Attackers no longer strike in isolation. In cloud-native environments, they orchestrate multistage campaigns that move laterally across workloads and vertically through cloud control planes. For teams running Kubernetes clusters in the cloud, an attack that begins in a containerized workload can escalate fast — breaching nodes, extracting credentials and gaining access to sensitive infrastructure.
Weekly code deployments now define the norm for 77% of organizations, creating a fast-moving attack surface that traditional security tools can't keep up with. Point solutions detect fragments of suspicious behavior but fail to connect events across the full attack chain.
In this blog post, we walk through a realistic Kubernetes attack that crosses security domains — application, container, host, cloud and identity. It also shows how Cortex® Cloud detects the attack in progress, correlates activity across the kill chain, and enables rapid investigation and prevention through a unified platform approach.
The Attack Scenario: Bank App Compromise
A fictional financial institution runs its core banking platform on a Kubernetes-based microservices architecture deployed in AWS EKS. Its security team is about to face a multistage attack that exploits systemic gaps across the stack.
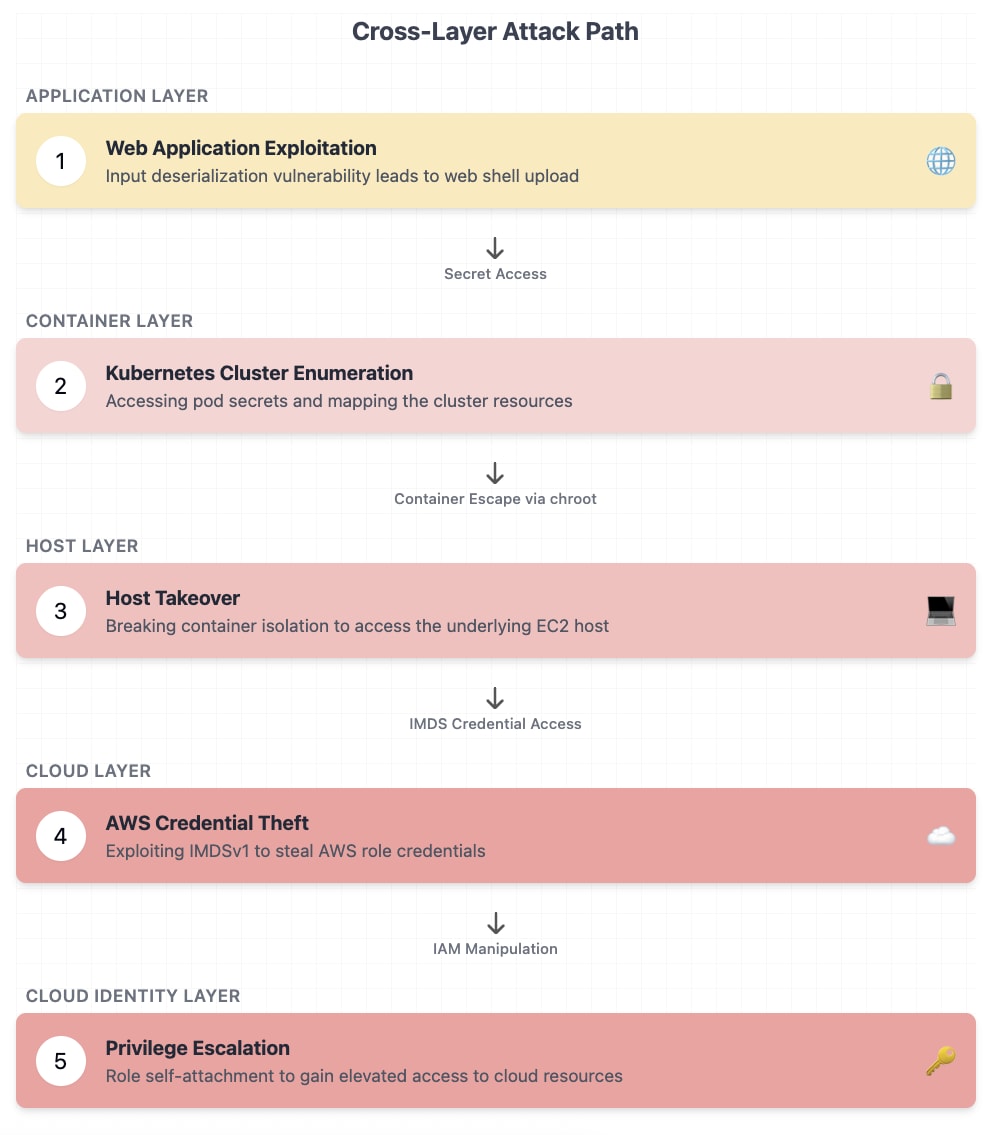
What Makes the Attack Sophisticated
Traditional security tools operate in isolation. Container security tools monitor pods. Cloud security tools evaluate configuration and IAM policies. Network tools inspect traffic. None of them alone can surface a threat that moves across layers.
