- 1. Why do experts disagree about when Q-Day will happen?
- 2. What would actually happen if Q-Day arrived tomorrow?
- 3. Why "harvest now, decrypt later" matters more than Q-Day itself
- 4. How close are we based on today's progress?
- 5. What are governments and standards bodies doing to prepare?
- 6. How to prepare for Q-Day (without overreacting)
- 7. Will Q-Day be a crisis, or a milestone we're ready for?
- 8. Q-Day FAQs
- Why do experts disagree about when Q-Day will happen?
- What would actually happen if Q-Day arrived tomorrow?
- Why "harvest now, decrypt later" matters more than Q-Day itself
- How close are we based on today's progress?
- What are governments and standards bodies doing to prepare?
- How to prepare for Q-Day (without overreacting)
- Will Q-Day be a crisis, or a milestone we're ready for?
- Q-Day FAQs
What Is Q-Day, and How Far Away Is It—Really?
- Why do experts disagree about when Q-Day will happen?
- What would actually happen if Q-Day arrived tomorrow?
- Why "harvest now, decrypt later" matters more than Q-Day itself
- How close are we based on today's progress?
- What are governments and standards bodies doing to prepare?
- How to prepare for Q-Day (without overreacting)
- Will Q-Day be a crisis, or a milestone we're ready for?
- Q-Day FAQs
"Q-Day" refers to the moment when quantum computers can break today's public-key cryptography.
It's not a calendar date but a milestone—one most experts expect in the 2030s or later. It marks the point when a cryptographically relevant quantum computer (CRQC) can run algorithms like Shor's to break RSA and elliptic-curve encryption, forcing a global shift to quantum-safe standards.
Why do experts disagree about when Q-Day will happen?
Experts disagree because there's no single path to building a cryptographically relevant quantum computer. The timeline depends on progress across several independent challenges.
Starting with hardware.
Different types of quantum computers use different physical approaches. Such as superconducting circuits, trapped ions, or photons. Each has its own trade-offs. Some can be built up quickly but are unstable. Others are more accurate but difficult to produce in large numbers. That's why progress varies by design.
Then there's error correction.
Quantum bits are fragile. They lose coherence in microseconds. That means a quantum computer can't simply add more qubits and expect better performance. To perform long calculations, millions of physical qubits must work together to create a few thousand logical ones. Estimates of when that will happen vary from the 2030s to beyond 2045.
