- 1. Why are organizations turning to hybrid cryptography?
- 2. How does hybrid cryptography actually work?
- 3. What kinds of hybrid cryptography exist?
- 4. How secure are hybrid schemes in practice?
- 5. Where is hybrid cryptography already being deployed?
- 6. How does hybrid cryptography fit into the quantum-security roadmap?
- 7. What's next for hybrid cryptography?
- 8. Hybrid cryptography FAQs
- Why are organizations turning to hybrid cryptography?
- How does hybrid cryptography actually work?
- What kinds of hybrid cryptography exist?
- How secure are hybrid schemes in practice?
- Where is hybrid cryptography already being deployed?
- How does hybrid cryptography fit into the quantum-security roadmap?
- What's next for hybrid cryptography?
- Hybrid cryptography FAQs
What Is Hybrid Cryptography? | The Bridge to Post-Quantum Security
- Why are organizations turning to hybrid cryptography?
- How does hybrid cryptography actually work?
- What kinds of hybrid cryptography exist?
- How secure are hybrid schemes in practice?
- Where is hybrid cryptography already being deployed?
- How does hybrid cryptography fit into the quantum-security roadmap?
- What's next for hybrid cryptography?
- Hybrid cryptography FAQs
Hybrid cryptography combines two or more cryptographic algorithms—typically one classical and one post-quantum—to protect data using the strength of both. Each algorithm performs its own operation, and their outputs are mathematically merged to stay secure if one fails.
Using approved key-combiners or key-derivation functions, it bridges classical and post-quantum systems.
Why are organizations turning to hybrid cryptography?
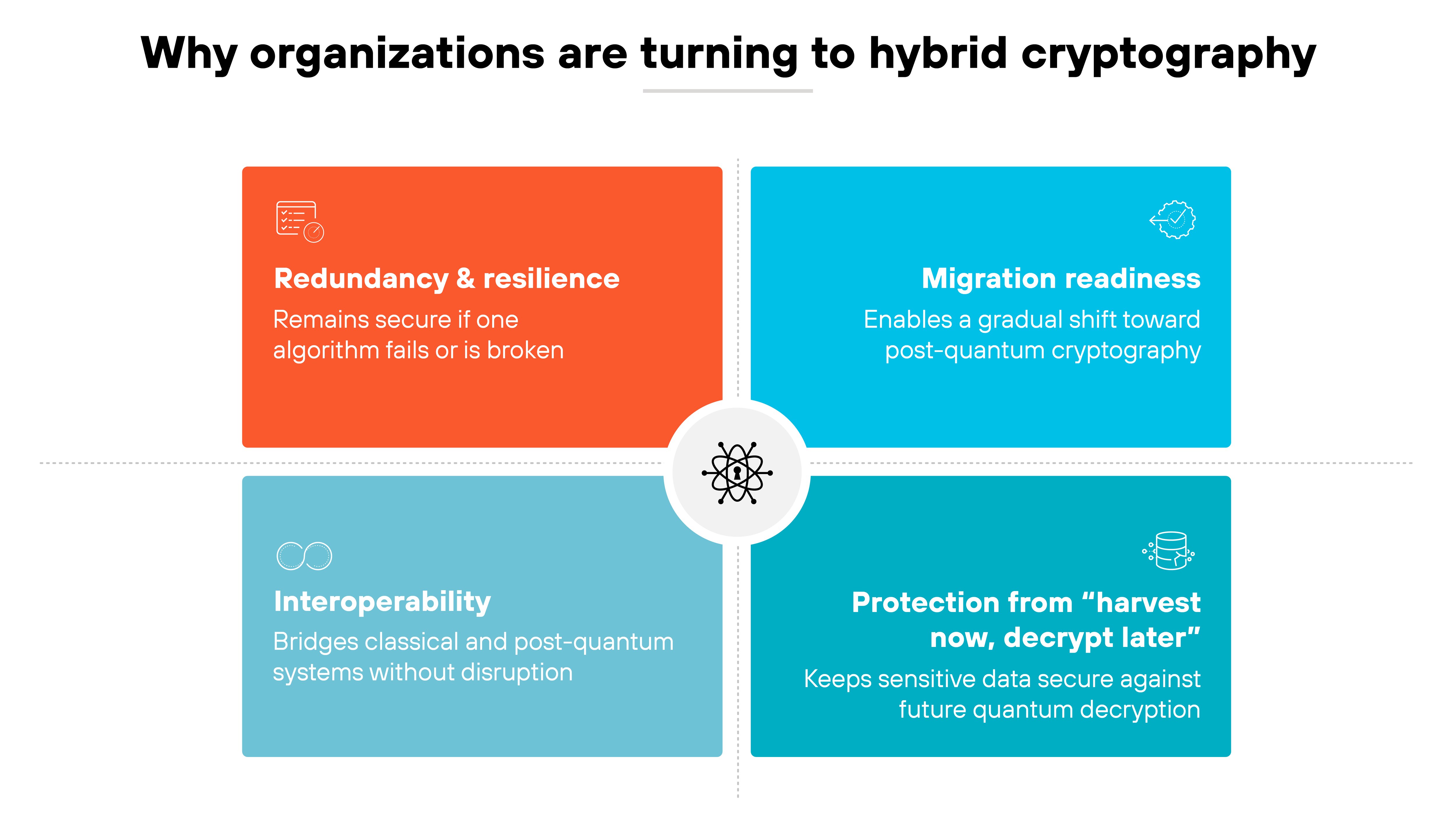
Organizations are turning to hybrid cryptography because it offers a practical bridge between today's classical systems and the post-quantum algorithms of the future. It's a transitional layer within quantum security.
More specifically:
Hybrid solutions make it possible to begin migration toward post-quantum cryptography (PQC) now, before it's fully standardized or deployed at scale. They allow encryption systems to evolve safely instead of waiting for a single, definitive cutover point.
Here's how it works.
Essentially, hybrid cryptography helps maintain security if one algorithm fails or is later broken.
So when a classical and post-quantum algorithm work together, each acts as a safeguard for the other. If the classical algorithm eventually becomes vulnerable to quantum attacks, the post-quantum algorithm continues to protect the data.
It also supports interoperability.