This attack crosses five distinct control planes:
- Application Layer: Begins with an input deserialization vulnerability in a containerized workload
- Container Layer: Escapes isolation to gain unauthorized access to the host
- Host Layer: Exploits the underlying EC2 node
- Cloud Control Plane: Harvests AWS credentials through the instance metadata service
- Identity Layer: Abuses IAM to escalate privileges and persist in the environment
Without unified visibility, a security team would need a stack of siloed tools — WAF, CWPP, host intrusion detection, cloud detection and response, UEBA — and still struggle to correlate the evidence. Signals stay disconnected. Analysts stay blind to the full chain of compromise.
Attack Progression: Step-by-Step Breakdown
Stage 1: Initial Access
The attacker exploits an input deserialization flaw in a containerized web application, using crafted HTTP requests to upload and execute a web shell.
Stage 2: Cluster Reconnaissance
With access to the pod, the attacker runs curl commands to interact with the Kubernetes API server, extract secrets from other pods, and map the cluster.
Stage 3: Container Escape
Using a chroot escape, the attacker breaks out of the container and gains access to the underlying EC2 host.
Stage 4: Credential Theft
From the host, they query the IMDSv1 endpoint to extract temporary AWS credentials linked to the EC2 instance’s IAM role.
Stage 5: Privilege Escalation
They enumerate permissions and perform a role self-attachment to grant elevated access to AWS resources.
The Challenge of Fragmented Security
Had the bank’s team relied on traditional point solutions, the attack likely would have gone undetected or been misdiagnosed entirely.
- Web Application Firewall may have flagged the deserialization attempt but lacked visibility into the web shell's post-exploitation activity.
- Container Security could have surfaced unhusual pod behavior but missed the container escape and cloud interaction.
- A Host Intrusion Detection System might have detected the escape but failed to correlate it with the initial compromise.
- CloudTrail Log Analysis may have caught anomalous API calls but lacked context to link them back to the container.
- Identity Security could have flagged the role self-attachment but wouldn’t trace it to the originating pod
Each tool offers a partial view, leaving analysts to piece together a sprawling attack from disjointed events. They'd be chasing isolated alerts, unaware those alerts were fragments of a single campaign. The result — delayed detection, incomplete understanding, and lost time when it matters most.
Detection and Investigation with Cortex Cloud
Now let's see how the attack unfolds for security engineers using Cortex Cloud.
The security team receives a high-severity alert. The incident appears in the Cortex Cloud console as a single aggregated case, already mapped to related issues across the environment.