Finally, algorithmic efficiency adds more uncertainty.
Breakthroughs in quantum algorithms—or classical countermeasures—could shift the timeline in either direction.
To put it simply, experts disagree because they're betting on different breakthroughs. Some focus on physics. Others on engineering. Others on math. Each discipline defines “close” differently.
Here's the consensus:
The exact date doesn't matter as much as the preparation window. The risk begins long before Q-Day itself, when stolen data can be stored now and decrypted later.
What would actually happen if Q-Day arrived tomorrow?
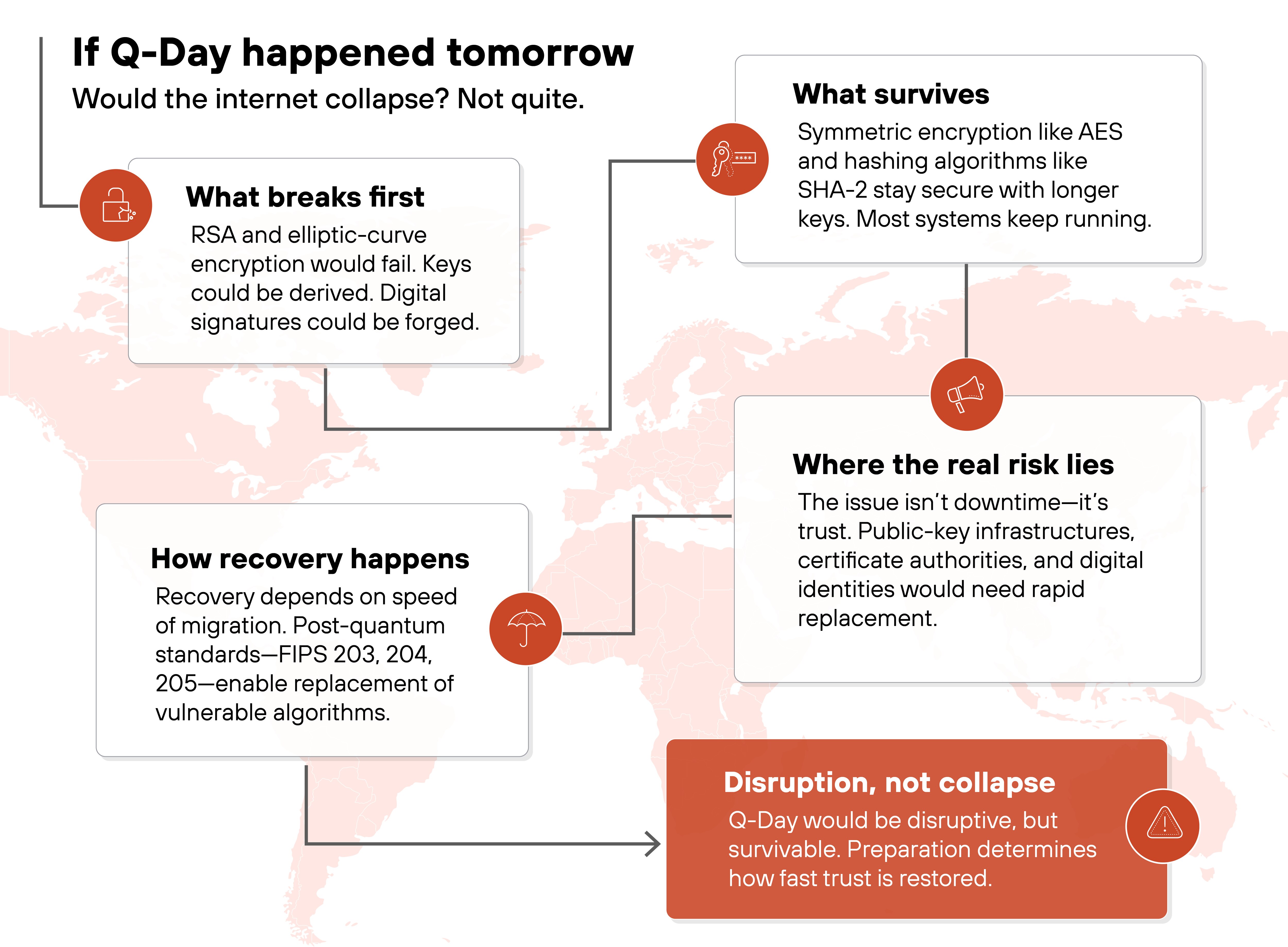
If Q-Day happened tomorrow, the internet wouldn't go dark. But encryption based on RSA and elliptic curves would no longer be secure.
Why?
Because a cryptographically relevant quantum computer could solve the math problems those algorithms rely on. Keys protecting everything from emails to VPNs could be derived. Digital signatures could be forged.
The first systems at risk would be those using older or static keys. Especially ones that secure data meant to stay private for decades. Think financial archives, intellectual property, and government records.
However:
This wouldn't mean instant chaos. Most symmetric encryption and hashing algorithms would remain safe with longer keys. Systems using AES or SHA-2 could continue operating if rekeyed appropriately.
The real concern would be trust.
Public key infrastructures, certificate authorities, and identity systems would all need immediate transition. Communication could continue, but verification would be uncertain until new keys and algorithms were deployed. And that's the primary quantum security risk.
In short:
Q-Day would cause disruption, not collapse. Recovery would depend on how quickly organizations could replace vulnerable algorithms with post-quantum standards finalized by NIST.
Why "harvest now, decrypt later" matters more than Q-Day itself
The real threat isn't Q-Day. It's what's happening before it.
Attackers are already collecting encrypted data today. They know that once quantum computers reach decryption capability, that data can be unlocked. Which means the information being stolen now—financial records, personal data, intellectual property—could be exposed years from now.
That's what “harvest now, decrypt later” means. It's the practice of stealing encrypted traffic today to decrypt it later with quantum computing.
