-
- Why is threat prevention important?
- How does threat prevention work?
- What are the differences between threat prevention, detection, and protection?
- What are the different types of threat prevention?
- Top 5 threat prevention tips, tricks, and best practices
- Why threat prevention is harder than it sounds (yet more achievable than it used to be)
- Threat prevention FAQs
Table of contents
-
What is UEBA (User and Entity Behavior Analytics)?
- How UEBA works
- Benefits of Implementing UEBA
- Examples of UEBA
- Common Use Cases for UEBA
- Challenges and Considerations in UEBA Deployment
- Diverse Threats Addressed by UEBA
- Integrating UEBA and XDR
- UEBA vs NTA
- UEBA vs SIEM
- UEBA vs IAM
- Future Trends and Developments in UEBA
- Choosing the Right UEBA Solution
- UEBA FAQs
- What Is Penetration Testing?
- 3 Challenges to Identifying Evasive Threats
- What is a Port Scan?
What Is Threat Prevention? [Definition, Explanation, + How-tos]
7 min. read
Table of contents
Threat prevention is the practice of proactively stopping cyberattacks before they can cause harm.
It involves implementing controls that block unauthorized access, malicious activity, and exploitation attempts across systems, networks, and applications. These controls are designed to reduce risk by limiting attackers' ability to gain entry or execute malicious actions.
Why is threat prevention important?
Threat prevention is important because most successful attacks exploit preventable weaknesses. These include poor access controls, unpatched systems, and misconfigured services.
Controls that stop known threats early help prevent downstream consequences like lateral movement, data loss, and system compromise.