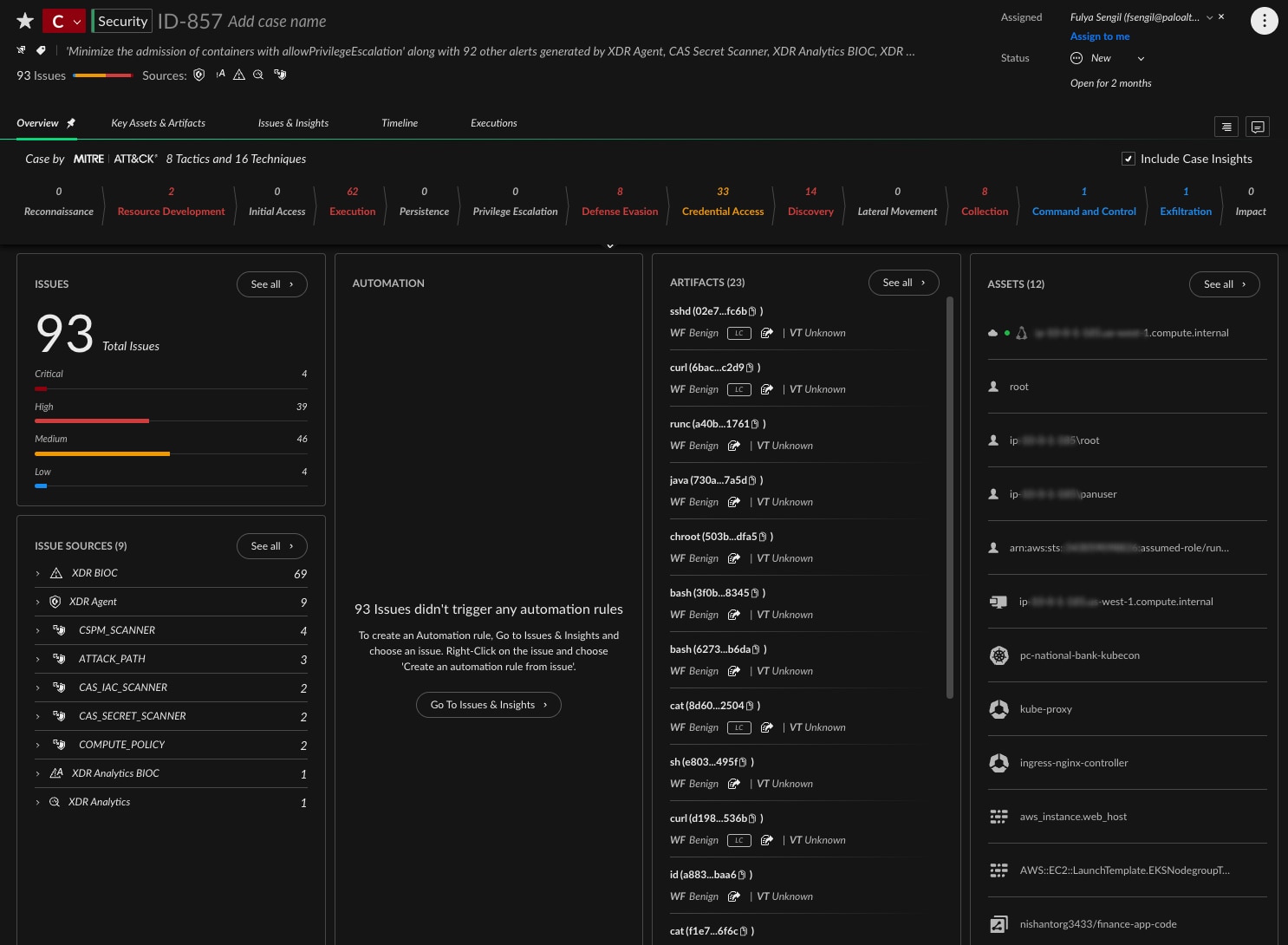
Inside the case screen, the “Issues & Insights” tab presents a unified timeline. The “Issue Sources” panel lists all contributing signals, automatically correlated. The incident includes both runtime activity and posture misconfigurations — conditions that created openings for the attacker at each stage.
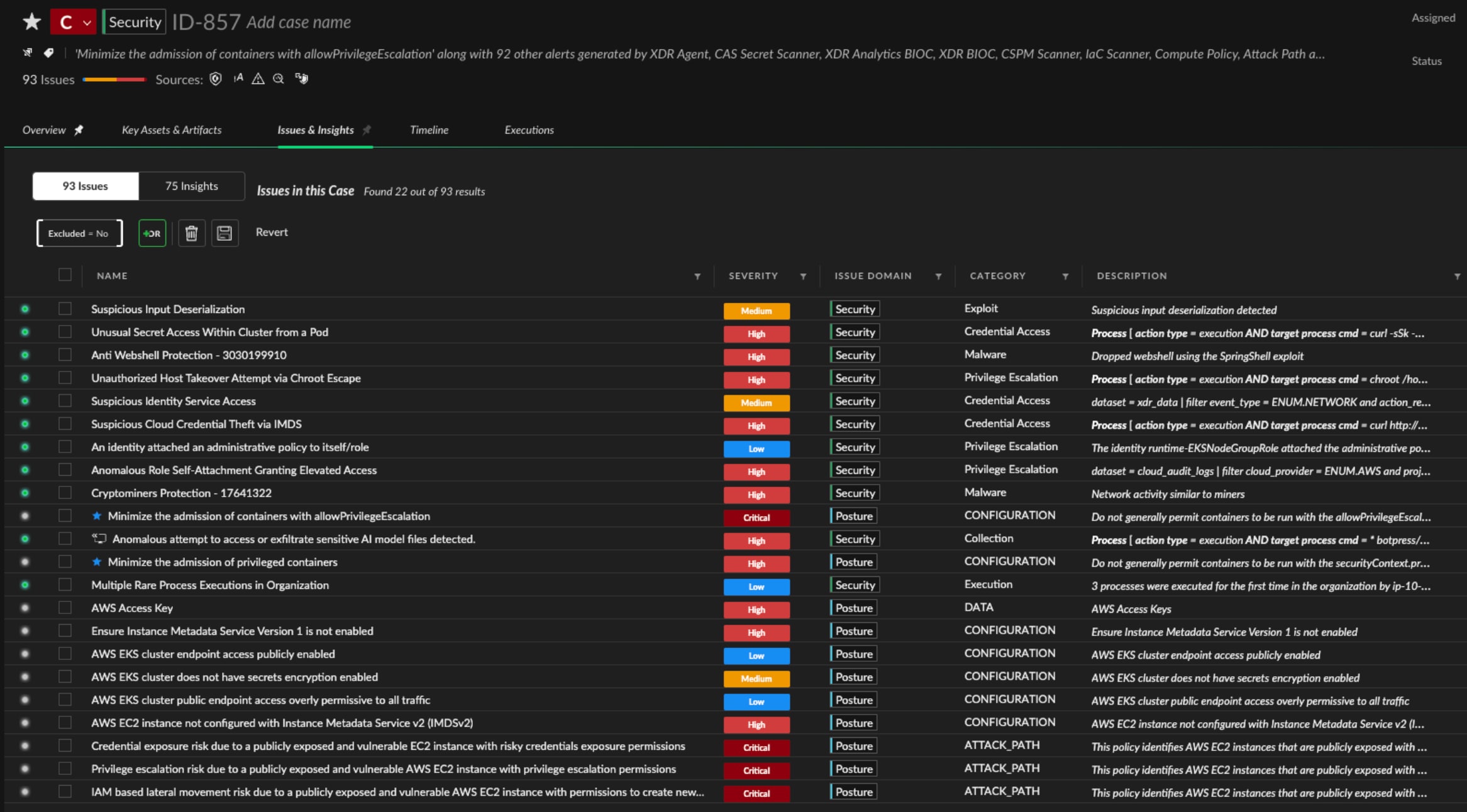
Within seconds, the team reviews key issues flagged by Cortex Cloud:
- Application Layer: “Suspicious Input Deserialization” and “Anti Web Shell Protection” detections
- Secret Access: “Unusual Secret Access Within Cluster from a Pod”
