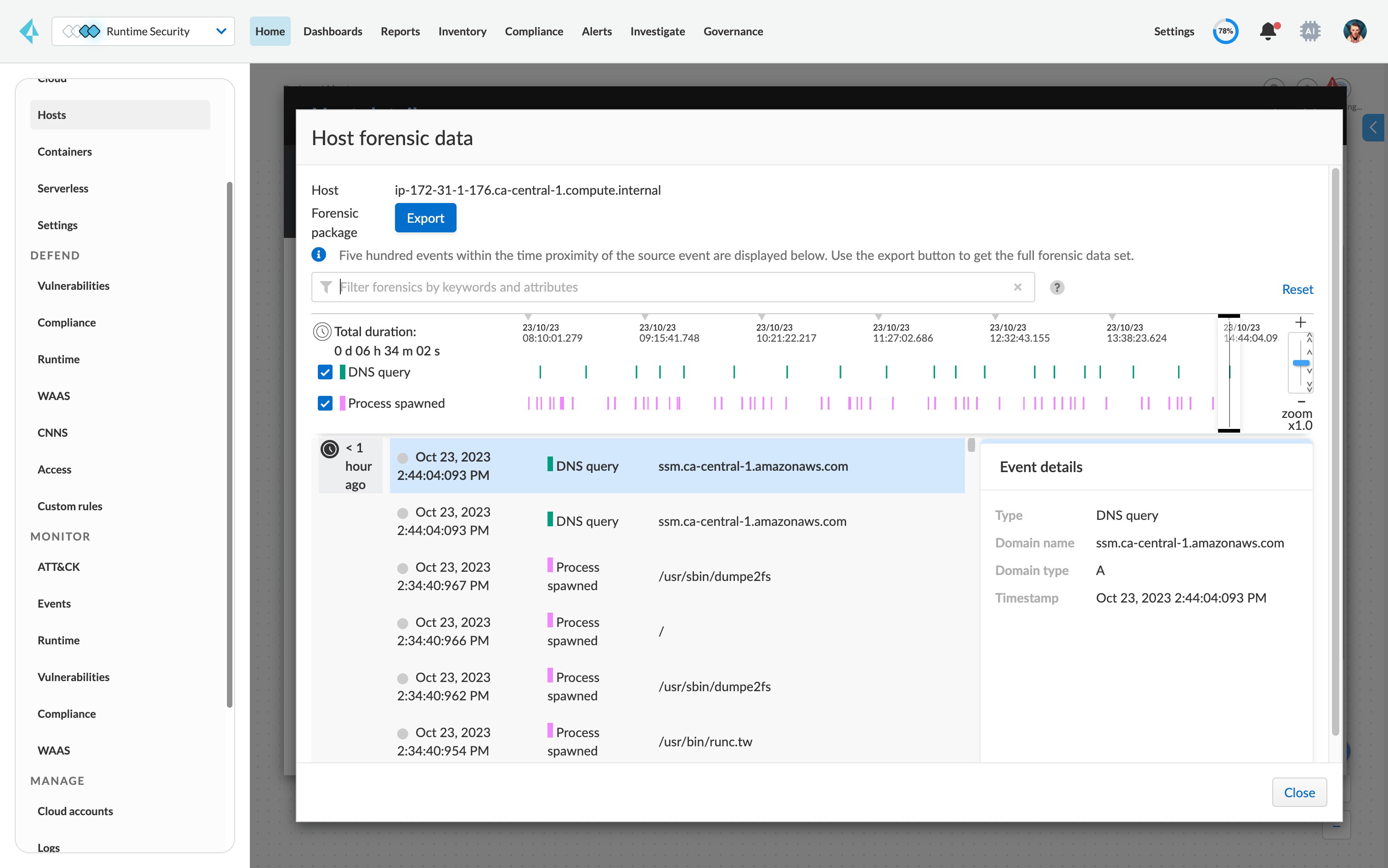
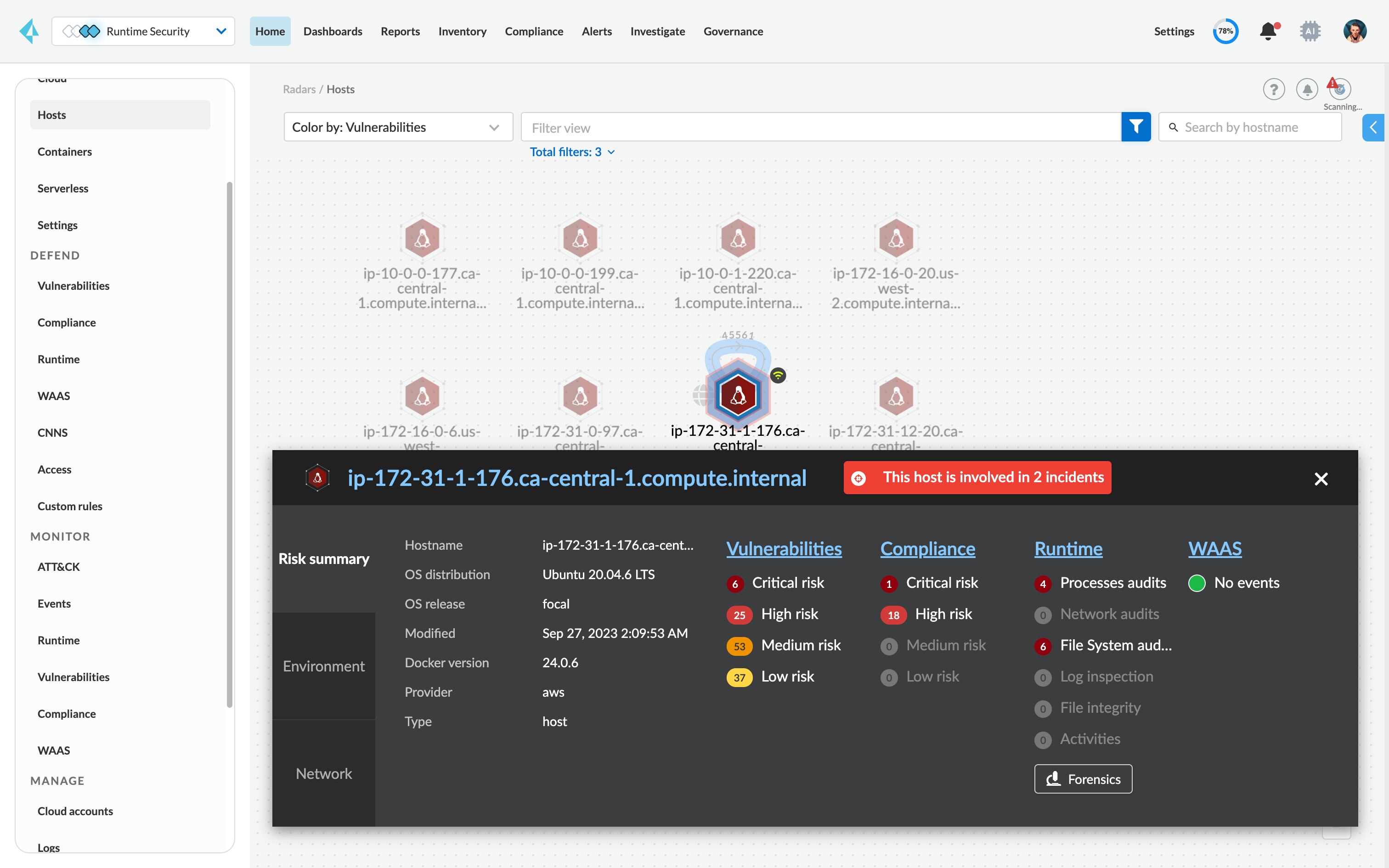
Gain a real-time view into vulnerabilities.
Scan running hosts continuously, with minimal increased load against the latest vulnerability databases.
Gain a consolidated view into risk across your stack from a single pane of glass.
