What Is Zero Trust Edge (ZTE)?
Zero Trust edge (ZTE) is a cloud-driven architecture that integrates networking and security and uses Zero Trust to authenticate and monitor network interactions.
Enterprises are using Zero Trust networking principles increasingly to securely connect growing numbers of users and devices to resources, which is a primary driver for ZTE. For many organizations, a main application of ZTE is to secure remote workers and reduce dependence on virtual private networks (VPNs).
Why Is Zero Trust Edge Important?
ZTE is important because it provides a more secure gateway to the internet and access to an organization’s applications and data for an organization's physical sites and remote workforce.
Three key factors drive the deeper integration of networking and security inherent in ZTE:
- Network traffic must adhere to strict security trust levels and comply with established policies.
- Rather than security teams overlaying corporate networks, organizations must adopt ZTE policies and pursue networking with a security-centric approach.
- All clients and endpoints must have secure internet access, capable of neutralizing or bypassing potential malware threats at any point in the network route.
Digital acceleration, characterized by hybrid workplaces and widespread application access, expands the attack surface and heightens business vulnerability to advanced threats. Traditional network architectures with point products and implicit access to all applications are no longer adequate.
The ZTE model addresses this challenge by forming a new perimeter. It converges security and networking across all points, granting explicit access to applications based on continuous validation of user identity and context. This establishes the crucial role of ZTE in the modern digital ecosystem, serving as an effective defensive shield in an increasingly interconnected, threat-prone environment.
How Does Zero Trust Edge Work?
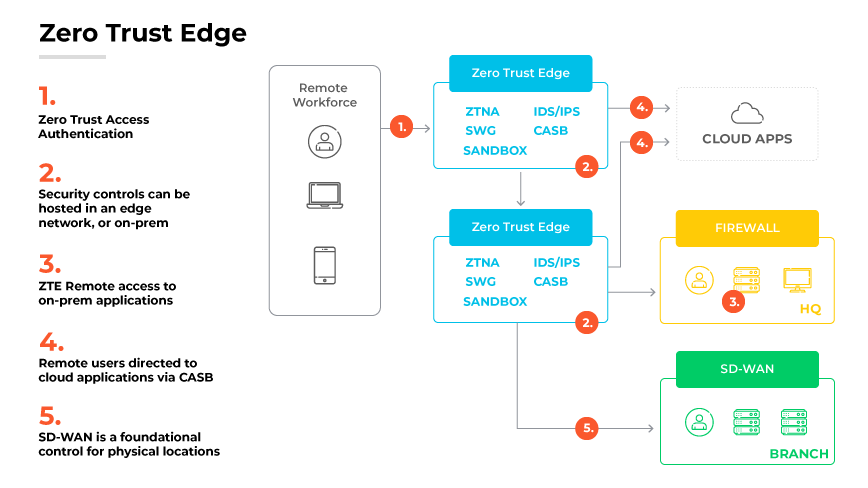
Zero Trust edge applies meticulous authentication and validation; in essence, it considers every network transaction as potentially risky.
When it comes to the mechanics of ZTE, it originates by placing elements of ZTE in a cloud or edge-hosted security stack, factoring in bandwidth constraints, which might necessitate local infrastructure for some components.
ZTE relies on two critical cloud-driven principles:
Cloud-based network and security management:
Ensures policy uniformity across the enterprise, reducing errors and improving efficiency.Analytics tools that seamlessly link networking and security:
Allows for better link utilization, early detection of network anomalies, and comprehensive network monitoring.
This calls for cloud-based solutions due to the substantial data volume needing storage and processing for effective analytics.
When deployed, ZTE allows organizations to centrally manage, monitor, and analyze a range of security and networking services, whether hosted on the cloud or remotely. The ultimate objective is to provide stringent security without compromising on networking capabilities.
ZTE Implementation
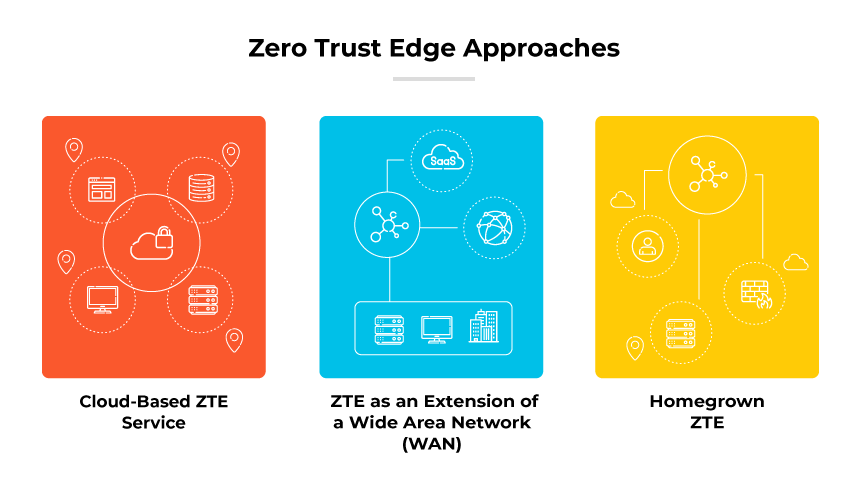
Organizations have three main paths for implementing ZTE:
Cloud-Based ZTE Service
A cloud-based ZTE service uses multiple points of presence (POPs) with inherent ZTE capabilities. This approach mirrors software-as-a-service (SaaS) delivery models.ZTE as an Extension of a Wide Area Network (WAN)
A homegrown approach incorporates ZTE as an extension of a wide area network (WAN) connection service.