Many systems, devices, and protocols still depend on classical cryptography. Hybrid deployments let organizations upgrade gradually without breaking existing integrations or disrupting operations. And that makes them a practical choice for organizations and governments managing long, complex supply chains.
Finally, hybrid cryptography reduces exposure to the harvest-now, decrypt-later threat.
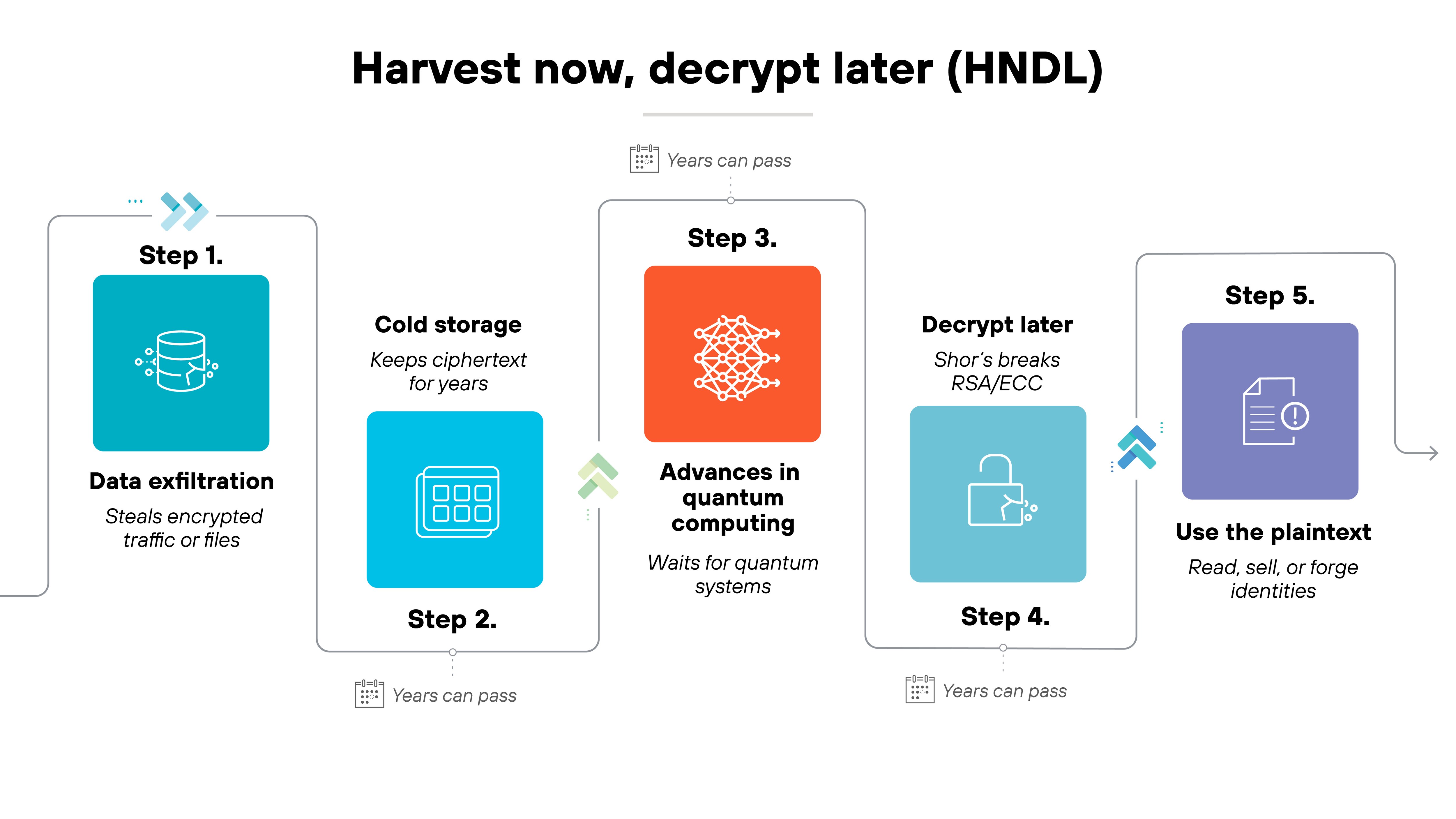
Attackers can already collect encrypted data today and wait until quantum computers are powerful enough to break it. With hybrid encryption, sensitive information remains secure even if decryption capabilities advance faster than expected.
In short:
Hybrid cryptography buys time. It keeps data protected, systems compatible, and transitions manageable while new post-quantum standards mature.
- What Is Q-Day, and How Far Away Is It—Really?
- What Is Post-Quantum Cryptography (PQC)? A Complete Guide
- 8 Quantum Computing Cybersecurity Risks [+ Protection Tips]
- Harvest Now, Decrypt Later (HNDL): The Quantum-Era Threat
How does hybrid cryptography actually work?
Hybrid cryptography works by combining two or more cryptographic algorithms into a single coordinated operation.
