Among cloud deployments averaging 1000s of configuration violations, security teams are realizing approximately 1% of their issues involve interconnected misconfigurations that create attack paths for adversaries.
Rapid proliferation of cloud infrastructure and workloads without unified, contextual security results in a dangerous outcome — enabling adversaries to exploit open attack paths before security teams even notice.
According to our recent cloud-native security survey, 90% of organizations report an inability to detect, contain, and resolve threats within an hour. What’s more, 76% of organizations say their collection of point-product security tools leave blind spots.
Why Fragmented Security Doesn’t Work
Organizations work with an average of 31 security tools across 13 security vendors, according to Palo Alto Networks research. But the complexity of managing vendors and point solutions can create security gaps.
Due to lack of integration and data unification across siloed products, security teams can miss context each time they discover a new security issue. Practitioners spend too much time combing through individual signals in a struggle to identify which issues, or combinations of issues, expose their organization to threats.
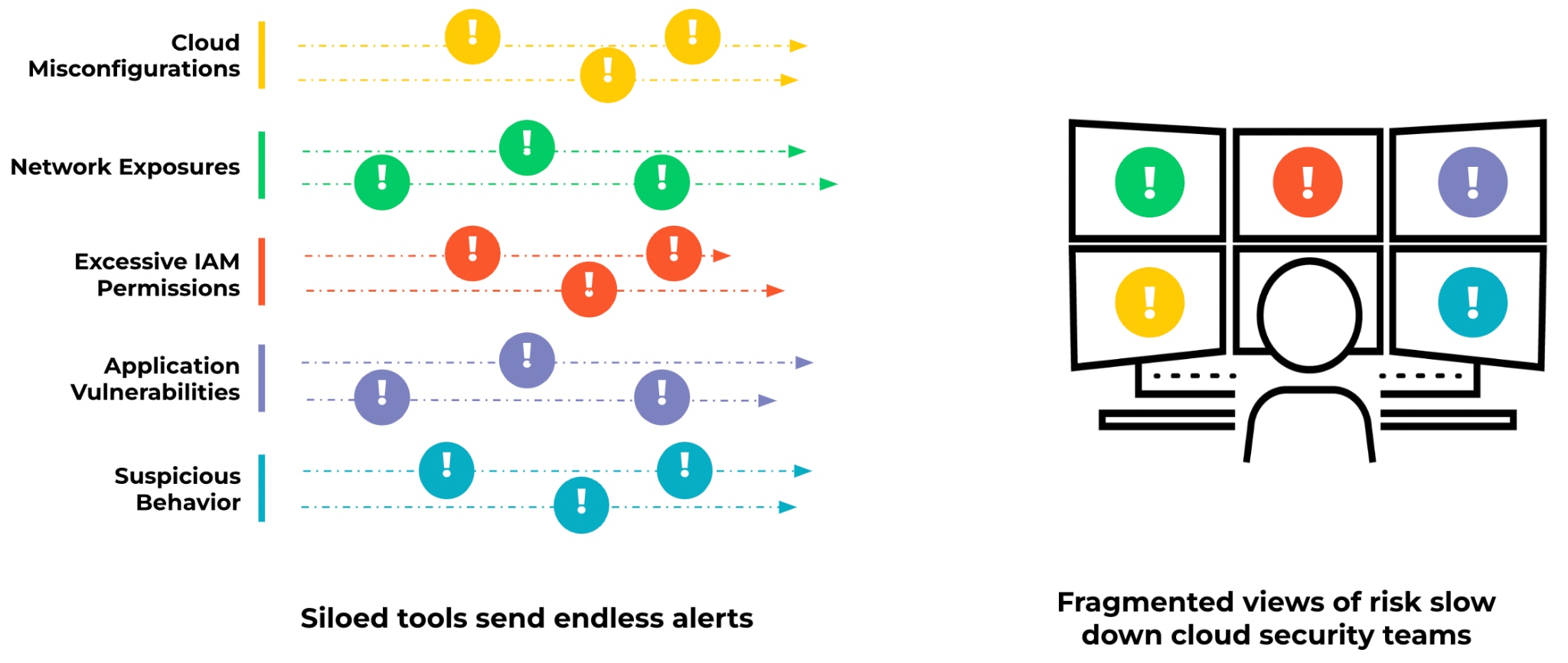
Security teams are seeking a better way to contextualize risk and identify potential attack paths. In fact, 78% of organizations agree that cloud security needs more out-of-the-box visibility and risk prioritization filtering.
Addressing attack paths requires a multidimensional approach. First, security teams need a single solution that ingests and consolidates several unique indicators of risk (e.g., misconfigurations, vulnerabilities, suspicious activity).
Next, that solution must contextualize these indicators of risk to identify open attack paths. To be immediately actionable, the solution ideally needs to provide recommendations on how to remediate the risk.