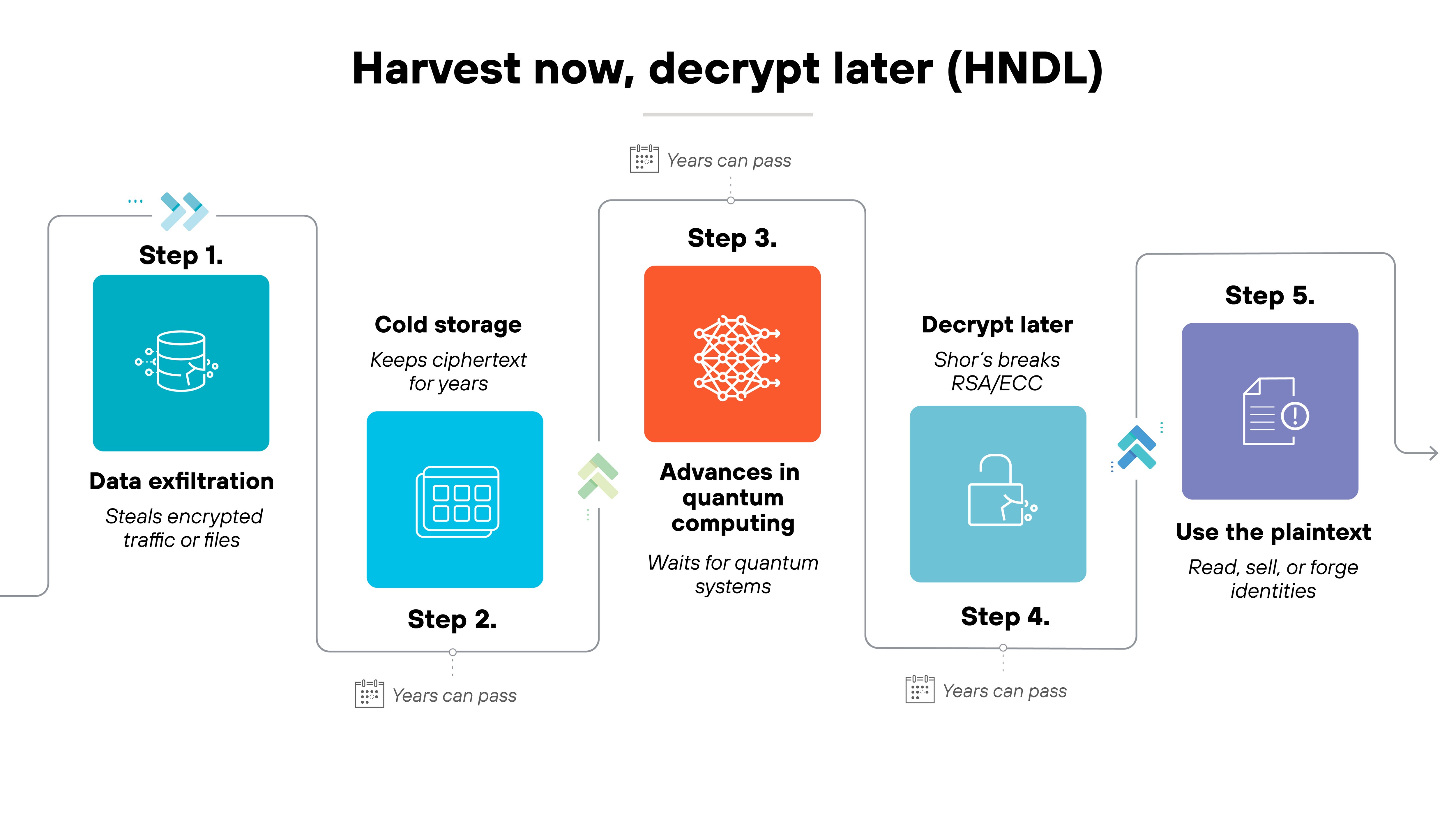
The risk is simple. Data with long confidentiality lifespans—like government archives, trade secrets, or medical research—will still matter when Q-Day arrives. So delaying migration increases exposure.
Important:
Quantum readiness isn't just about future encryption standards. It's about protecting what's already in motion.
How close are we based on today's progress?
We're not there yet—but we're getting closer. A cryptographically relevant quantum computer remains years, likely decades, away.