- Container Escape: “Unauthorized Host Takeover Attempt via Chroot Escape”
- Credential Theft: “Suspicious Cloud Credential Theft via IMDS”
- Privilege Escalation: “Anomalous Role Self-Attachment” in AWS
Cortex Cloud correlates these signals into one coherent narrative. Analysts don’t waste time jumping between tools or investigating them in isolation.
From Alerts to Attack Narrative
The team opens the case to investigate further.
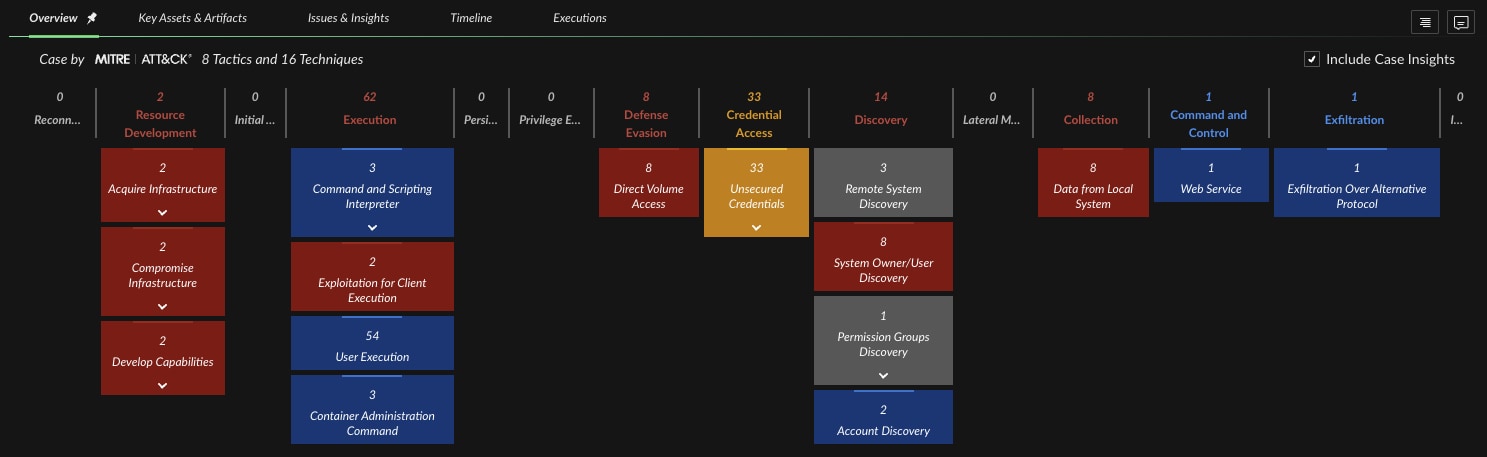
MITRE ATT&CK Mapping
Each detection is mapped to the MITRE ATT&CK framework, showing how the attacker moved through tactics and techniques.
