Playbook of the Week: Manage Secrets and Protect Sensitive Data
Introduction
Information security teams rely on a variety of products and tools to manage their daily work. Each product typically has its own login details, creating a significant challenge for organizations. Managing multiple secrets across different platforms and sharing login details in a non-secure manner is a risky and time-consuming process. This lack of control over who can access sensitive information risks the organization.
Working with our customers at Palo Alto Networks, we understand the challenges of using multiple integrations and the need to provide login secrets when creating a new instance. This process involves sharing secrets openly from the system administrator and hard-coding them in Cortex XSOAR.
You can use a new integration with HashiCorp Vault to simplify and secure the secret management process. In this post, we will take a closer look at the benefits of using the HashiCorp Vault content pack for Cortex XSOAR, including how the integration works and a practical guidance for using it effectively.
What is HashiCorp Vault?
HashiCorp Vault is a tool for managing secrets. It provides a secure way to store and manage sensitive information, such as passwords, API keys, certificates, and other sensitive information. It uses encryption and access control mechanisms to ensure that only authorized users and applications can access these secrets.
In addition, instead of having secrets spread out across different systems and applications, HashiCorp Vault provides a centralized way to manage secrets. This can help to reduce the risk of exposure and make it easier to manage secrets at scale.
Benefits of the HashiCorp Vault content pack
The HashiCorp Vault content pack for Cortex XSOAR enables security operations center (SOC) teams to easily manage their secrets. With a range of 15 out-of-the-box commands available, you can gain full visibility into your environment's policies, secrets, and secret engines.
Moreover, this pack provides a powerful toolset that allows you to take swift action in the event of a security breach. If you suspect that your data has been compromised, you can quickly seal or unseal your vault, delete or undelete specific secrets, or disable specific engines to prevent further unauthorized access.
This integration also enables you to fetch the stored credentials and use them in Cortex XSOAR without hard coding or exposing the credentials. The credentials are fetched and cached in memory for 10 minutes by default and passed to the relevant executed integrations as part of the integration parameters.
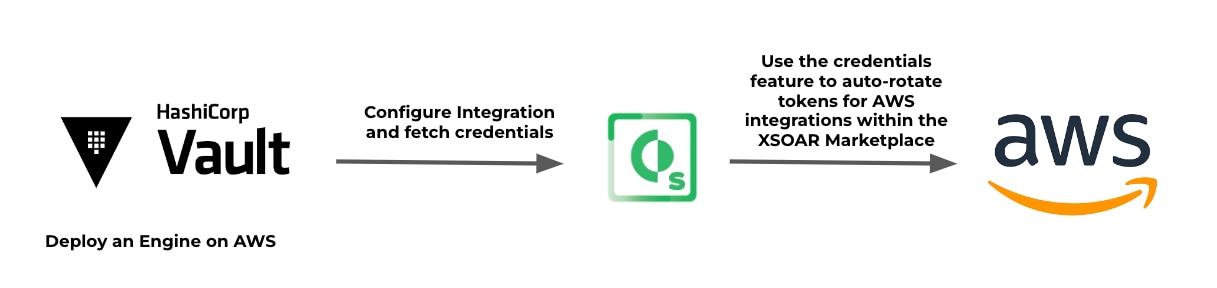
See it in action
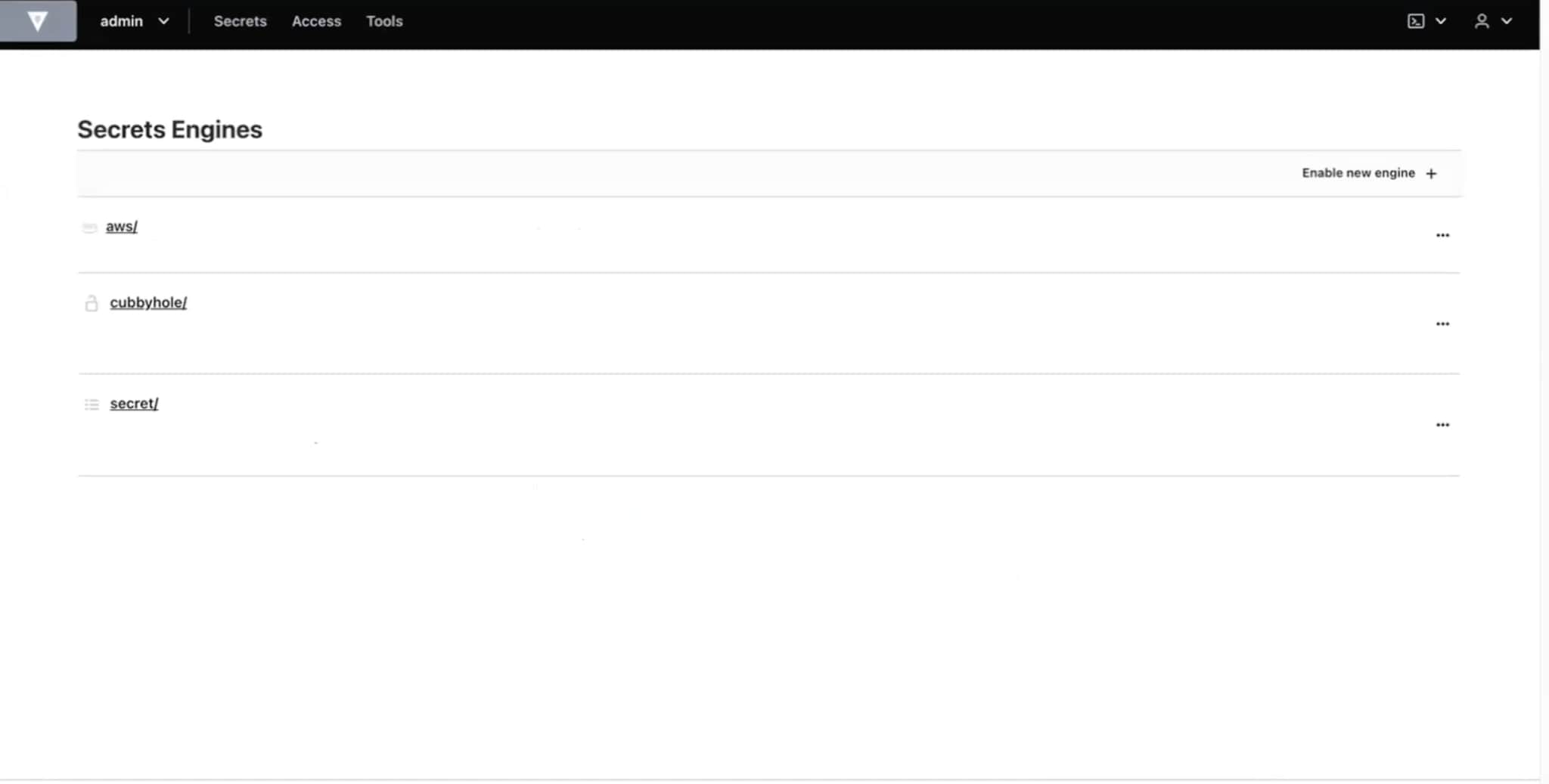
The first step is to configure the desired engines in the HashiCorp Vault platform.
You can use the page shown in the screenshot below or use the developer guide.