Each algorithm performs its own task—one classical, one post-quantum—and their outputs are merged to form a shared result. This allows systems to use the strengths of both without relying on either one completely.
Here's how it breaks down.
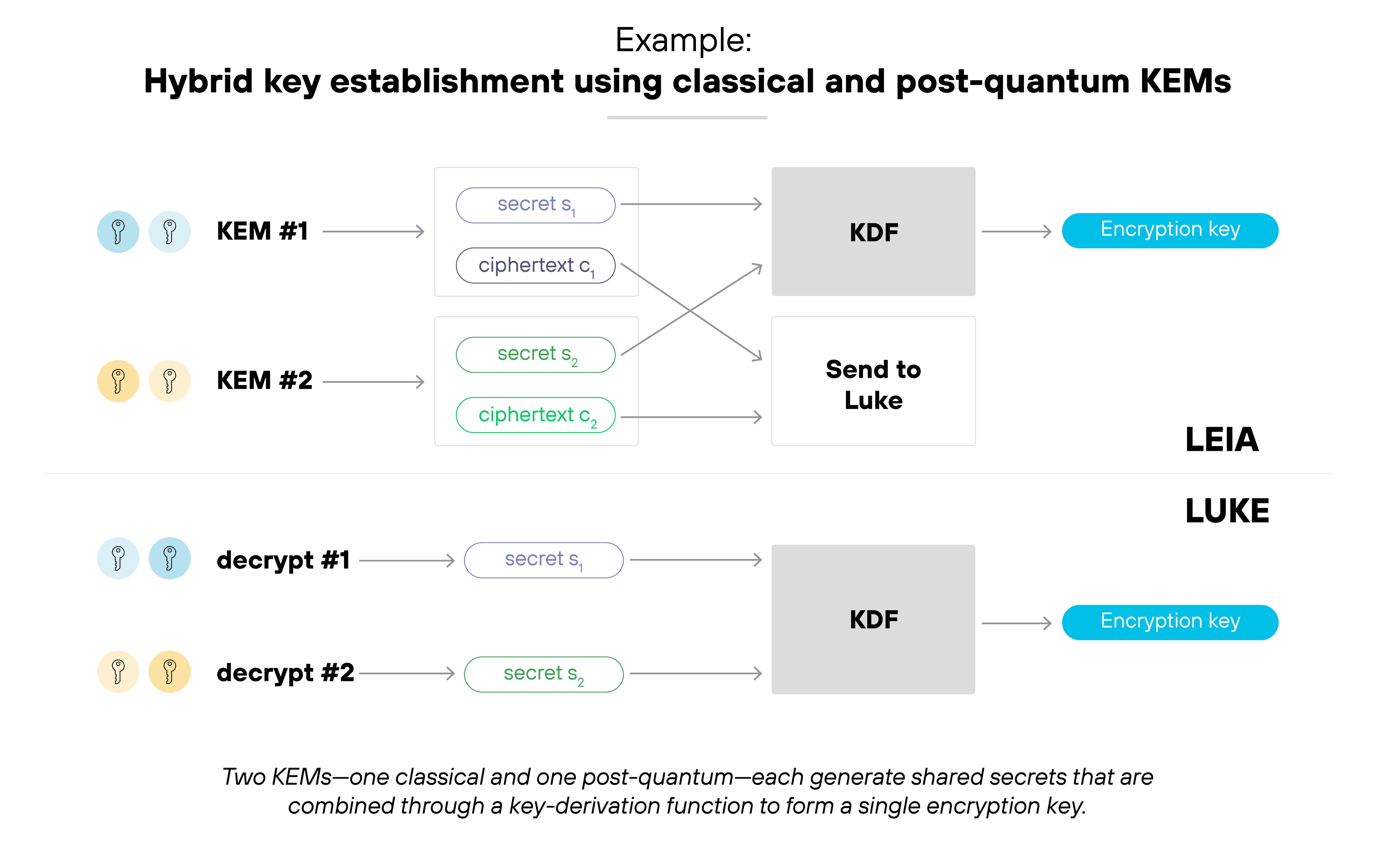
Hybrid key establishment uses classical and post-quantum key encapsulation mechanisms (KEMs) together.
Each KEM generates its own shared secret. The two secrets are then combined through an approved key-derivation function (KDF), creating one unified encryption key. This ensures that if one KEM is compromised, the other still protects the session.
Hybrid digital signatures take a similar approach.
A system can sign the same message with two algorithms—such as ECDSA and ML-DSA—and validate both signatures. In some cases, the signatures are stored separately. In others, they're merged into a single “composite” signature that behaves like one cryptographic object.
Hybrid protocols implement these techniques in real systems.
Examples include TLS, SSH, and MACsec, which can negotiate both algorithm types at the start of a secure connection. The protocol handles which combinations are used and how keys are exchanged.
Important: combining methods must follow approved key combiners or KDFs. That ensures the hybrid design remains mathematically sound and secure.
What kinds of hybrid cryptography exist?