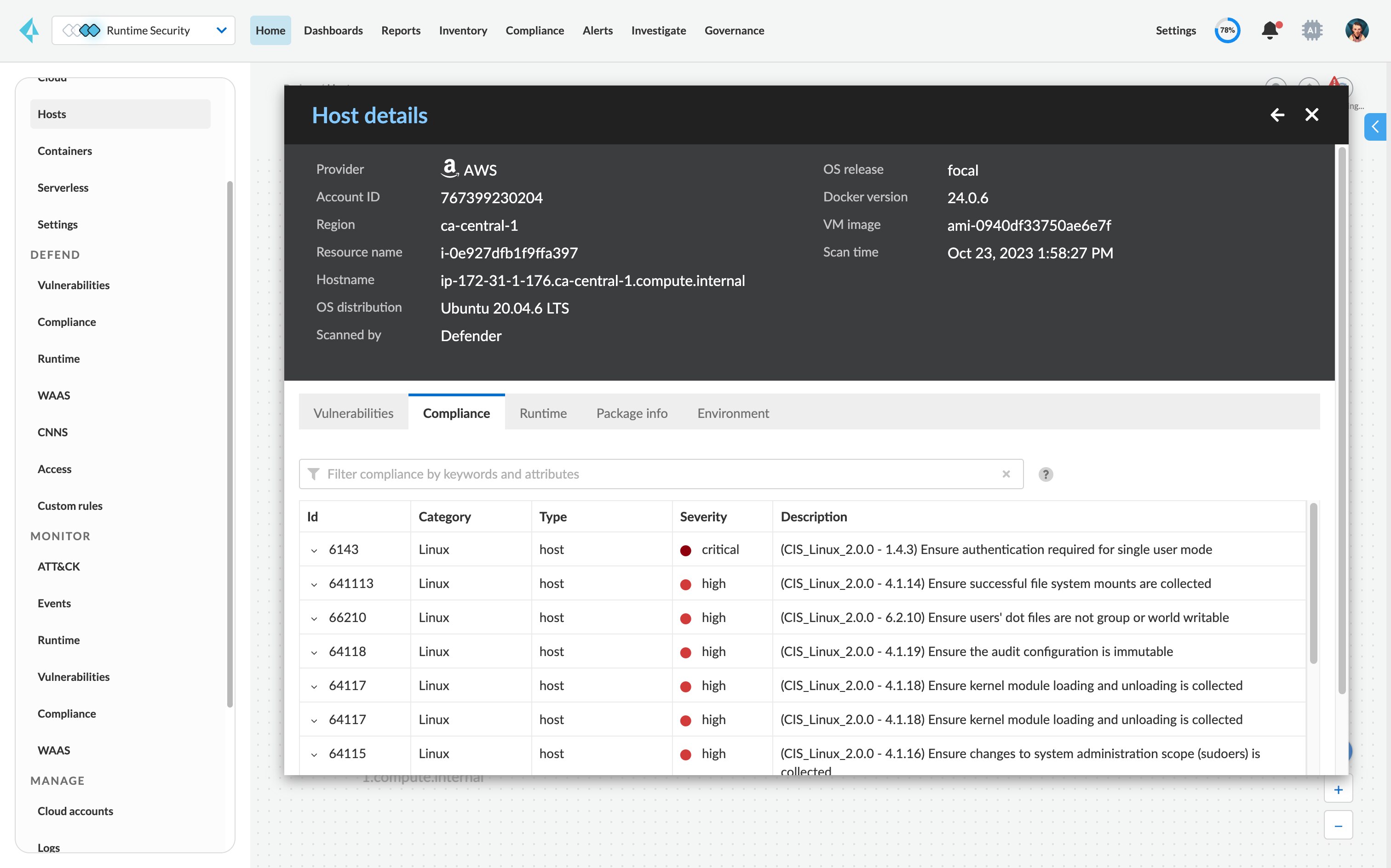
View risks across your hosts, containers and serverless applications from one unified console with flexible deployments (agents and agentless).
Protect against unpatched vulnerabilities.
Leveraging our WAAS module, you can block attempted exploits of vulnerabilities prior to patching the operating system.