Preventive measures also reduce the operational load on detection and response. Preventing harm is more efficient and cost-effective than trying to mitigate it after the fact. The longer a threat persists, the more complex and expensive it becomes to contain. Proactive security reduces that exposure.
- In 2024, 86% of incidents that Unit 42 responded to involved business disruption — spanning operational downtime, reputational damage or both.
- In 41% of incidents, there was at least one contributing factor related to issues with identity and access management, including overly permissioned accounts and roles.
- By tackling complexity, gaps in visibility and excessive trust, organizations can materially reduce the risk and impact of cyberattacks.
Modern threat actors, including those using generative AI, can automate reconnaissance, targeting, and malware delivery at scale. This makes traditional response-based approaches less reliable on their own.
Threat prevention provides a necessary first layer that limits attacker access and reduces the risk of escalation.
How does threat prevention work?
Threat prevention works by enforcing security controls before a threat can run, spread, or cause damage. Instead of waiting to detect and respond after an incident, it proactively blocks malicious activity in real time.
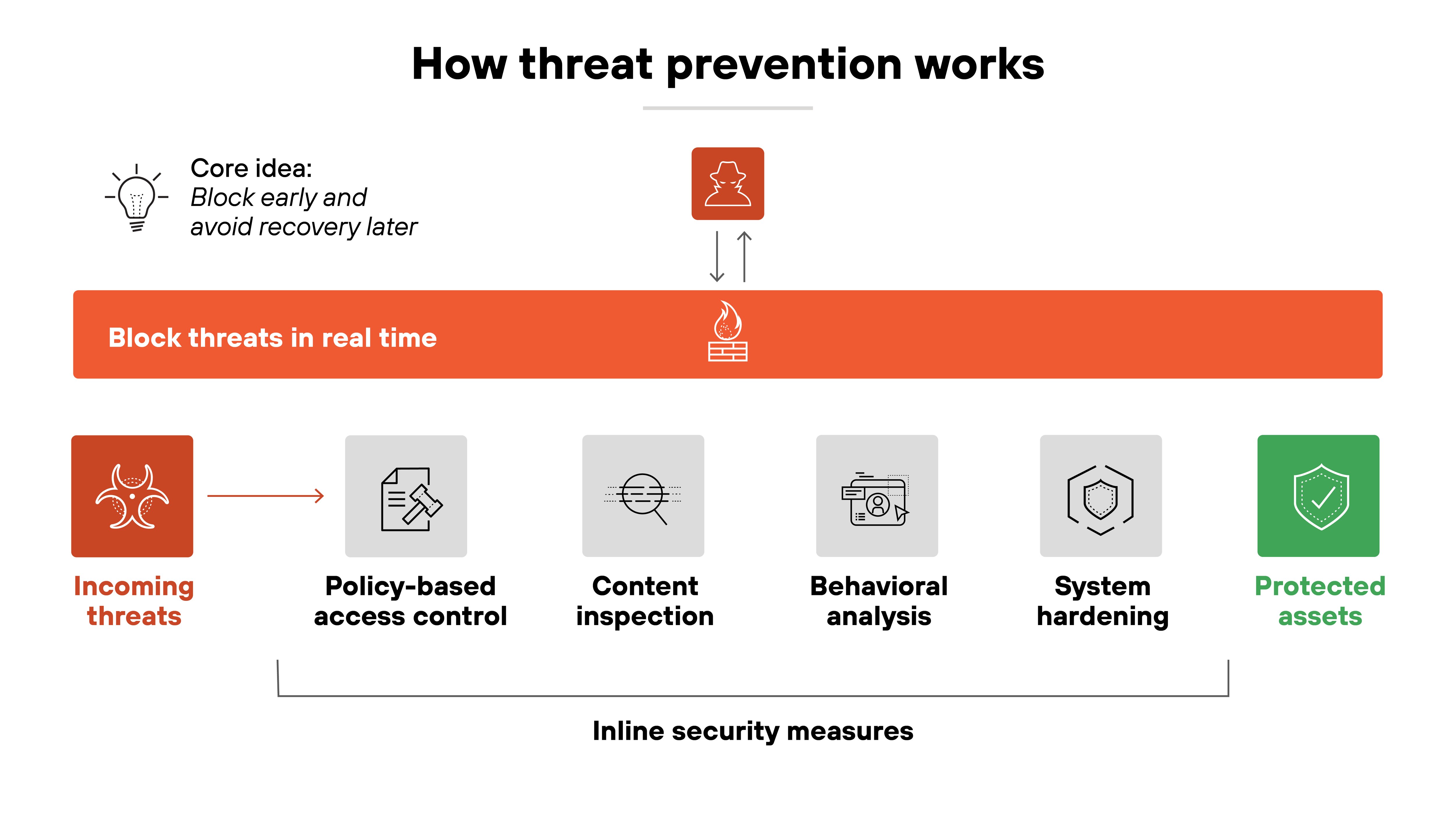
This happens through a mix of techniques, like policy-based access control, content inspection, behavioral analysis, and system hardening.
Many of these measures act inline, meaning they evaluate and stop activity as it occurs. Others reinforce security posture by reducing attack surface or limiting what an attacker can do if they get in.