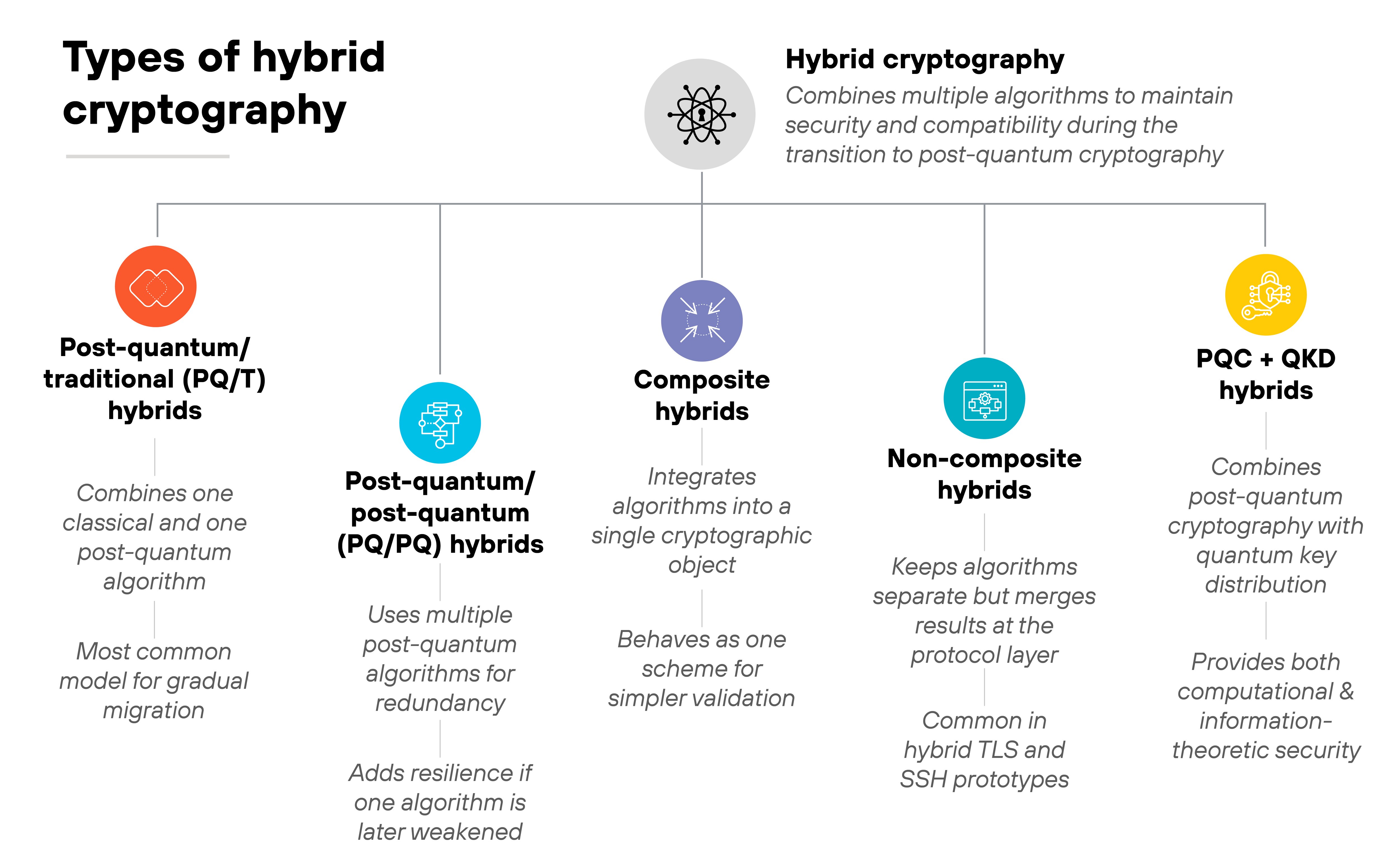
Hybrid cryptography takes several forms. Each is defined by how algorithms are combined and how their outputs are used together.
Recent standards define the main categories that have emerged as organizations transition from classical to post-quantum encryption.
Let's look at each type and how it works in practice.
Post-quantum/traditional (PQ/T) hybrids
A PQ/T hybrid combines one classical algorithm and one post-quantum algorithm in the same operation. Each performs its own key generation or signature process. Their results are then merged into a single shared secret or combined signature.
This is the most common model today because it maintains compatibility with legacy systems while adding quantum-resistant protection.
Post-quantum/post-quantum (PQ/PQ) hybrids
A PQ/PQ hybrid uses two or more post-quantum algorithms from different mathematical families.
The goal is redundancy. If one algorithm is later weakened, the other still provides protection.
This approach helps future-proof systems against unknown vulnerabilities in newly standardized post-quantum schemes.
Composite hybrids
A composite hybrid integrates multiple algorithms into one combined cryptographic object. Basically, the algorithms are bound together at the implementation level.
The resulting key, signature, or ciphertext behaves as if it were generated by a single algorithm, simplifying validation and integration.
Non-composite hybrids
Non-composite hybrids keep the algorithms separate but merge their results at the protocol layer.