Carriers offer ZTE functionality and outsourced security. Although several options exist for on-premises solutions, they may lack the agility of cloud-based systems. In addition, combinations of SD-WAN and ZTE require individual policy configurations for each service, rendering a single, holistic solution unfeasible.Homegrown ZTE
Larger, nimble organizations have the option of developing their own ZTE offering. This method necessitates public cloud services for POPs and cloud-hosted firewalls, among other security services. Despite its inherent flexibility, homegrown ZTE requires constant monitoring of evolving security components and cloud services. Adequate IT expertise to manage and maintain the offering is also critical.
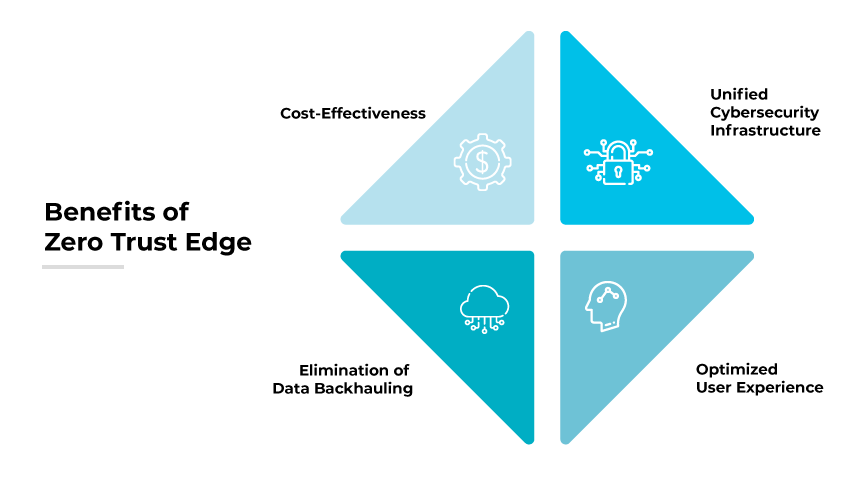
Benefits of Zero Trust Edge
Enhanced Risk Mitigation
A primary benefit of ZTE lies in its ability to substantially reduce network vulnerabilities. With security ingrained at every level of the network and every transaction undergoing rigorous authentication, potential threats are mitigated significantly. Regardless of where users are connecting from or what applications they're using, ZTE provides consistent, high-level security.
By enforcing consistent and coordinated security policies across all connection sources, ZTE also safeguards hybrid workplaces. Regardless of whether employees connect from unmanaged networks or the office, ZTE applies the same level of scrutiny.
ZTE also enables Zero Trust network access (ZTNA) everywhere. It shifts from implicit trust to explicit access based on identity and context, resulting in continuous validation. This ensures effective control of network access, enhancing overall network security.
ZTE improves incident response capabilities. By fostering team collaboration, ZTE enhances incident response capabilities and simplifies troubleshooting, providing a more proactive approach to security management.Cost-Effectiveness
Due to its cloud-based and automated nature, ZTE networks provide an economical, scalable security solution. As an inherent part of the internet, they accommodate digital transformation effortlessly, unfettered by legacy architectures. This results in substantial cost savings and ensures organizations only pay for the resources they utilize.Optimized User Experience
ZTE facilitates an enhanced user experience by improving networking performance and throughput. It focuses on providing optimal paths and a comprehensive digital experience, significantly accelerating application performance.Unified Cybersecurity Infrastructure
ZTE adoption condenses multiple cybersecurity tools into one unified solution, simplifying the monitoring, analysis, and response to cybersecurity threats. Consolidation leads to a more manageable, efficient cybersecurity infrastructure, eliminating potential compatibility issues.