Dismantling Attack Paths with Prisma Cloud
Palo Alto Networks Prisma Cloud, the CNAPP that secures applications from code to cloud, is engineered from the ground up to solve this problem.
Unlike siloed tools, Prisma Cloud is built with a unified data model that automatically correlates findings across cloud misconfigurations, vulnerabilities, excessive IAM permissions, network exposures, and more to identify harmful combinations that cause impactful risk.
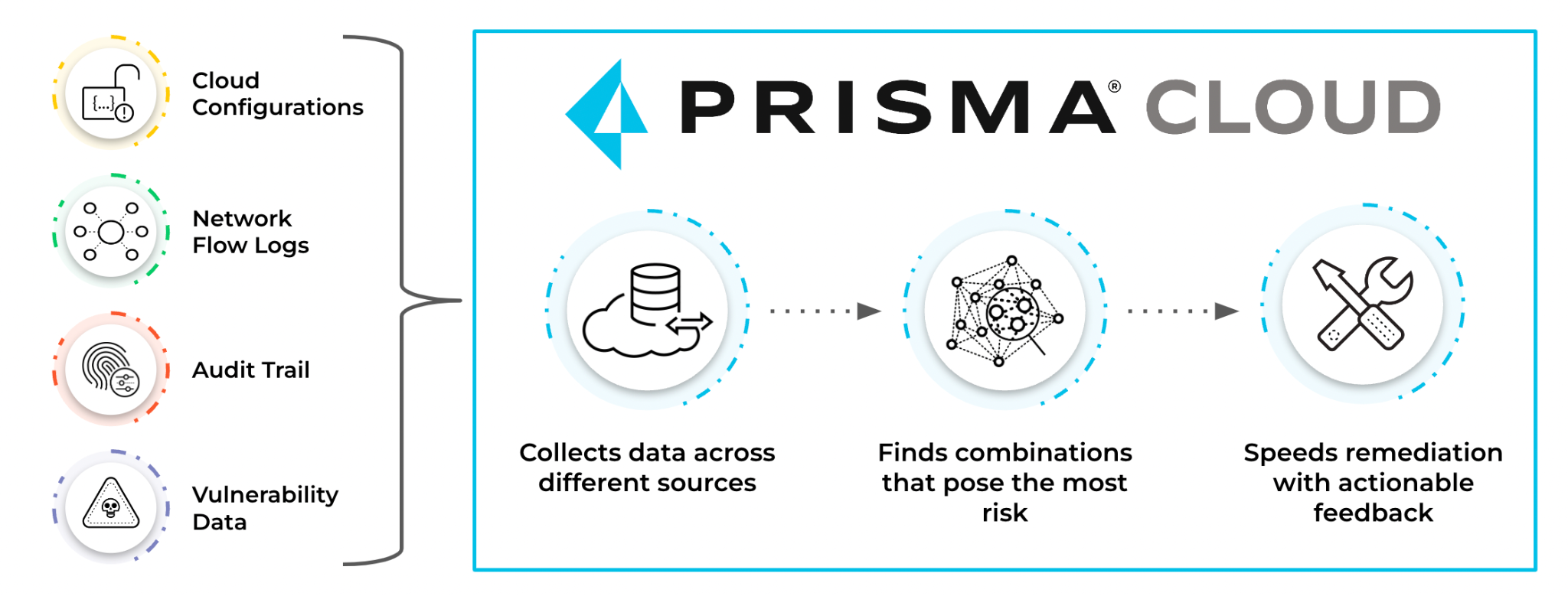
In addition to finding what could go wrong in cloud environments, Prisma Cloud applies threat context to identify what is going wrong. With Palo Alto Networks Unit 42 threat intelligence, coupled with machine learning (ML) and user and entity behavior analytics (UEBA), security teams can detect exploited attack paths.
Examples combinations potentially indicating attack paths:
- A workload with a critical vulnerability that’s exposed to the internet and has excessive access permissions.
- Azure AD user with Key Vault access performing unusual activity
- Detected network data exfiltration activity on a publicly accessible workload with a critical, exploitable vulnerability
The context-driven platform delivers insights with actionable feedback to address attack paths.
