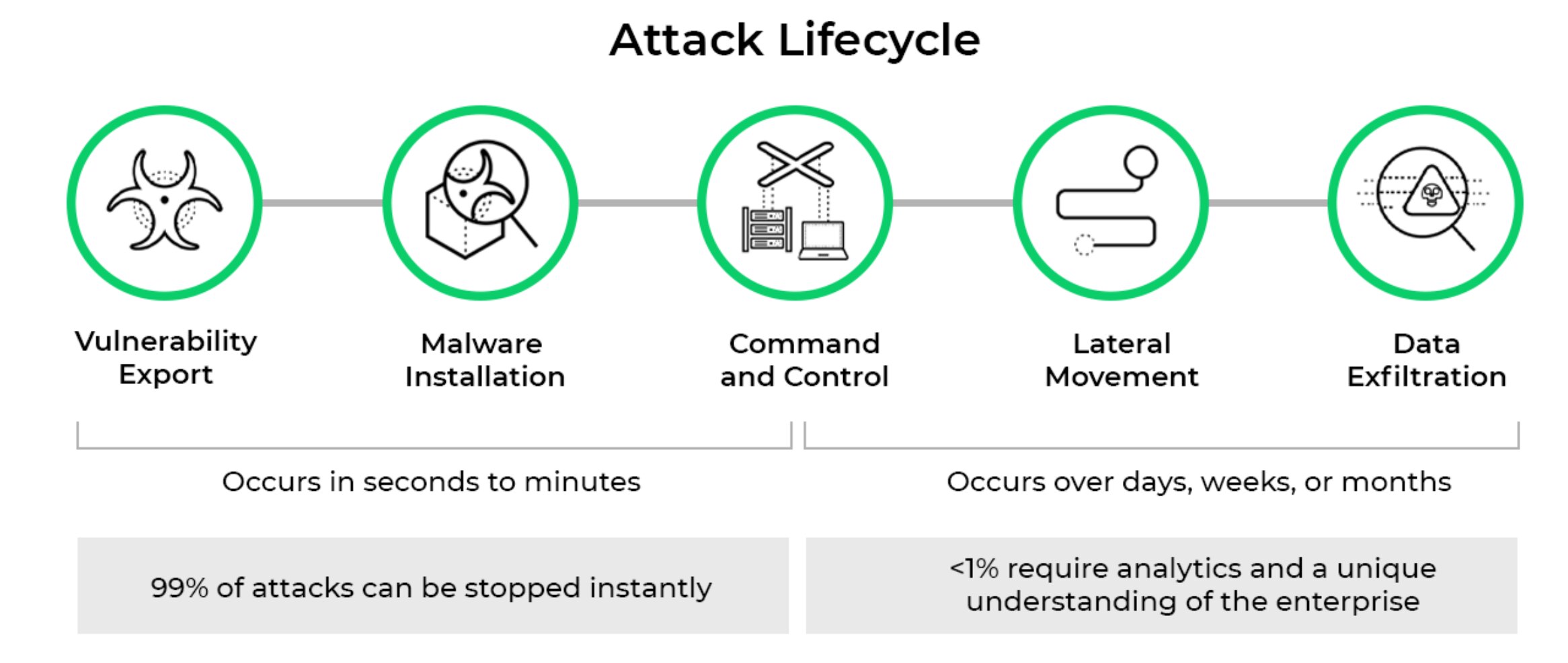
Advanced Threats Are Multi-Stage
Attacks are becoming increasingly sophisticated. At the same time, the list of new vulnerabilities and exposures is increasing rapidly, with thousands of high-impact exposures affecting applications and protocols being discovered every month.
Malicious actors have developed new, advanced threats affecting multiple systems and employing multistage attacks. Notably, fileless attacks operate without executable files, in an
attempt to evade security defenses and maximize impact. Moreover, these advanced, complex threats can affect a number of systems and tools - including protocols, applications, and registry keys. Siloed, signature-based antivirus software, and traditional intrusion prevention systems are ineffective against these new threats.
Finally, high-impact attacks such as ransomware employ a variety of tactics, techniques, and
procedures (TTPs) from initial access to persistence, privilege escalation, credential access, lateral movement, defense evasion, persistence, and more.