In practice, prevention happens at multiple layers. But the core idea stays the same: Block what you can early, so you don't have to recover from what you could've stopped.
What are the differences between threat prevention, detection, and protection?
These terms are often used interchangeably, but that leads to confusion. Some vendors label detection as protection. Others describe reactive tools as preventive. It's worth clarifying what a solution actually does before assuming where it fits.
Threat prevention is about stopping attacks before they can do harm. It uses controls like MFA, web filtering, and secure configurations to reduce risk up front. The goal is to block known and unknown threats before they reach critical systems or data.
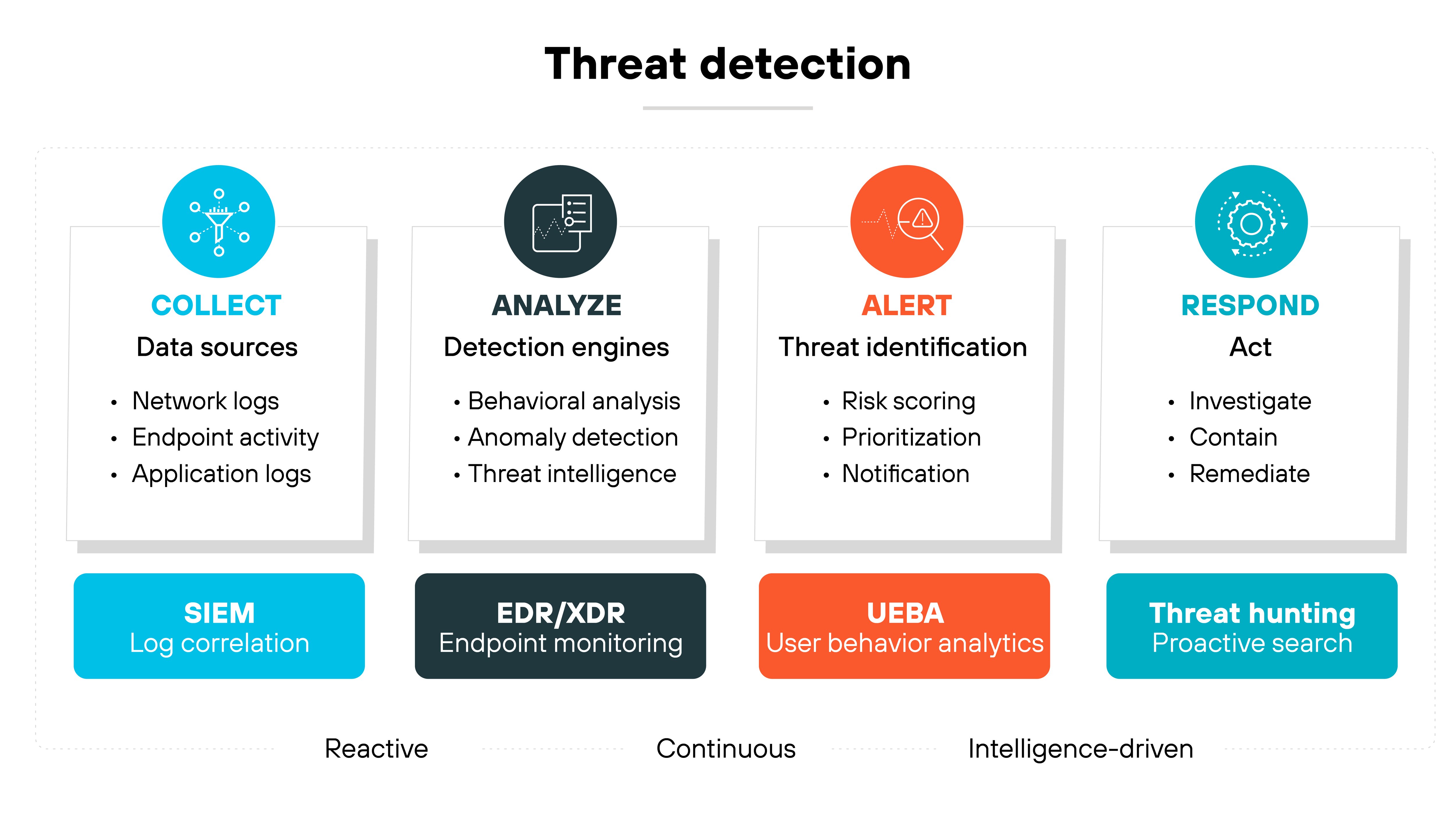
Threat detection comes into play when prevention fails. It involves identifying malicious activity that has already bypassed defenses. Detection methods include anomaly detection, behavioral analytics, and endpoint detection and response (EDR). These tools help surface threats that might otherwise go unnoticed.
Threat protection is the broader category that includes both prevention and detection. It refers to the combined effort of reducing exposure and identifying threats in progress. Some use the term to describe any security measure. Others use it to refer to endpoint-specific controls.
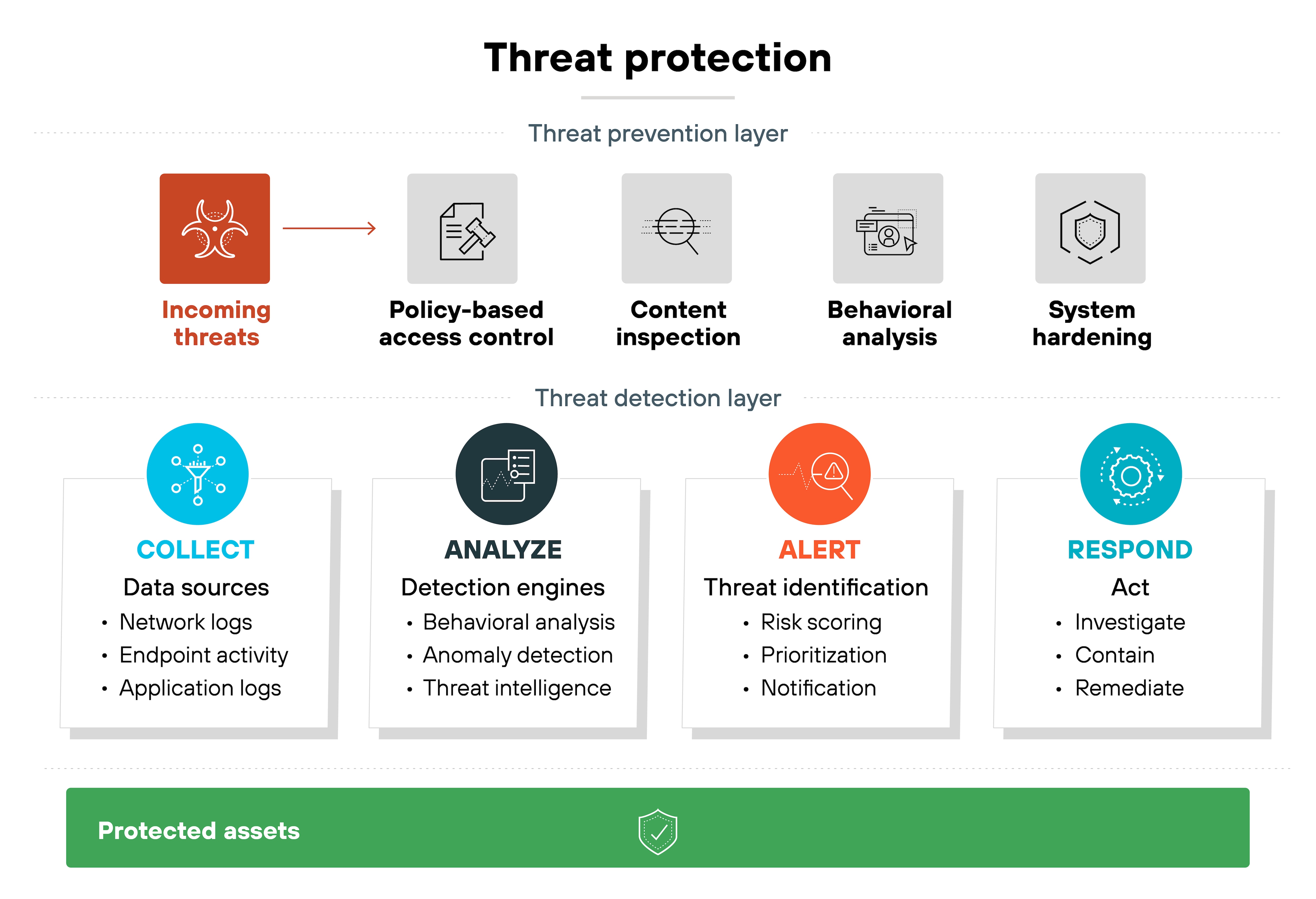
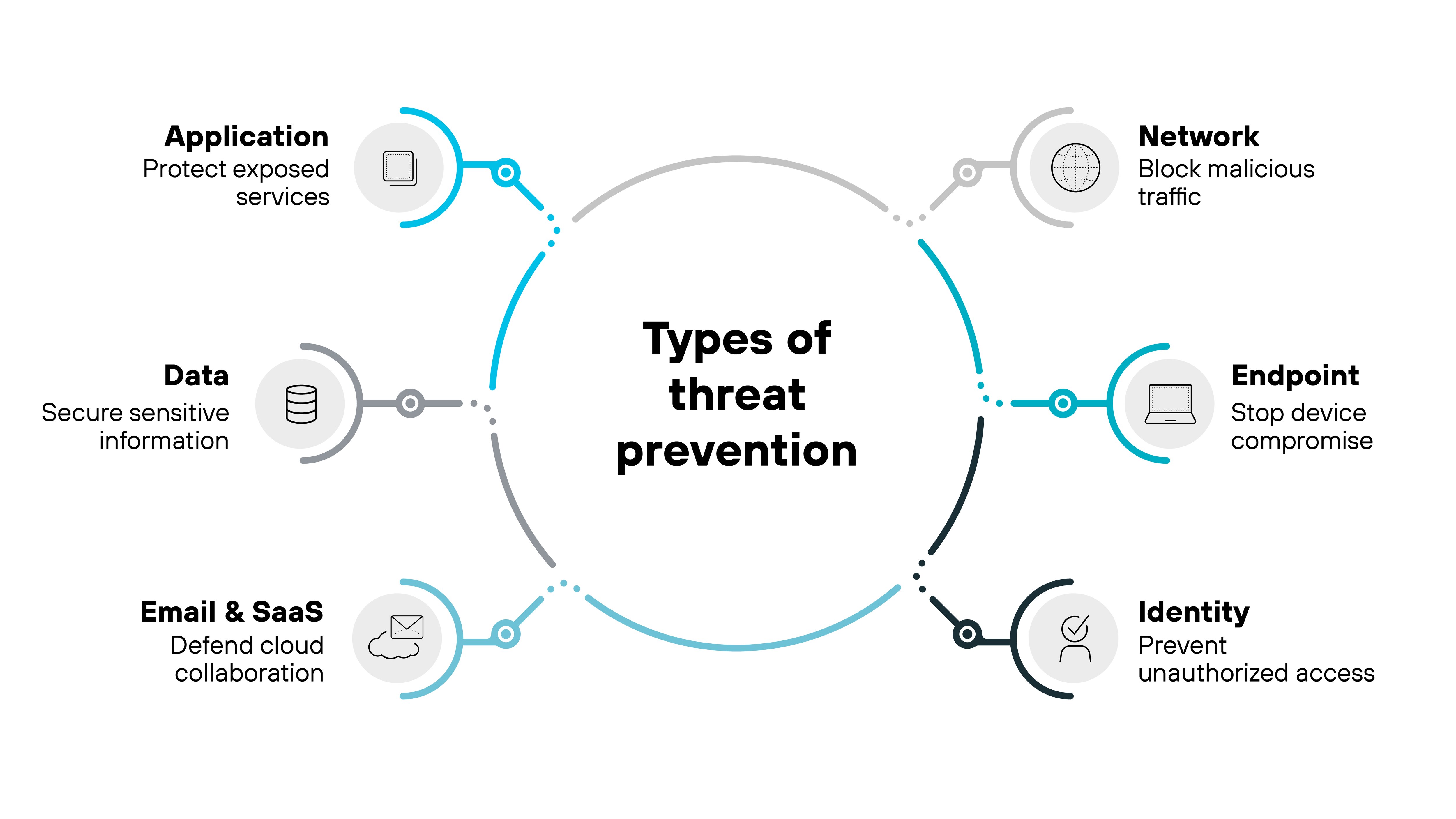
Threat prevention isn't a single control. It's a collection of strategies applied across different parts of your environment.
The goal is simple: Stop threats before they can execute or cause harm. But how that happens depends on where the protection is applied.