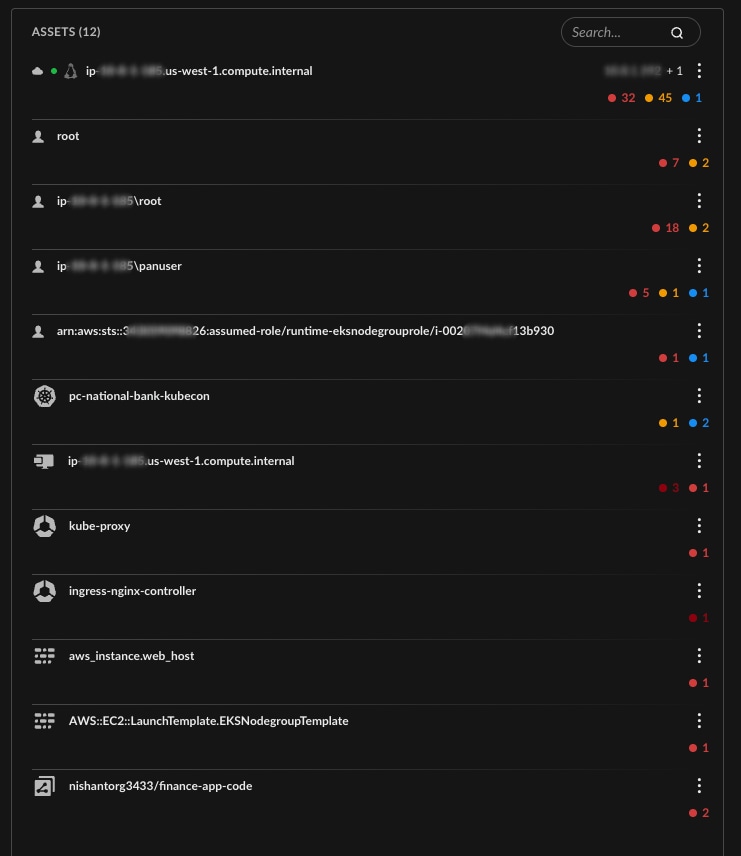
Asset Correlation
Affected resources — containers, clusters, cloud accounts and IAM identities — are connected in a single view. Analysts also see the historical posture issues that made each asset vulnerable.
Causality Chain
An interactive chain reveals the complete attack sequence. The team clicks on the alert for secret access within the cluster.
