Azure-Specific Policies to Detect Suspicious Operations in the Cloud Environment
Exploiting privileged operations for malicious intent is one of the biggest threats in the public cloud. Such operations allow bad actors to perform a range of attack techniques, such as lateral movement, credential access, and data exfiltration.
Imagine that a privileged user account has been compromised. The attacker might use the user’s permissions to remotely run commands to an active virtual machine and log into it. The attacker could then use the permissions of the machine to modify the routing tables in the network and directly access a remote server to perform data exfiltration.
In this scenario, organizations can be alerted to suspicious operations at many stages of the attack. The activity of a user executing a RunCommand operation points to lateral movement, while the activity of a virtual machine modifying the network route table indicates defense evasion.
The timely detection and containment of security threats rely on anomaly policies that issue high-fidelity alerts for suspicious operations — and free security teams to investigate and remediate critical incidents.
Introducing New Anomaly Detection Policies
In our ongoing expansion of threat detection capabilities, as we keep pace with the evolving threat landscape, Prisma Cloud has added eight new anomaly policies to detect suspicious operations for Azure® environments.
Of the eight policies, six focus on activities originating from Azure compute workloads, and the remaining two policies focus on activities originating from Azure users. Based on policy results, security alerts are triggered, with operations detected having a high fidelity for malicious activity.
Azure Compute Workload Assigning Roles to Resources
This policy detects an Azure Compute workload assigning a role to a resource, resource group, or subscription. Azure provides mechanisms to define and assign roles to control elevated permissions. Adversaries may circumvent these mechanisms to gain higher-level permissions.
Azure Compute Workload Modifying Key Vault Configurations
Attackers commonly attempt to steal secrets to elevate their permissions. The modifying Key Vault configurations policy detects when an Azure Compute workload attempts to alter the configuration of a key vault. The Azure Key Vault is a cloud service for securely storing and accessing secrets, like encryption keys and passwords.
Azure Compute Workload Deleting Network Security Groups
This detection alerts you to an Azure Compute workload that’s deleting network security groups. Azure network security groups contain security rules to filter network traffic between Azure resources in an Azure virtual network. Attackers routinely attempt to delete these groups to allow traffic to flow through.
Azure Compute Workload Disabling Azure Alerts
This policy detects an Azure Compute workload by deleting Azure Monitor alert rules. An Azure monitor alert rule monitors your telemetry and captures a signal that indicates that something is happening on the specified resource. Adversaries may attempt to delete these rules to avoid getting detected.
Azure Compute Workload Creating or Modifying Route Tables
This policy detects an Azure Compute workload creating or modifying Azure routing tables. Azure routing tables are used to route traffic between Azure subnets and virtual networks. Adversaries attempt to compromise these routing tables to divert traffic to their desired destinations.
Azure Compute Workload Disabling Antimalware Extensions
This policy detects an Azure Compute workload disabling antimalware extensions. Antimalware for Azure is a protection capability that helps identify and remove viruses, spyware, and other malicious software. Attackers often attempt to disable these extensions in order to deploy malware.
Azure User Reading Database Master Keys
This policy detects an Azure user reading master keys from Cosmos DB. The Azure master database key is a symmetric key used to protect the private keys of certificates and asymmetric keys present in the database.
Azure User Executing Remote Commands on Virtual Machines
This policy detects Azure users executing commands remotely on a virtual machine.
The above eight policies provide valuable additional context in the alerts, such as the number of failed and successful attempts, source IP addresses, and sample event IDs to help with the investigation and alert handling.
Policy Dashboard
To view or enable the anomaly detection policies, please navigate to Policies, select Overview, and then filter specifically for Policy Type = ‘Anomaly’, Policy Subtype = ‘UEBA’, and Cloud = ‘Azure’.
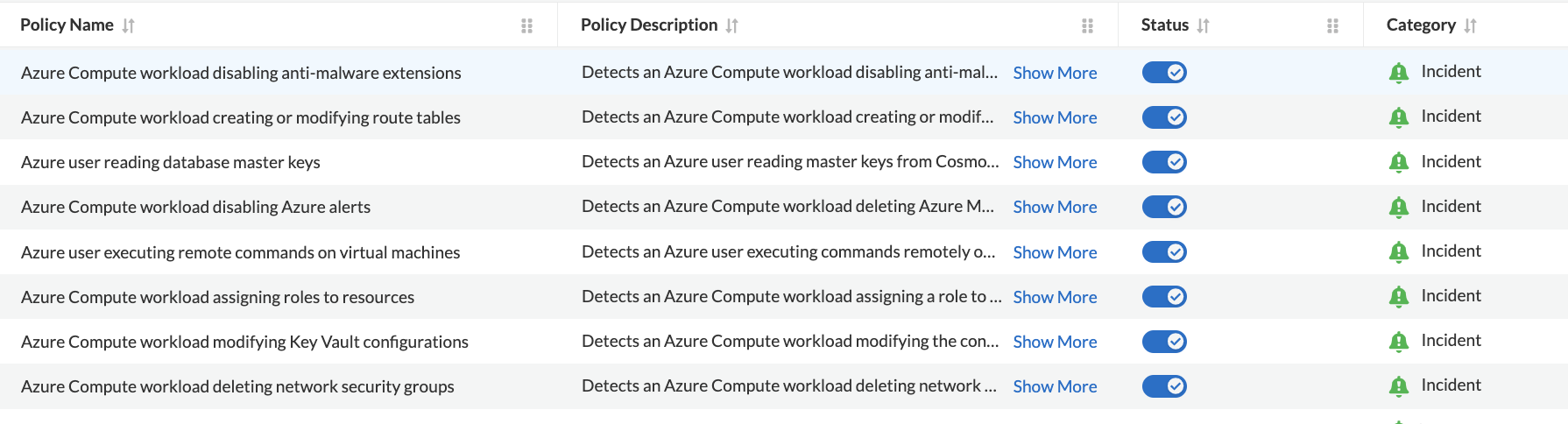
When audit logs from Azure cloud accounts are ingested, and the eight anomaly policies are enabled, alerts for these policies will trigger when a suspicious operation is performed — specifically when:
- An Azure compute workload employing potential privilege escalation or defense evasion tactics is detected
- An Azure user is suspected of using credential access or lateral movement tactics
Trusted List Support:
- Role-Based Trusted List: With the addition of these policies, you also have the ability to specify a role in a trusted anomaly list to suppress alerts. For the matching role names added to this trusted list, the specified anomaly policies will not generate alerts.
- Subject-Based Trusted List: The alert can also be suppressed by adding subjects to a trusted list and selecting applicable policies from the list.
Learn More About Anomaly Detection
Discover how to protect Microsoft Azure environments with comprehensive cloud security posture management (CSPM) — including support for the CIS Microsoft Azure Foundations Benchmark — and cloud workload protection (CWP) for hosts, containers, and serverless deployments. Prisma Cloud for Microsoft Azure offers cloud-native security and compliance throughout the development lifecycle.
Related Blogs
Subscribe to Cloud Native Security Blogs!
By submitting this form, you agree to our Terms of Use and acknowledge our Privacy Statement. Please look for a confirmation email from us. If you don't receive it in the next 10 minutes, please check your spam folder.