For example, hybrid TLS or SSH sessions can negotiate both a classical and post-quantum key exchange, then combine the resulting secrets through a key-derivation function.
It's a modular approach that allows incremental deployment without changing underlying cryptographic libraries.
PQC + QKD hybrids
PQC + QKD hybrids represent the next frontier. They combine post-quantum cryptography (PQC) with quantum key distribution (QKD).
PQC protects data using computational hardness assumptions, while QKD provides information-theoretic security based on quantum physics. Used together, they offer layered defense for high-assurance environments.
How secure are hybrid schemes in practice?
Hybrid cryptography is designed to maintain security even if one of its component algorithms is compromised.
A properly implemented hybrid cryptographic scheme remains secure as long as at least one algorithm continues to hold. That's the foundational principle—redundancy through independence.
Each algorithm, whether classical or post-quantum, performs its own operation.
Their outputs are then combined to form a single shared secret or digital signature. If one algorithm is later broken, the other continues to protect the data. In other words, hybrid design provides a safety margin during transition, without forcing an abrupt switch to post-quantum methods.
Security depends heavily on how those outputs are combined.
Only robust combiners—typically hash-based or key-derivation functions—can provide formal assurance. These mechanisms set strict rules for how keys are joined so that the result remains unpredictable even if one component fails. Without such safeguards, the hybrid's theoretical guarantees weaken.
However:
Adding algorithms increases complexity.
More moving parts mean more surface for implementation error. Early hybrid TLS and SSH prototypes showed that message sizes increased, negotiations slowed, and handshake logic introduced new downgrade-attack risks.