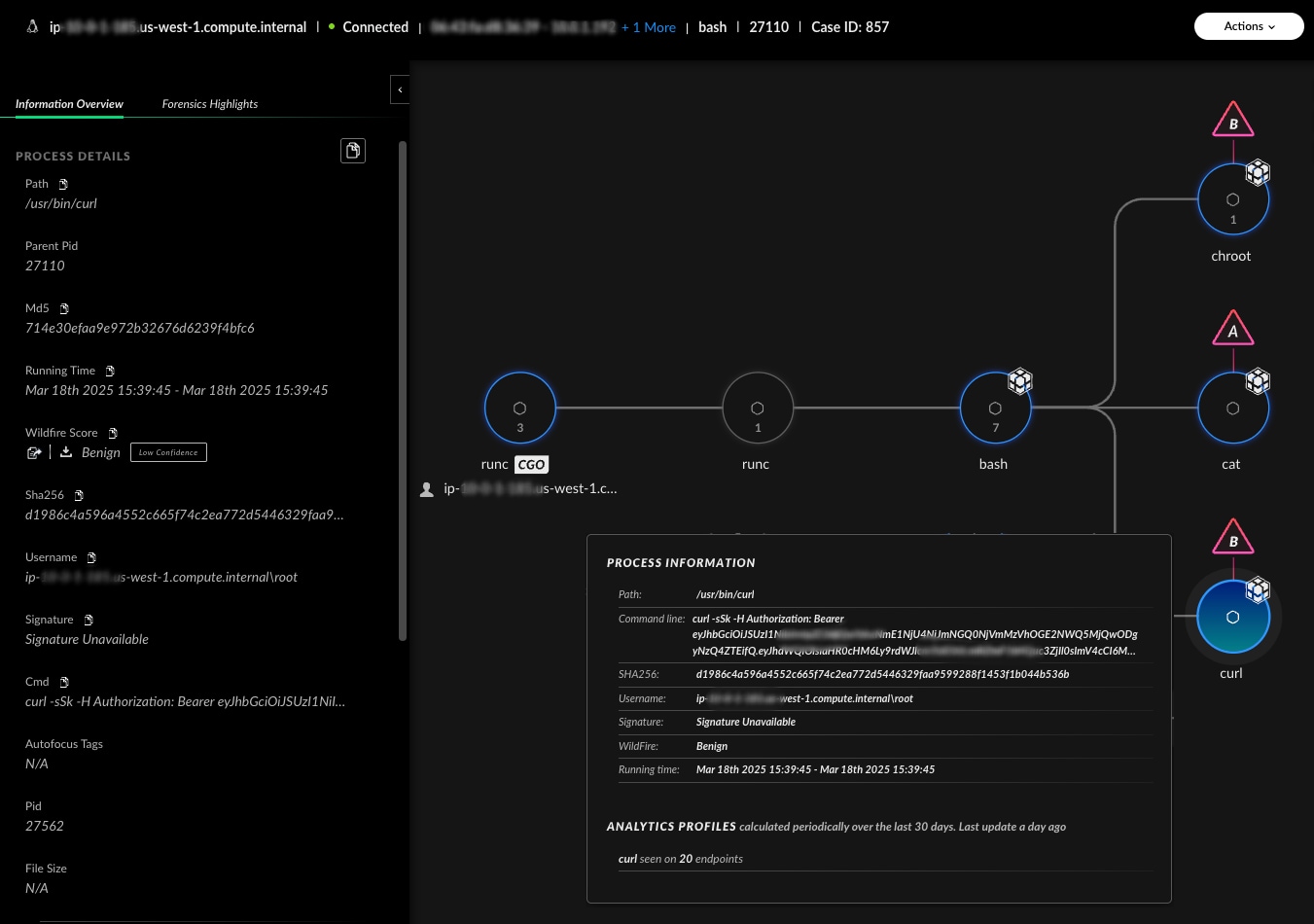
They examine:
- The curl commands used to extract secrets
- The process tree showing which container was compromised
- Network connections initiated during lateral movement
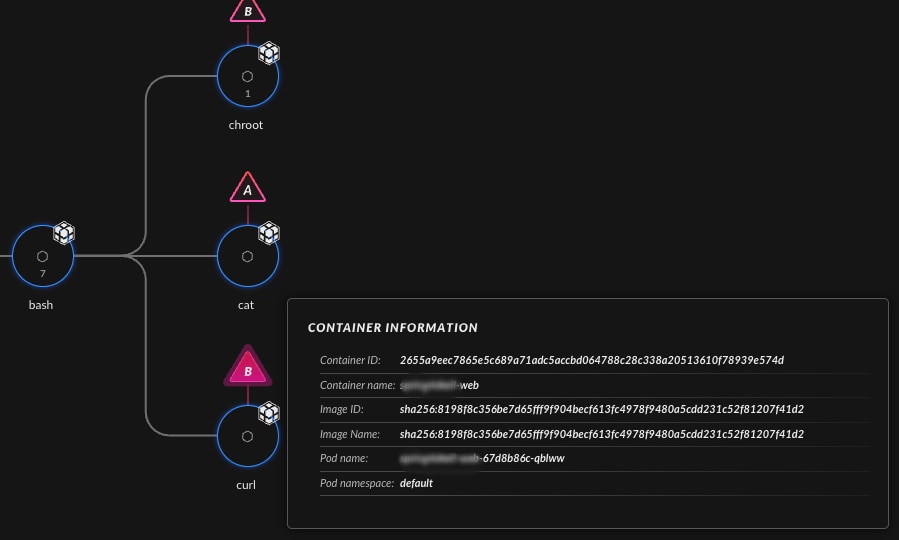
- Links between the pod and other Kubernetes resources
The causality chain continues into the cloud layer. Cortex Cloud surfaces CloudTrail logs showing the exact moment the attacker exploited IMDS and escalated privileges.
