From Log4j and Beyond: 3 Ways CN-Series Protects Containers
This post is also available in: 日本語 (Japanese)
Since the Log4j vulnerability was detected in December 2021, security teams have rushed to identify and patch their vulnerable applications. Because Java is used everywhere and many applications rely on open source libraries dependent on Log4j, even applications that don't use Log4j directly may be vulnerable. Due to this vulnerability, attackers can contact any LDAP or JNDI server and execute any Java command on the victim device to steal data, install malware or take full control of the victim’s system. Estimates state that up to 3 billion devices, on both corporate and home networks, are affected. Even though many companies started patching the vulnerability immediately, it could take weeks to even months to patch all vulnerable applications since large companies have hundreds of vulnerable applications in both the cloud and on-premises.
Log4j is far from the first unknown critical vulnerability to be unearthed and will certainly not be the last. Vulnerabilities are prevalent and dangerous, however, there are ways to stop both known and unknown attacks. Here are the three ways CN-Series Container Firewalls provide Layer-7 runtime protection for your containers for both known and unknown vulnerabilities.
1. CN-Series prevents data exfiltration from Kubernetes environments:
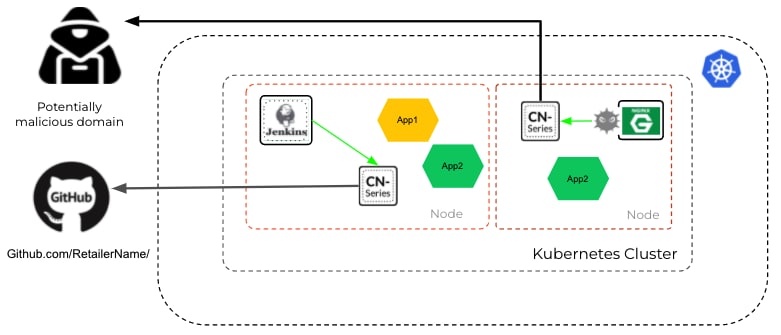
For vulnerabilities like Log4j, an important part of an attack is to communicate externally to malicious domains to exfiltrate data and establish a command-and-control (C2) relationship. CN-Series, when used in conjunction with URL Filtering and DNS security subscriptions, provides visibility and enforcement at an application level. Additionally, DNS security subscription constantly monitors and blocks connections with known and unidentified malicious domains (websites) and ensures customers’ sensitive data stays within the organization. Thus, CN-series customers are protected against Log4j as well as other known and unknown vulnerabilities without any manual intervention.
2. Protection against unknown threats/CVEs without manual intervention:
Although security teams have been working around the clock to patch the Log4j vulnerability, the CVE-2021-44832 patch will only protect them from attacks targeting this specific and known vulnerability. There are numerous vulnerabilities that have not been discovered yet, meaning that even “up-to-date” organizations can still be attacked through vulnerability exploits.
To detect and protect against zero-day attacks, organizations need global security that is always on. Deploy-time (shift-left) security products help to identify and secure instances, devices, and hosts that are vulnerability-free and configured properly. In contrast, Layer-7 ML-Powered Next-Generation Firewalls prevent the core parts of a network attack by identifying and blocking malware, suspicious protocols, and connections to malicious and/or unknown domains. That’s not to say that shift-left security isn’t important. Reducing the attack surface is a best-practice step in cybersecurity. However, for end-to-end container security, a ML-Powered Next-Generation Firewall is necessary to block the inevitable holes.
3. Granular level control and policies for East-West and Inbound traffic protection:
It is unrealistic for security teams to always patch every single application since it takes time to identify the vulnerability, develop a patch and then roll out the patch. However, to ultimately compromise an organization, attackers need to push malware onto victims, exfiltrate data or beacon out for further instructions.
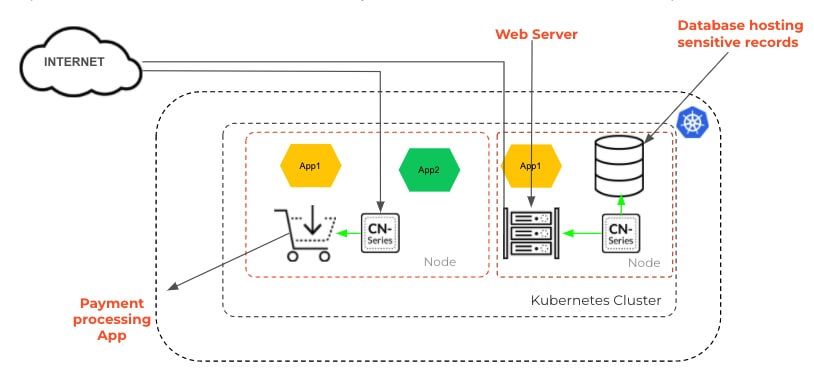
CN-Series keeps organizations safe by inspecting and controlling traffic between the two applications running on the same Kubernetes cluster (East-West traffic protection), as well as the incoming traffic to the specific application from the internet (Inbound traffic protection). For both East-West and inbound traffic protection, CN-Series uses both the Threat Prevention (TP) and WildFire (WF) subscriptions to block malware, spyware, vulnerability exploits, and file-based threats that exploiters may attempt to sneak into your network, affording security teams the time to focus on their security posture instead of the never ending patch-work.
Log4j will not be the last unknown critical vulnerability. With these types of vulnerabilities prevalent throughout the industry, it’s important to learn ways to protect your containers against both known and unknown attacks. To learn more about how CN-Series Container Firewalls can help you protect your containerized workloads, download our eBook, Protect Kubernetes Environments with CN-Series Firewalls, or explore CN-Series on Qwiklabs.
About the Log4j Vulnerability
To stay on top of the latest Log4j analysis and mitigation, as well as the latest vulnerability updates, please continue checking the Unit 42 blog or view the on-demand replay of the Unit 42 Briefing: Apache Log4j Threat Update.
Related Blogs
Subscribe to Network Security Blogs!
By submitting this form, you agree to our Terms of Use and acknowledge our Privacy Statement. Please look for a confirmation email from us. If you don't receive it in the next 10 minutes, please check your spam folder.