No one can pinpoint when Q-Day will happen. But current evidence gives a sense of scale.
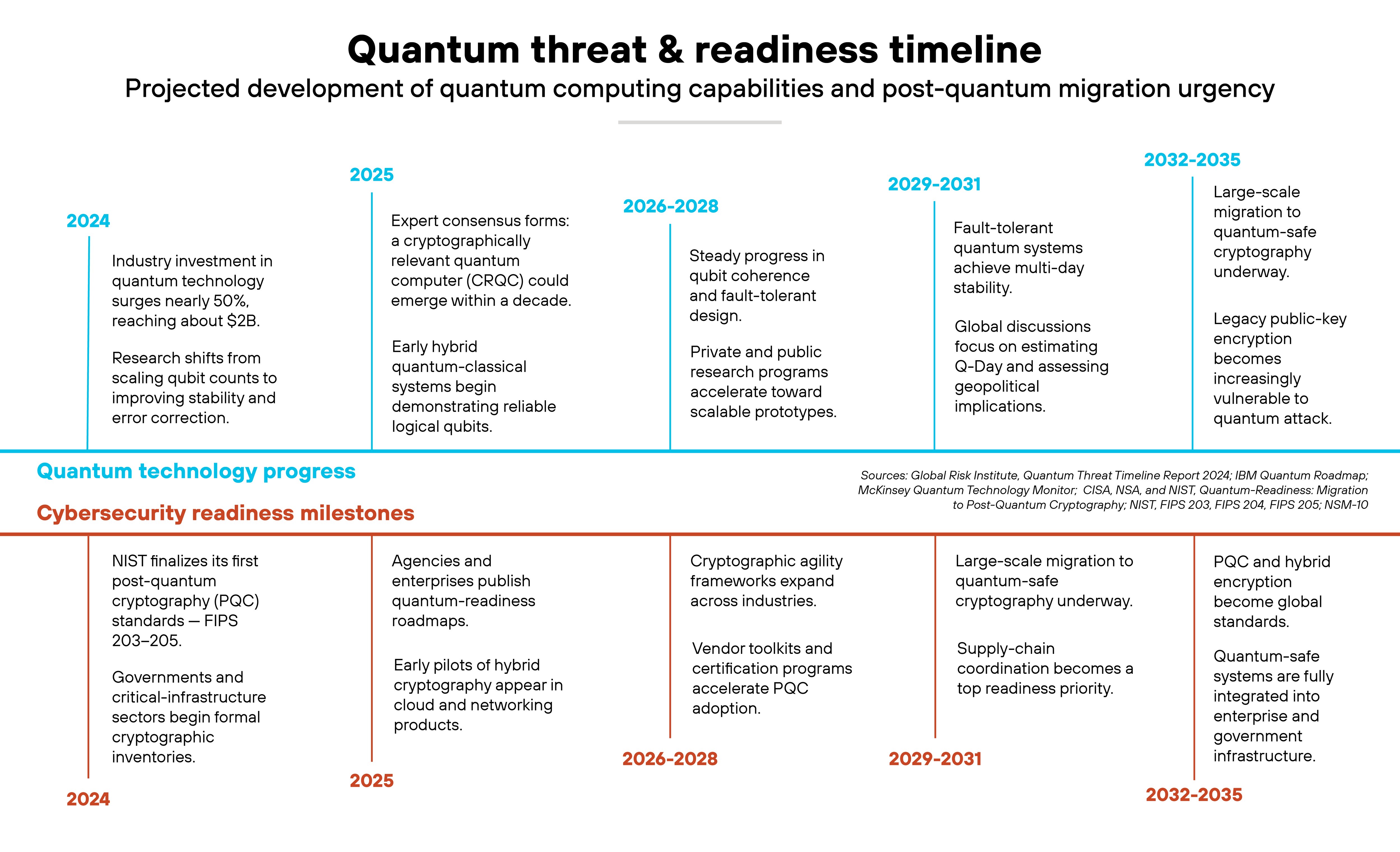
Let's consider the latest assessments.
The Global Risk Institute's Quantum Threat Timeline 2024 finds most specialists expect cryptographically relevant quantum computers sometime in the 2030s or later. Even in optimistic forecasts, the probability of such a machine arriving within ten years remains under 20%.