Here's a breakdown of threat prevention by functional domain, with examples that reflect how organizations actually deploy prevention in the real world.
Network threat prevention
Network-based threat prevention inspects, filters, and controls traffic, both at the perimeter and within internal segments.
Key technologies include:
- Firewalls that enforce policy across zones
- Intrusion prevention systems (IPS) that block known exploits
- DNS security to disrupt domain-based threats and C2 callbacks
- Microsegmentation to limit lateral movement
This layer blocks malicious traffic before it hits endpoints or apps. Many systems now use machine learning to flag anomalies in encrypted or evasive traffic.
Note:
Inline threat prevention isn't just for traffic entering the network. Internal segmentation is just as important. Many attacks escalate only after moving laterally. So blocking east-west traffic helps contain them before they reach high-value targets.
Endpoint threat prevention
This layer protects devices like laptops, desktops, and servers by blocking malware and exploit techniques directly on the system.
Common tools include:
- Next-generation antivirus (NGAV) with behavior-based detection
- Device control policies for USB and peripheral restrictions
- Memory protection to stop buffer overflows and code injection
Stopping the initial compromise at the endpoint prevents privilege escalation, data theft, and lateral movement.
Identity threat prevention
Identity-focused prevention blocks unauthorized access and limits what valid credentials can do.
Controls include:
- Multi-factor authentication (MFA)
- Posture checks to assess device health
- Identity analytics to flag credential abuse and privilege escalation