Please note: at this stage we only support the following engines: AWS, Cubbyhole, K/V Version 2
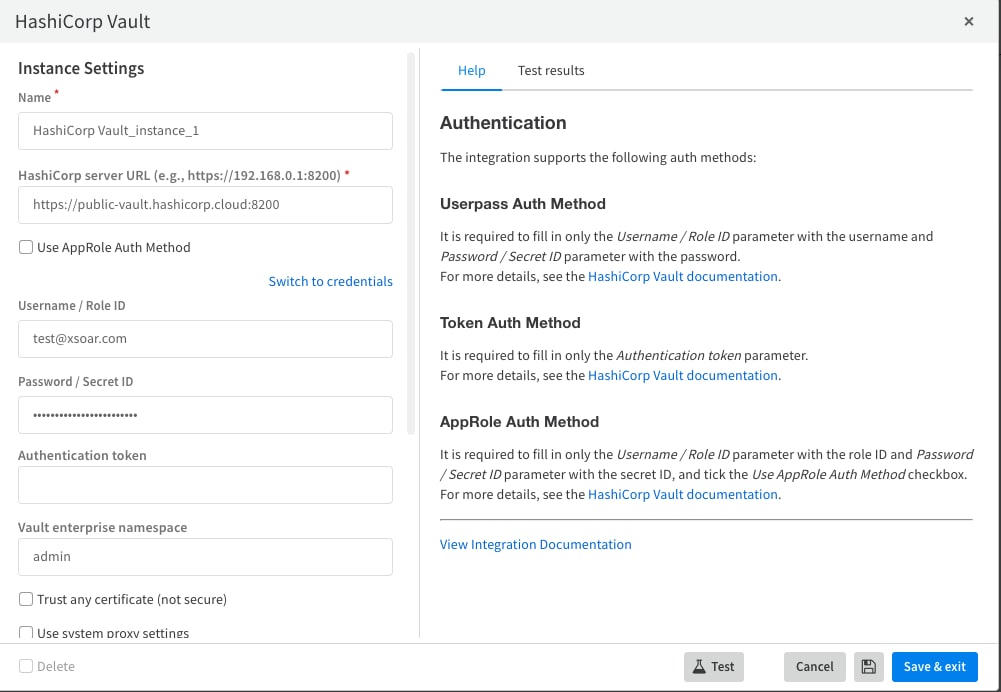
Next, we'll move on to configuring the instance of the HashiCorp Vault integration.
We will fill the login details according to the chosen authentication method (an explanation of the methods appears in the help section on the right).
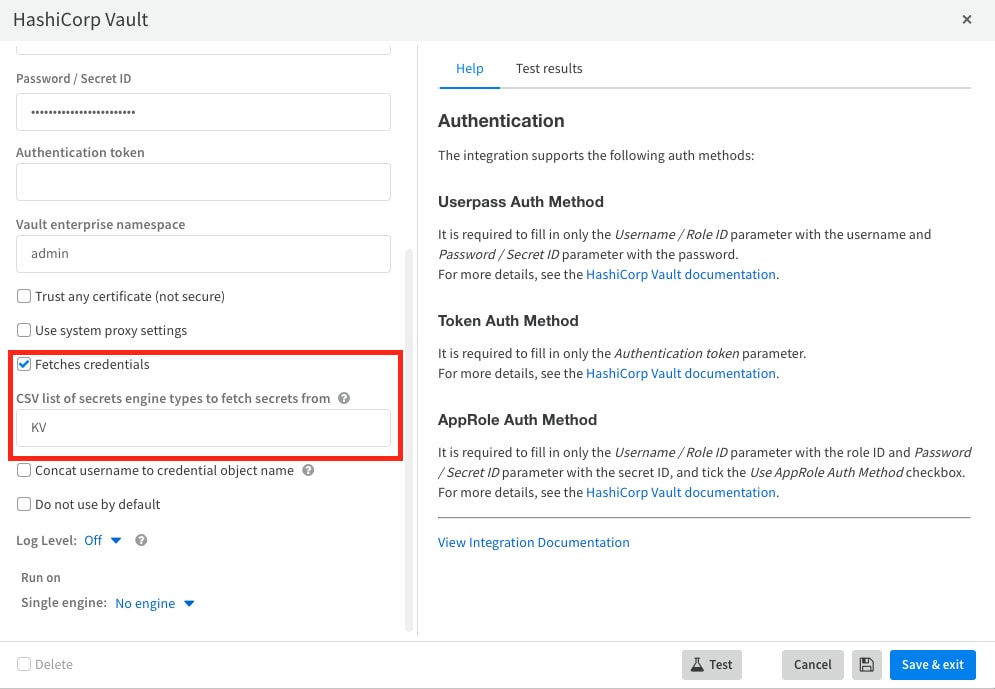
Then we will mark the "Fetches credentials" rubric and define the selected engine type.