Recent technical progress supports that view.
Both the Quantum Threat Timeline 2024 and McKinsey's Quantum Monitor 2025 note measurable advances in qubit stability and error correction over the past year. But even with those gains, cryptographically relevant systems remain far off—requiring millions of fault-tolerant qubits, compared with the hundreds available today.
Migration planning is already under way.
Following the release of NIST's post-quantum standards in 2024—ML-KEM (FIPS 203), ML-DSA (FIPS 204), and SLH-DSA (FIPS 205)—governments and vendors began adopting these algorithms. It's worth noting, though, that readiness varies widely, with larger institutions beginning pilot deployments while others wait for regulatory deadlines.
Here's the key takeaway:
Q-Day isn't imminent, but it's not theoretical either. The point is that while a cryptographically relevant system is still decades away, the migration window is now. Transitioning this decade ensures data protected today will remain secure when that milestone finally arrives.
What are governments and standards bodies doing to prepare?
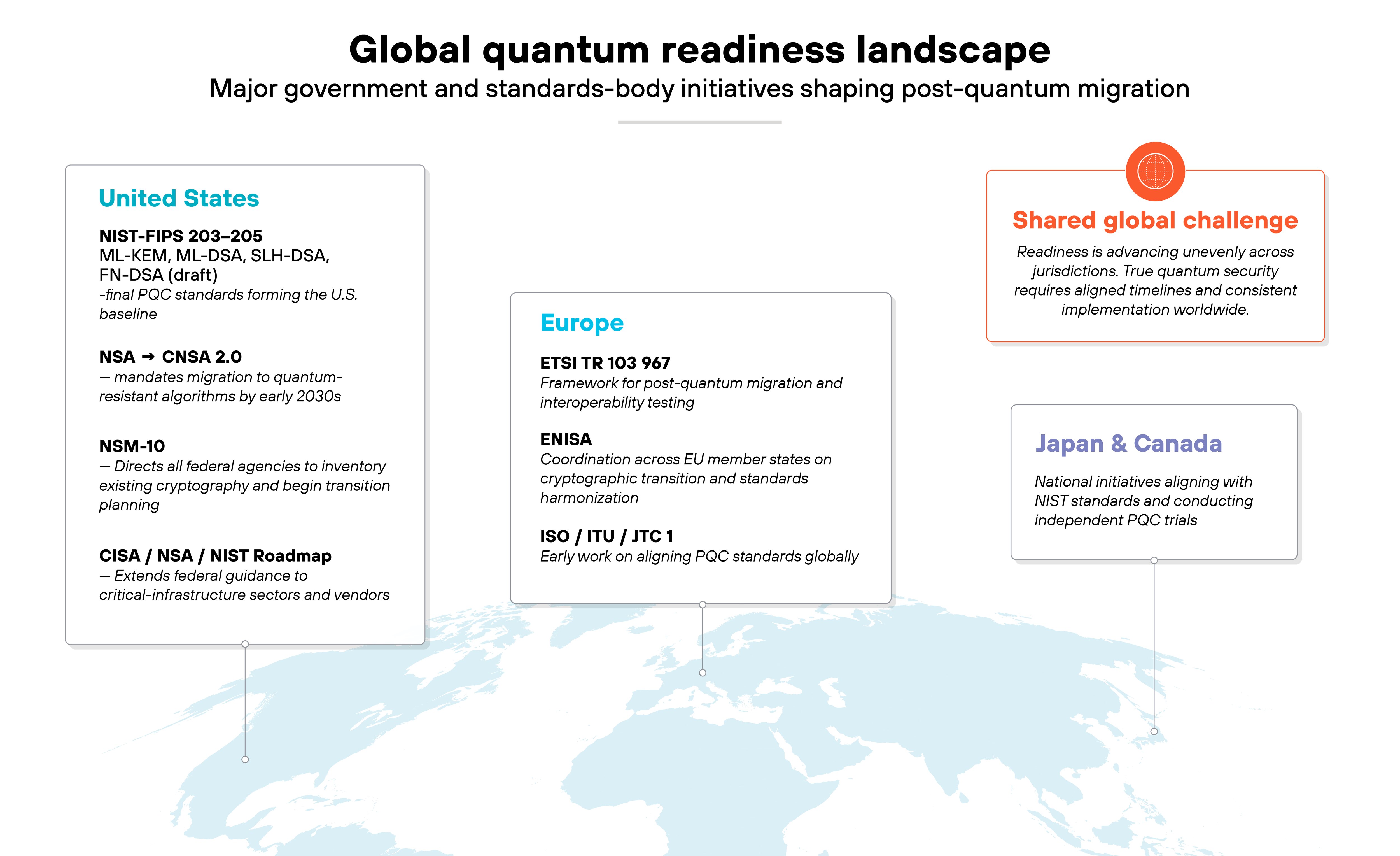
Governments and standards bodies are no longer just studying the quantum threat. They're executing coordinated migration plans.