This is essential because attackers often bypass defenses by logging in rather than breaking in.
Note:
Attackers don't need to break in if they can log in. Identity-based attacks now outpace traditional exploits. That's why prevention here isn't just about authentication. It's about understanding context, behavior, and access intent.
Application-layer prevention
This layer protects web applications and APIs exposed to users, developers, and partners. The focus is on stopping attacks that arrive through legitimate channels.
Key technologies include:
- Web application firewalls (WAFs)
- API gateways that enforce rate limits and validate inputs
- Bot protection to stop automation-based abuse
Modern attacks often exploit normal traffic patterns. Application-layer defenses profile behavior to catch misuse without relying solely on signatures.
Data-layer threat prevention
Data-layer controls secure sensitive information, whether stored, in transit, or in use.
Key technologies include:
- Data loss prevention (DLP)
- Encryption of data at rest and in transit
- Rights management to control access and usage
These safeguards act as a final barrier, ensuring attackers can't easily access or exfiltrate critical data. Even if other controls fail.
Email and SaaS threat prevention
This domain targets threats delivered through email or cloud-based platforms. Especially phishing, malware, and session abuse.
Controls include:
- Email gateways that scan links and attachments
- Sandboxing to isolate unknown payloads
- SaaS security posture management (SSPM)
- OAuth/session protection in collaboration platforms
These tools help stop threats at delivery and reduce abuse across widely used services.