ZTE's comprehensive capabilities reduce the need for multiple security vendors, offering the option for a single or limited number of vendors. It's essential, however, that organizations ensure vendors can effectively integrate solutions into the existing network infrastructure.Elimination of Data Backhauling
Traditional Virtual Private Network (VPN) setups often backhaul remote users’ traffic through corporate networks. This process can result in significant bandwidth congestion. However, ZTE employs cloud on-ramps for global connectivity and security inspection, thereby eliminating data backhauling and boosting performance.
ZTE Challenges
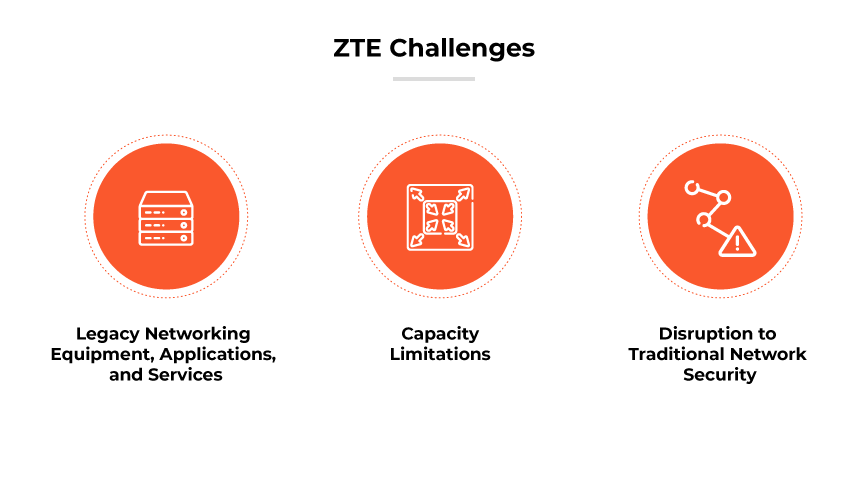
Legacy Networking Equipment, Applications, and Services
The incorporation of operational technology (OT) and internet of things (IoT) devices can complicate the transition to a ZTE framework. These devices, potentially numbering in the thousands within an organization, may be tied to legacy networking gear. Transitioning these devices to a ZTE network can be a complex process requiring substantial infrastructure overhauls.
Compatibility with legacy hardware is another significant hurdle in transitioning to ZTE. Critical infrastructure components may depend on outdated hardware, and modernizing these components can be a daunting task. Additionally, some legacy hardware may not support the requirements of ZTE, necessitating the reassessment and potential replacement of operational technologies and IoT devices.
Integrating legacy applications and services into the ZTE framework pose significant challenges as well. Especially problematic are applications built on non-web protocols, such as Remote Desktop Protocol (RDP) or virtual desktop infrastructure (VDI) for remote access and Session Initiation Protocol (SIP) or Voice over IP (VoIP) for voice services. These applications lack standardized procedures for ZTE utilization, complicating their integration.Capacity Limitations
Capacity constraints are difficult in ZTE implementation. While ZTE can address remote workforce access issues, it currently lacks the capacity to replace high-volume network and security services that provide data center access. As a result, organizations may need to pursue cloud migration before transitioning certain enterprise assets to ZTE protection.
Prior to ZTE implementation, enterprises must carefully assess network capacity. If near capacity limits, additional workarounds may need to be identified or significant upgrades undertaken. In some cases, it may be necessary to migrate to a cloud-based infrastructure before implementing ZTE, which could add further complications to the transition process.Disruption to Traditional Network Security
As a new and transformative approach, ZTE disrupts traditional network security practices. This disruption may create challenges as organizations adjust to the paradigm shift, particularly as network security has traditionally been practiced in fundamentally different ways. The transition process can thus be complicated, requiring significant planning and adaptation.
What Is the Difference Between Zero Trust Edge and SASE?
Secure access service edge (SASE) and Zero Trust edge (ZTE) share common principles and goals such as the consolidation of network functionality and cloud-delivered security. However, they differ in their emphasis and approach.
SASE represents a convergence of Software-Defined Wide Area Networking (SD-WAN) and a range of network security services into a unified cloud-based offering. It enables secure, efficient network access, catering to the needs of increasingly remote and distributed workforces.
ZTE, defined as an evolution of the original SASE model, zeroes in on the "Zero Trust" component, aiming to establish a rigorous Zero-Trust-as-a-Service beyond access controls. ZTE is reflective of the Zero Trust approach in assuming a worst-case scenario, whereby it authenticates every connection, regardless of nature or origin.
While SASE provides an amalgamation of network services and security in a cloud-based model, ZTE adopts a more stringent stance, focusing intensely on authentication to uphold Zero Trust principles across the network infrastructure.
Zero Trust Edge FAQs
Zero Trust network access (ZTNA) is a category of technologies that provides secure remote access to applications and services based on defined access control policies. It uses the same Zero Trust principles, but serves as a component of ZTE.