As mentioned, in the United States, NIST has finalized the first post-quantum cryptography standards, FIPS 203-205:
- Module-Lattice-Based Key-Encapsulation Mechanism (ML-KEM)
- Module-Lattice-Based Digital Signature Algorithm (ML-DSA)
- Stateless Hash-Based Digital Signature (SLH-DSA)
ML-KEM, ML-DSA, and SLH-DSA are established as the new federal baseline. Those standards align with broader guidance in NIST SP 800-131A r3, which outlines the transition from classical to quantum-resistant algorithms.
Policy direction is equally clear.
As discussed, National Security Memorandum-10 requires all federal agencies to complete their post-quantum migration by 2035. The NSA's Commercial National Security Algorithm Suite 2.0 supports that goal, defining approved algorithm families and timelines for defense and national security systems.
This effort extends globally.
ENISA and ETSI are leading European initiatives to harmonize post-quantum adoption and interoperability. ISO/IEC 23837 defines shared testing and evaluation criteria for technologies such as quantum key distribution. The World Economic Forum has emphasized the governance side of quantum readiness, encouraging collaboration across industries and integrating quantum risk into existing cybersecurity strategies.
The direction is set. Global standards are converging, timelines are published, and implementation is underway.
What varies now is pace.
Some nations are ahead, others are still planning, but the transition to quantum-safe infrastructure has already begun.
For enterprises, that means migration planning must now align with these public timelines to avoid falling behind the broader shift.
How to prepare for Q-Day (without overreacting)
Quantum readiness isn't about panic. It's about preparation.
Start with leadership.
Accountability at the executive level ensures readiness isn't an isolated project.
Next comes visibility.
Organizations need a complete inventory of where and how cryptography is used across applications, APIs, and devices. Without that baseline, you can't prioritize what to protect or migrate.
Then triage.
Identify long-life data that must remain confidential for decades. Those assets should move first, since they're already vulnerable to harvest-now-decrypt-later exposure.
Focus on flexibility.
Crypto-agility lets you replace algorithms and keys without rebuilding entire systems. It's the foundation for adopting post-quantum standards safely.
Testing matters too.
Hybrid models that combine classical and post-quantum algorithms allow organizations to validate performance before scaling broadly.
Finally, governance keeps progress sustainable.
Define ownership for cryptographic management and align internal policy with emerging standards.
Ultimately, the goal isn't to future-proof everything overnight.
It's to build systems ready to evolve. So when Q-Day comes, migration is planned, not improvised. And the collective result of that preparation is what determines whether Q-Day becomes a crisis or a milestone we're ready for.
- Quantum Readiness: What It Means and How to Achieve It
- Cryptographic Agility: The Key to Quantum Readiness
Will Q-Day be a crisis, or a milestone we're ready for?
Q-Day won't be a single moment of collapse. It'll be a milestone that measures how well the world prepared.
The transition to quantum-safe encryption is meant to be managed. Not improvised. The algorithms, timelines, and coordination frameworks are already defined.
So:
When a cryptographically relevant quantum computer finally arrives, the systems built for flexibility will adapt. The ones that planned early will transition with minimal disruption.
In the end, Q-Day isn't a surprise waiting to happen. It's the predictable outcome of a process already in motion.
The challenge isn't the day itself. It's making sure readiness keeps pace with technology. Because preparation only matters if execution continues until the transition is complete.