Please note: we recommend defining one engine for each instance, if there are more engines you should separate them.
The last step is to run the hashicorp-configure-engine command, to insert the engine details in the context.
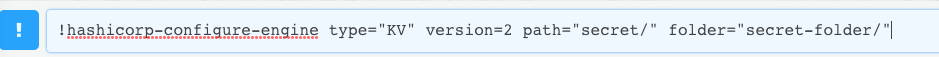
Now XSOAR has pulled all the secrets that exist in the HashiCorp environment, and you can see them under Settings -> Integrations -> Credentials.
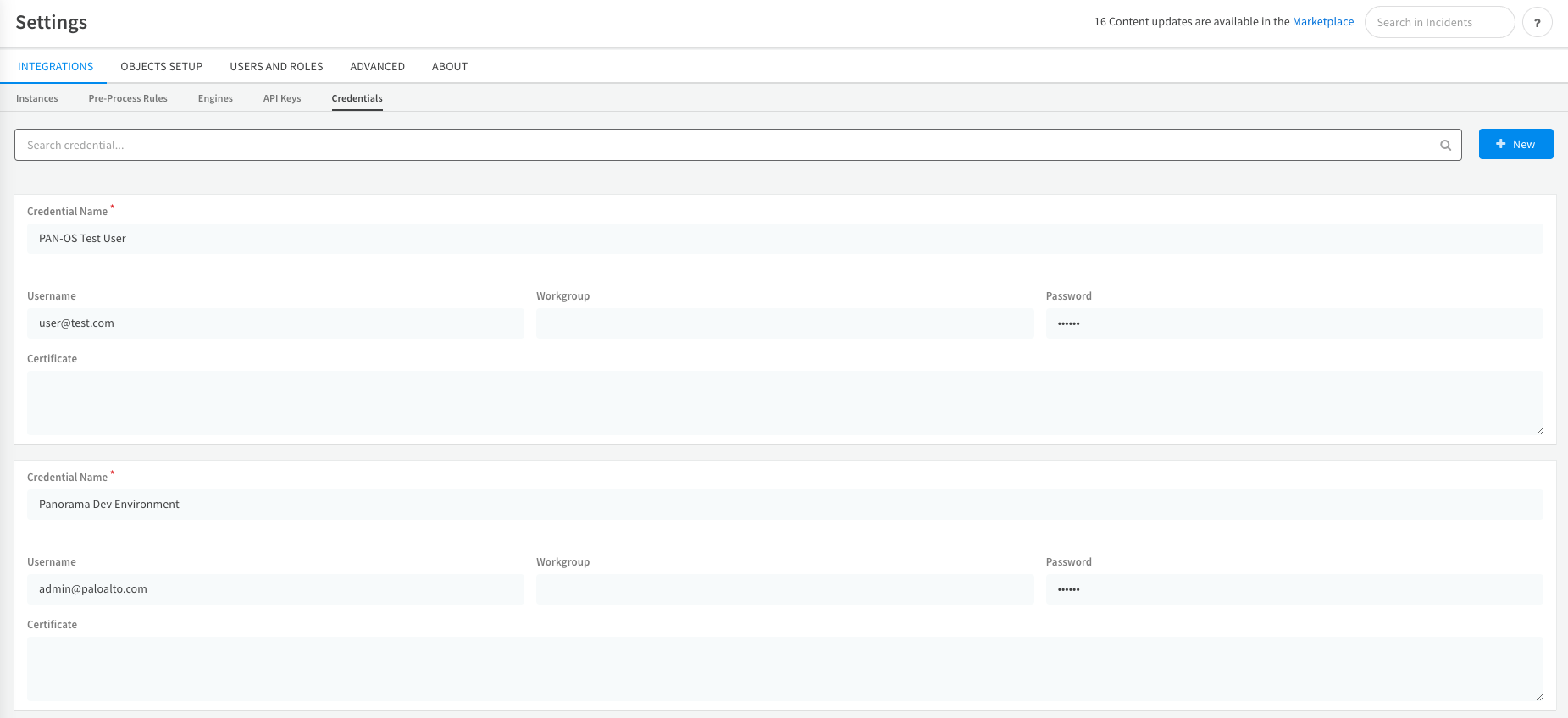
At this point, you can utilize values stored in XSOAR's cache when setting up a new instance of an integration or use in automations and playbooks.