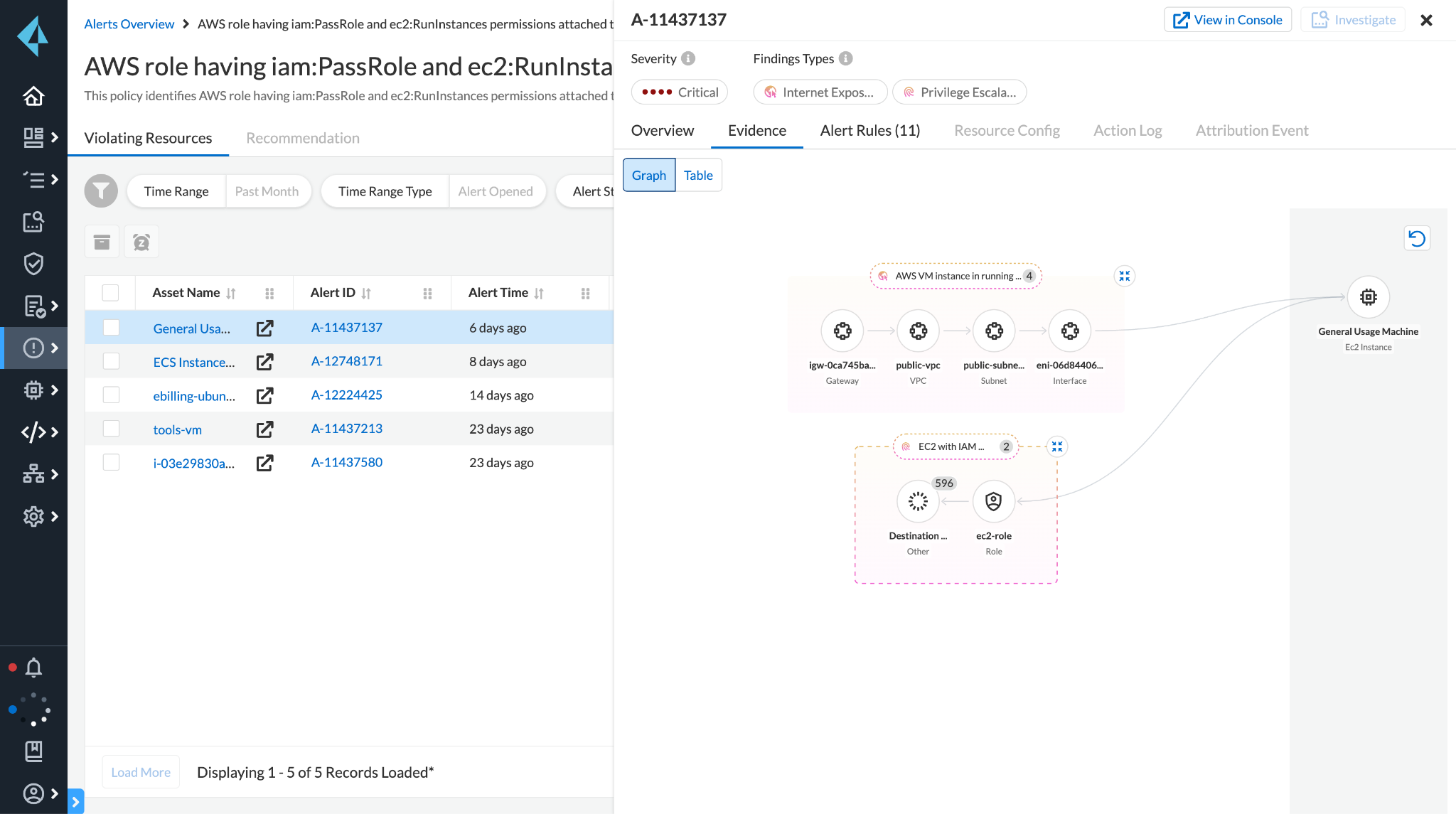
The Value of a Unified CNAPP
Prisma Cloud ingests one trillion cloud events daily and intelligently analyzes signals for groups of interconnected risk. Using Prisma Cloud, our early access users discovered 31 critical risks on average, accounting for 1% of their total cloud violations.
In addition to finding what could go wrong in cloud environments, Prisma Cloud applies threat context to identify what is going wrong.
Benefits of Prisma Cloud
- Increase SecOps efficiency: Spend less time chasing low-risk alerts and focus on issues that matter the most.
- Drive down risk: Identify security issues that pose the greatest likelihood of compromise and lateral movement, find the root cause, and remediate with actionable findings before attackers can exploit them.
- Improve the developer experience: Communicate the most urgent issues with application owners using context and evidence for frictionless remediation.
How to Defeat Critical Risk with Prisma Cloud
Addressing critical risk is nearly effortless, and organizations can get started right away. If you’re new to Palo Alto Networks, Prisma Cloud is a SaaS-delivered platform combining best-of-breed capabilities across:
- Cloud security posture management (CSPM)
- Cloud workload protection (CWP)
- Cloud infrastructure entitlement management (CIEM)
- Code security
- and more
Identifying attack paths with Prisma Cloud doesn’t require an agent installation. Users simply connect Prisma Cloud to their environments and begin burning down risk.
Want to know more about how Prisma Cloud disrupts attack paths? Join us on the Code to Cloud Security Summit and check out our session on Securing What’s Next in Your Cloud, where we dive into risk prioritization.
If you’d like to get hands-on experience with code-to-cloud security, then request a 30-day trial of Prisma Cloud.