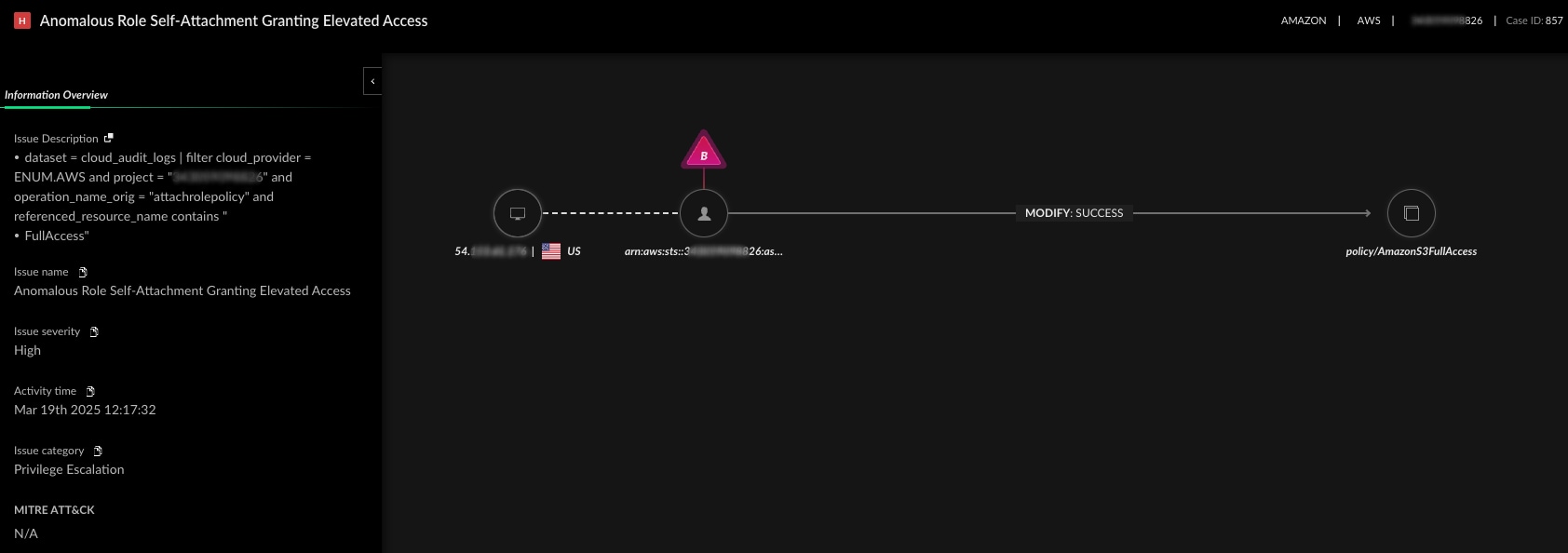
Analysts don’t dig through thousands of logs or guess at intent. They see what happened, where it started, how it spread, and where it could go next.
Immediate Response
With full context in hand, the team acts quickly:
- Container Isolation: Cuts off the compromised pod to stop lateral movement
- Credential Rotation: Replaces all AWS credentials exposed during the breach
- Network Segmentation: Applies tighter policies to restrict pod communication
Containment is swift. The team moves immediately to prevent recurrence by addressing the root causes across posture, identity and workload exposure.
Implementing Preventive Controls
With the attack contained, the team turns to posture management to uncover the underlying weaknesses that enabled the breach.
Kubernetes Security Posture Management (KSPM)
The KSPM dashboard surfaces several configuration issues across the affected clusters.