In short: hybrid cryptography improves resilience, but its real-world security depends as much on careful engineering and protocol design as on the mathematics behind it.
Where is hybrid cryptography already being deployed?
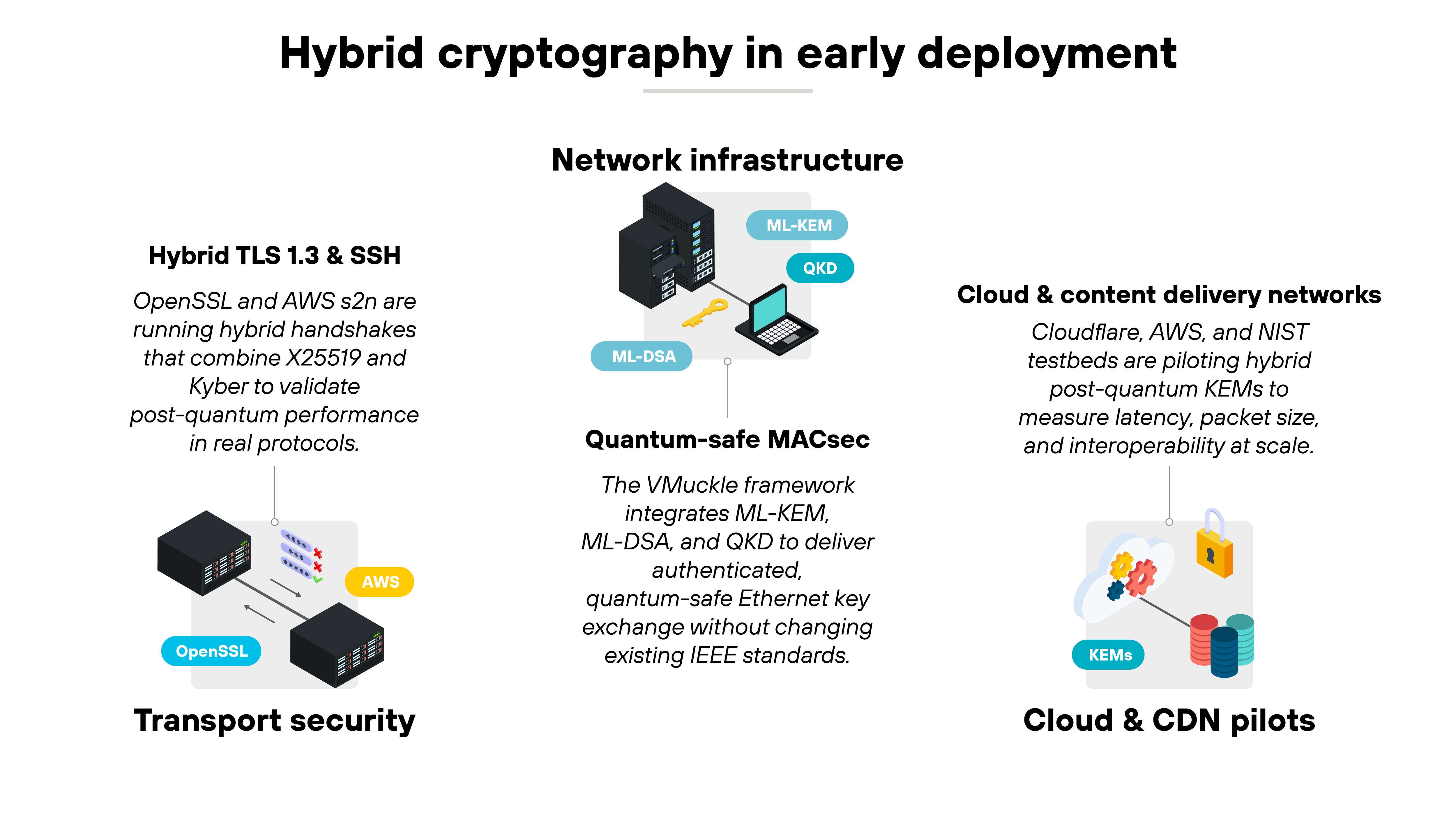
Hybrid cryptography is moving from research into early, real-world testing.
Most deployments today are experimental, but they already validate how hybrid algorithms interoperate and perform under production conditions.
Hybrid TLS 1.3 and SSH implementations
Early hybrid adoption has focused on transport security.
Projects like OpenSSL and AWS s2n have implemented hybrid versions of TLS 1.3 and SSH, pairing the classical elliptic-curve algorithm X25519 with the post-quantum scheme Kyber.
These pairings allow two endpoints to exchange both a classical and post-quantum key in the same handshake. And the results show that hybrid handshakes can run efficiently without major changes to existing protocol logic.
Quantum-safe MACsec
The VMuckle framework, developed by researchers at the Universidad Politécnica de Madrid and partners, extends hybrid cryptography to Ethernet.
It integrates ML-KEM, ML-DSA, and quantum key distribution (QKD) to create authenticated, quantum-safe key exchange for MACsec networks.
In testing, VMuckle provided long-term confidentiality and integrity without modifying the IEEE 802.1X or 802.1AE standards.
Cloud and CDN pilots
Cloud and content delivery providers are also experimenting with hybrid key exchange.
Cloudflare, AWS, and NIST testbeds have deployed hybrid post-quantum KEMs in select environments to assess latency, packet size, and reliability.
These trials demonstrate that hybrid configurations can protect traffic today while maintaining forward secrecy against future quantum attacks.
How does hybrid cryptography fit into the quantum-security roadmap?
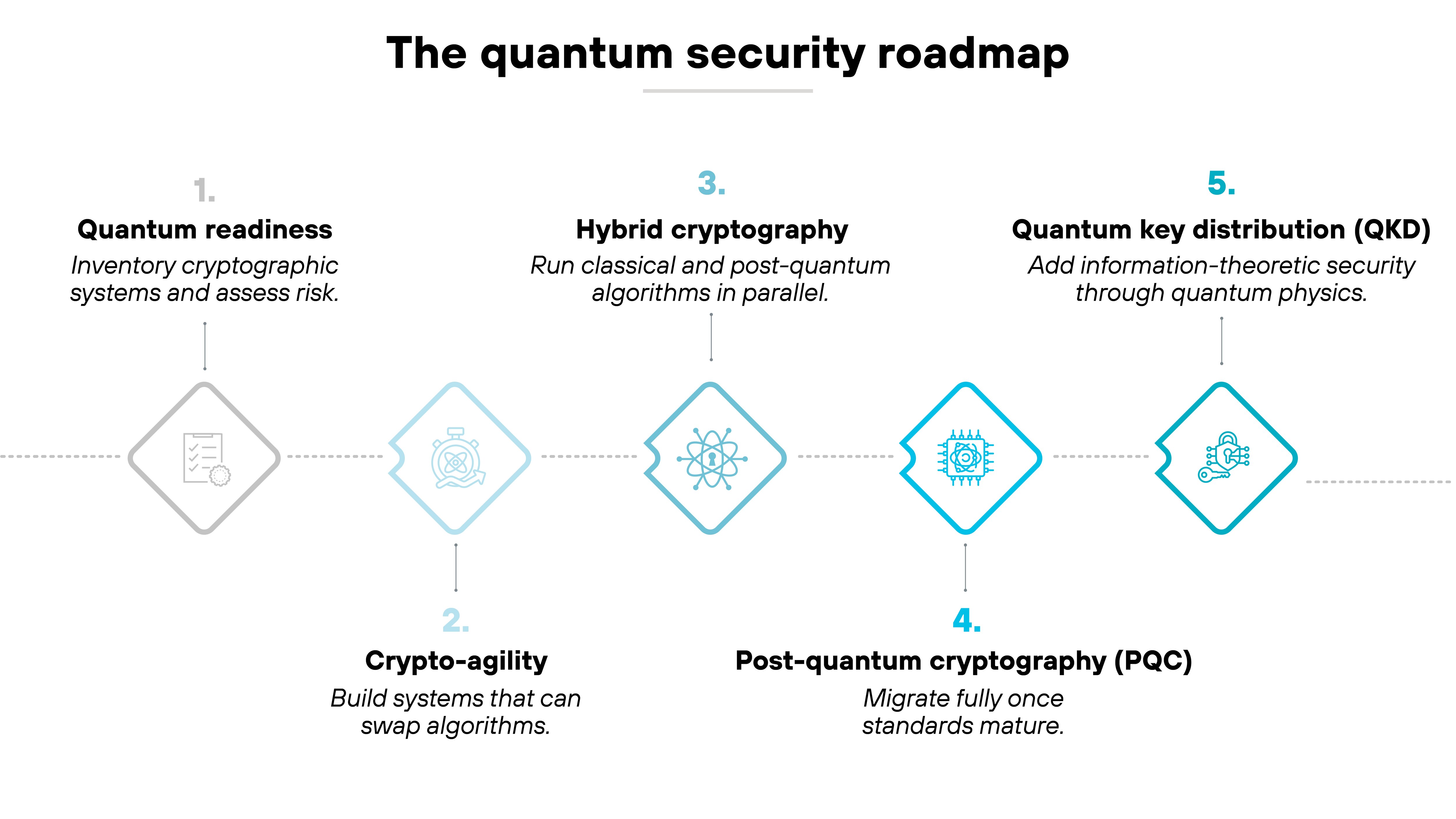
The path to quantum-safe security unfolds in stages.