In order to prevent known threats, and detect and block advanced attacks, you need to adopt
an extended detection and response (XDR) solution that expands visibility to the whole security estate, captures inclusive and rich telemetry, leverages all available data, and is able to reconstruct the story of an attack - going from simple, isolated alerts to all-encompassing
incidents.
![]()
Figure 1: The challenge is not being overcome with traditional approaches today
Data Is the Foundation of Threat Hunting
According to a recent survey, 68% of organizations measuring their threat hunting saw a significant increase in the overall security posture of their organization.1 Therefore, many organizations that are on a path to develop a strong security posture recognize the value of threat hunting.
Furthermore, 51% of responding SOC organizations are on a path to threat hunting maturity. SOCs are constantly developing new techniques and methodologies for threat hunting. These techniques range from simple to very complex, including detections based primarily on indicators of compromise (IOCs), and more elaborate and accurate use cases relying on full TTPs.
![]()
Figure 2: Targeted attacks can’t be stopped with IOCs
Data is foundational for threat hunting, and the benefits of threat hunting are diverse. They include an improvement in the accuracy of threat detections derived by additional context from research and telemetry and a reduction in false positives from developing use cases tailored to an organization’s requirements, objectives, and technology environment.
To enable and take a comprehensive approach to threat hunting, organizations should empower their security team with the right skills and capabilities. Security solutions play an important role in threat hunting: capturing good and comprehensive data, applying analytics, and presenting insights in a way that is easily consumable to a cyber analyst. A sound threat hunting methodology is therefore underpinned by the right security solutions and an expansive set of telemetry and insights.
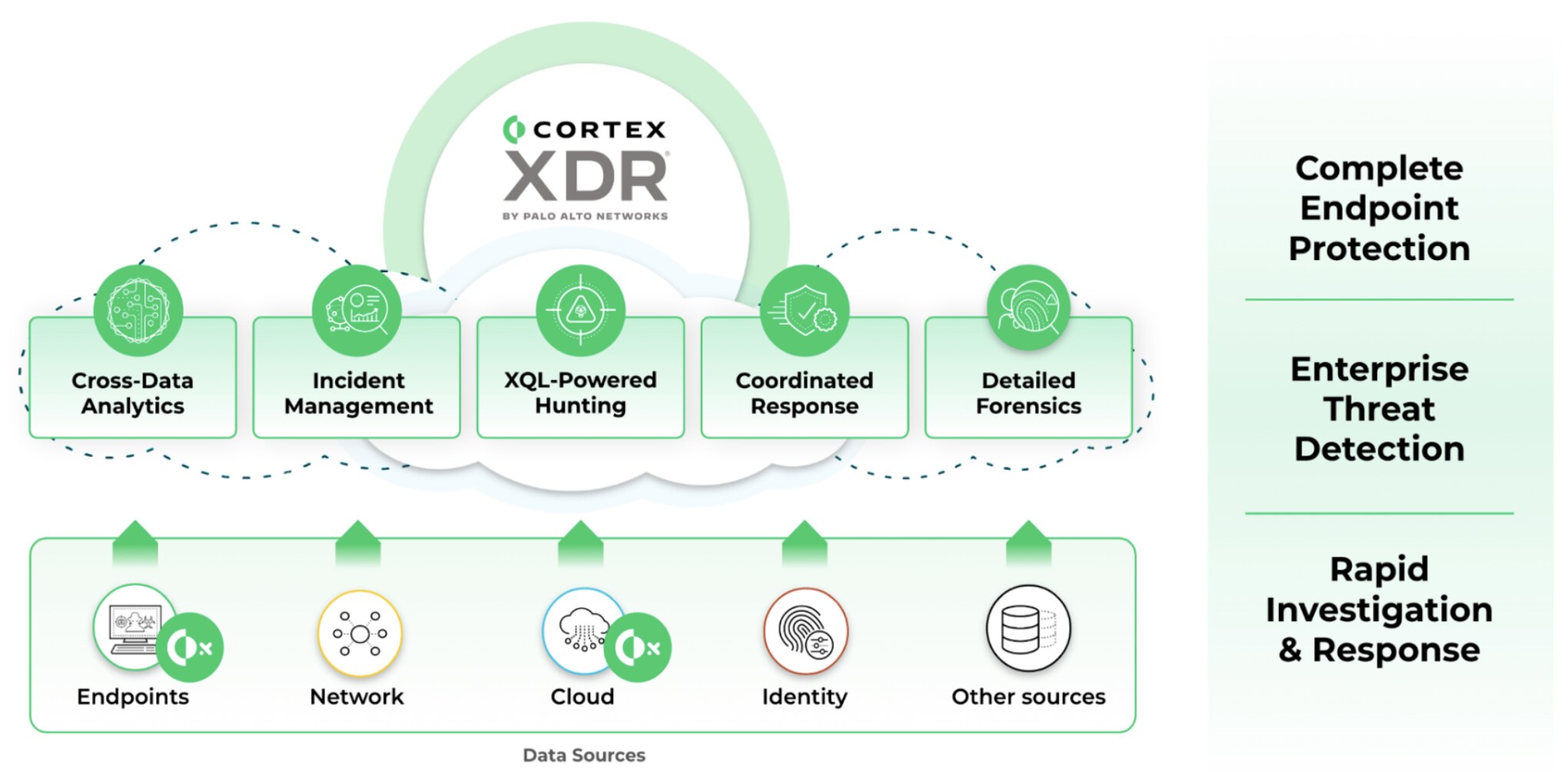
Cortex eXtended Threat Hunting Data Module
The new, optional eXtended Threat Hunting Data Module (XTH) adds key functionalities to Cortex XDR Pro, unlocking technological capabilities that augment your security operations team. By onboarding additional telemetry to XDR Pro, XTH unlocks advanced analytics in XDR that allow you to increase threat detection accuracy and scope. Additionally, XTH leverages advanced telemetry to deliver more visibility and insights, in order to boost your team’s threat hunting abilities.
The XTH module enables organizations to:
- Supercharge threat hunting by unlocking additional analytics and machine learning-powered detectors.
- Boost advanced detection use cases, increasing coverage and precision against lateral movement, credential & file stealing, discovery, supply chain, and more.