Note:
Phishing remains one of the most common entry points. But today's SaaS threats go beyond email. OAuth token abuse, unmanaged apps, and misconfigured integrations all expose cloud environments to compromise.
Top 5 threat prevention tips, tricks, and best practices

Effective threat prevention isn't just about buying tools. It's about how you deploy them, connect them, and maintain them.
These five tips can help strengthen your preventive strategy without adding unnecessary complexity.
1. Focus on identity and access first
Most attacks still involve credential misuse. That's why identity-based prevention is one of the highest-impact places to start.
Implement MFA, restrict overly broad permissions, and verify device posture before granting access. This limits attackers' ability to authenticate, even if they have credentials.
Tip:
Harden defaults before adding tools. Don't rely on new technology to compensate for poor baseline hygiene. Review built-in platform settings, close unused ports, disable legacy protocols, and enforce secure defaults wherever possible. Especially in cloud and SaaS environments.
2. Prevent lateral movement by design
Once inside, attackers often pivot.
Use microsegmentation to block unnecessary east-west traffic. Restrict admin privileges. And apply least-privilege access consistently.
The more you isolate systems and enforce boundaries, the harder it becomes for threats to spread.
Tip:
Build a prevention-first incident playbook. Include prevention tuning and policy refinement as part of your incident response process. Not just remediation and recovery.
3. Prioritize behavior over signatures
Signatures can't catch everything. Especially AI-assisted malware and polymorphic attacks.
Add behavior-based controls that analyze how users, processes, and traffic behave. This includes tools like NGAV, UEBA, and adaptive policy engines. They give you visibility into subtle risks that static rules often miss.
Tip:
Prevention controls can degrade silently. If MFA isn't enforced, DLP isn't logging, or rules are bypassed by allow lists, you won't know until it's too late. Regularly test and validate whether your controls are actually working as intended.
4. Don't treat prevention as a checklist
Prevention is not a one-time deployment.
It requires maintenance. Patch management. Configuration drift detection. Policy tuning. These small operational details make or break your defenses.
Automate wherever possible, and review your controls regularly. Especially as your environment changes.
5. Connect your controls
Disconnected tools lead to blind spots.
Look for prevention technologies that share context across layers, like between your firewall, endpoint, and identity systems. This improves accuracy, reduces alert fatigue, and lets you enforce smarter, risk-based controls across your stack.
Tip:
Don't just react to prevention alerts. Use them to identify coverage gaps, spot patterns in attempted exploits, and strengthen defenses over time. Good prevention should evolve with the threats it's blocking.
Why threat prevention is harder than it sounds (yet more achievable than it used to be)
Preventing threats sounds simple. But in practice, it requires the right policies, tuned controls, and continuous maintenance.
Most organizations already own prevention tools, but struggle to configure, connect, and manage them effectively.
The reasons?
Complex environments. Users are everywhere. Data is everywhere. Threats change quickly, especially with AI. Attackers adapt faster than static controls. And many organizations assume prevention is working, even when critical controls are misconfigured or missing.
The good news: Prevention has gotten easier to operationalize.
Many modern platforms integrate policy, detection, and response. AI-assisted analytics reduce false positives. Unified control planes simplify tuning and enforcement.
Threat prevention isn't automatic. But it's more practical than it used to be.
Learn how today's attacks unfold and where threat prevention can stop them, featuring the Unit 42 2025 Global Incident Response Report.
Download reportThreat prevention FAQs
Threat prevention is the practice of stopping cyberattacks before they cause harm. It uses security controls to block unauthorized access, malware, and exploitation attempts across systems, networks, and applications.
There’s no single standard list, but cyber threats are often grouped into categories like external attacks (e.g., malware, phishing), internal threats (e.g., insider misuse), supply chain risks (e.g., third-party compromise), and human error (e.g., misconfigurations or accidental data exposure).
Threat protection refers to the combined use of prevention and detection. It includes both stopping threats before they occur and identifying malicious activity in progress.
Threat detection identifies attacks after they bypass defenses. Threat prevention blocks them up front. Together, they reduce risk by preventing known threats and catching others that slip through.
Yes. Prevention reduces risk, but no control is perfect. Detection and response are still needed to catch, investigate, and contain threats that evade preventive measures.
Cyber threat prevention refers to the proactive steps taken to stop cyberattacks before they occur. It includes technical, identity, and behavioral controls that block malicious activity across systems, networks, and applications.