It begins with quantum readiness—the process of identifying where classical cryptography is used and assessing what will need replacement. After that comes crypto-agility, which ensures systems can swap algorithms without major redesigns.
Hybrid cryptography sits at the midpoint of that journey.
As discussed, it allows classical and post-quantum algorithms to operate in parallel, maintaining protection during the transition. It's a temporary but expected step toward full post-quantum adoption by 2035.
Once post-quantum cryptography (PQC) is standardized and validated across major protocols, organizations can migrate entirely to PQC.
The final stage, quantum key distribution (QKD), extends security even further by introducing information-theoretic protection based on quantum physics.
Ultimately, hybrid cryptography bridges today's classical systems with the quantum-resistant future.
- Quantum Readiness: What It Means and How to Achieve It
- Cryptographic Agility: The Key to Quantum Readiness
What's next for hybrid cryptography?
Hybrid cryptography is entering a period of standardization and early adoption.
NIST SP 800-227 and RFC 9794 are stabilizing the definitions and implementation rules that will guide how hybrids are built and validated. This marks the shift from research-driven prototypes to formal, production-ready standards.
Proof-of-concepts are also moving into operational pilots.
Major vendors and research networks are now testing hybrid deployments across TLS, SSH, and MACsec. These trials help refine interoperability and performance before large-scale rollout begins.
Long-term, hybrid cryptography will give way to fully post-quantum systems.
Once PQC algorithms are standardized and widely deployed, hybrids will no longer be needed. But their legacy will remain. Hybrid designs are teaching the industry how to modernize encryption safely by evolving rather than replacing trust models outright.