- More context and insights on top of XDR Pro to better identify attacker actions and techniques, enhancing Cortex XDR’s MITRE-relevant insights.
- Gain deeper visibility and see stronger causality links between attacker actions and affected entities
![]()
Figure 3: Cortex XDR detects stealthy attacks by analyzing integrated data with machine learning and behavioral analytics
By increasing data collection at the machine, network, and operating system level, XTH expands Cortex XDR Pro’s data analysis capabilities to a plethora of event types, increasing visibility. You can now detect even more sophisticated attacks, including instances of manipulation via remote injection. The additional insights that XTH brings to XDR Pro allow you to efficiently block and mitigate stealthy attacks that leverage multiple MITRE stages like credential dumping, lateral movement, privilege escalation, and more.
XTH enhances Cortex XDR’s visibility, detection and response capabilities, allowing you to take a proactive stance against advanced threats, detect and respond effectively, and prepare for threat hunting.
Full Coverage for Threat Hunting, Investigation and Detection
The XTH Module in Cortex XSIAM and XDR delivers analytics-driven detection capabilities that empower security teams to prevent threats faster and detect effectively with more precision.
- Extend your visibility by ingesting more event types
- Gain additional context to identify unusual behaviors and stealthy attacks
- Identify the full story of an incident with better causality data
- Prevent and block complex attacks
- Supercharge XDR Pro’s detectors and threat hunting capabilities
- Better coverage of network, machines, operating systems, and applications enables more advanced analytics in XDR Pro
- Sharpen your detection to unearth stealthy threats and get ahead of attackers
- Additional telemetry allows more accurate profiling of network entities, machines, and users
- Gain better insights into machine-level and operating system-level data for more detailed investigations
- Proactively hunt for threats with XDR, analytics, and UEBA
- Unlock advanced analytics and behavioral models with XTH
- Leverage machine learning and adopt hundreds of pre-built detection use cases
With more innovations in Cortex XSIAM and XDR, we continue to advance our mission to help customers protect their organization and make it easier for them to do this. The new advanced XTH Module unlocks advanced analytics and provides comprehensive coverage for sophisticated attack techniques and anomalous behaviors. It allows you to increase SOC maturity, enable threat hunting, and add more value to your organization.
How to Get the XTH Data Module
Palo Alto Networks’ offering enables threat hunting use cases in Cortex XSIAM and Cortex XDR. The XTH module is already part of XSIAM, and can be purchased as an add–on to Cortex XDR Pro.