Let's take the PAN-OS integration as an example to demonstrate this, in order to use these credentials in an integration, click Switch to credentials, and select the necessary credential from the drop-down menu.
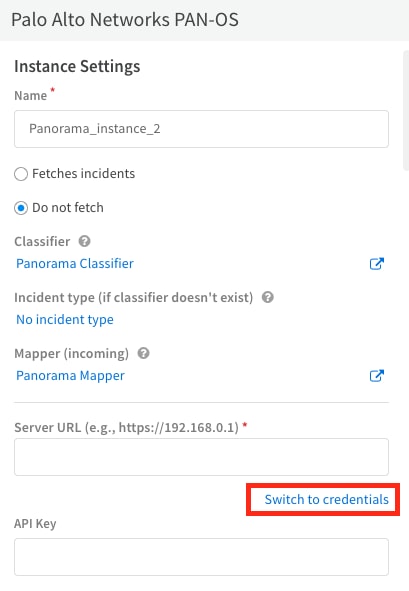
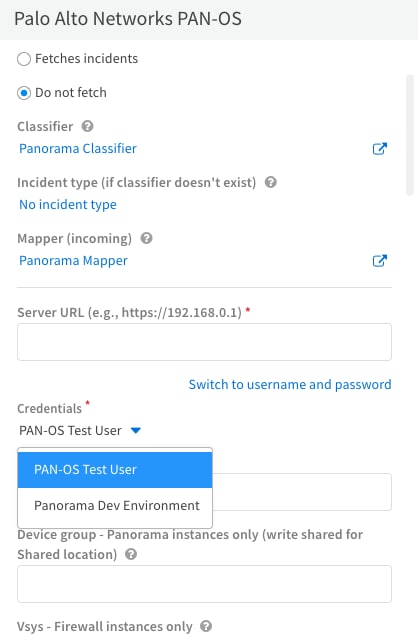
Conclusion
Integrating HashiCorp Vault with Cortex XSOAR can greatly enhance your organization's security and operational efficiency. By managing your secrets centrally and automating the process of securely retrieving them when needed, you can ensure that only authorized users and systems have access to sensitive information. This reduces the risk of data breaches and compliance violations, and allows your security teams to focus on more complex threats. With XSOAR's out-of-the-box integrations for HashiCorp Vault, you can easily incorporate this powerful secret management solution into your workflows, without the need for custom development. So if you haven't already, consider adding the HashiCorp Vault integration to your XSOAR platform and take your security to the next level.
To learn more about our most popular and unique XSOAR integrations, content packs and playbooks check out our Playbooks of the Week blog or visit the Cortex Marketplace.
Don’t have Cortex XSOAR? Download our free Community Edition today to test out this playbook and hundreds more automations for common use cases you deal with daily in your security operations or SOC.
Related Blogs
Subscribe to Security Operations Blogs!
By submitting this form, you agree to our Terms of Use and acknowledge our Privacy Statement. Please look for a confirmation email from us. If you don't receive it in the next 10 minutes, please check your spam folder.