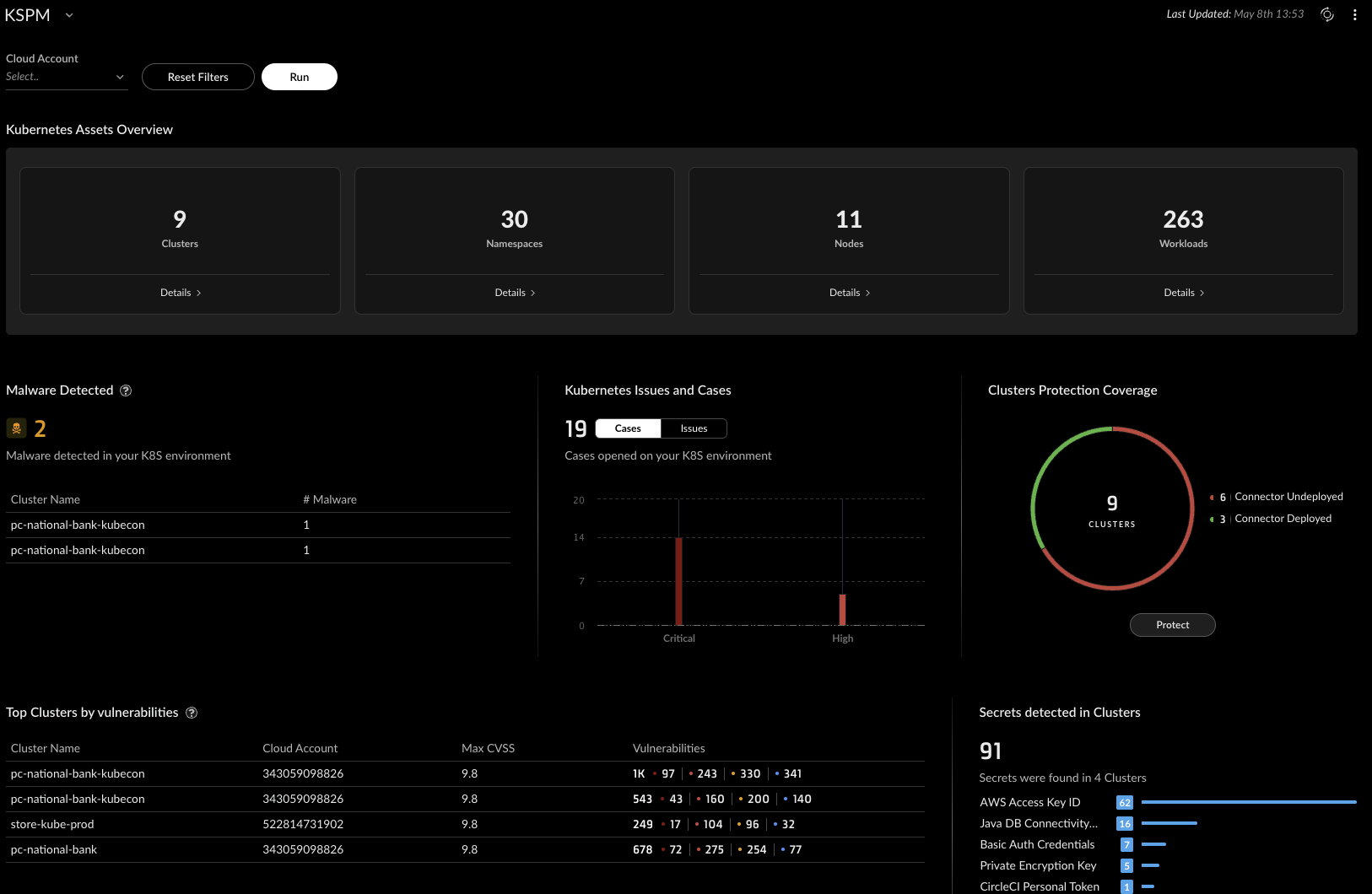
- Pod Security Issues: Pods configured with elevated privileges or missing security context constraints
- Admission Control Gaps: No controllers enforcing security policy at deployment
- Compliance Violations: Multiple infractions against the CIS Amazon EKS Benchmark
The team takes immediate action:
- Enables Cortex Cloud's admission controller across all clusters
- Applies Pod Security Standards to restrict privileges
- Adds network policies to limit both internal and external pod communication
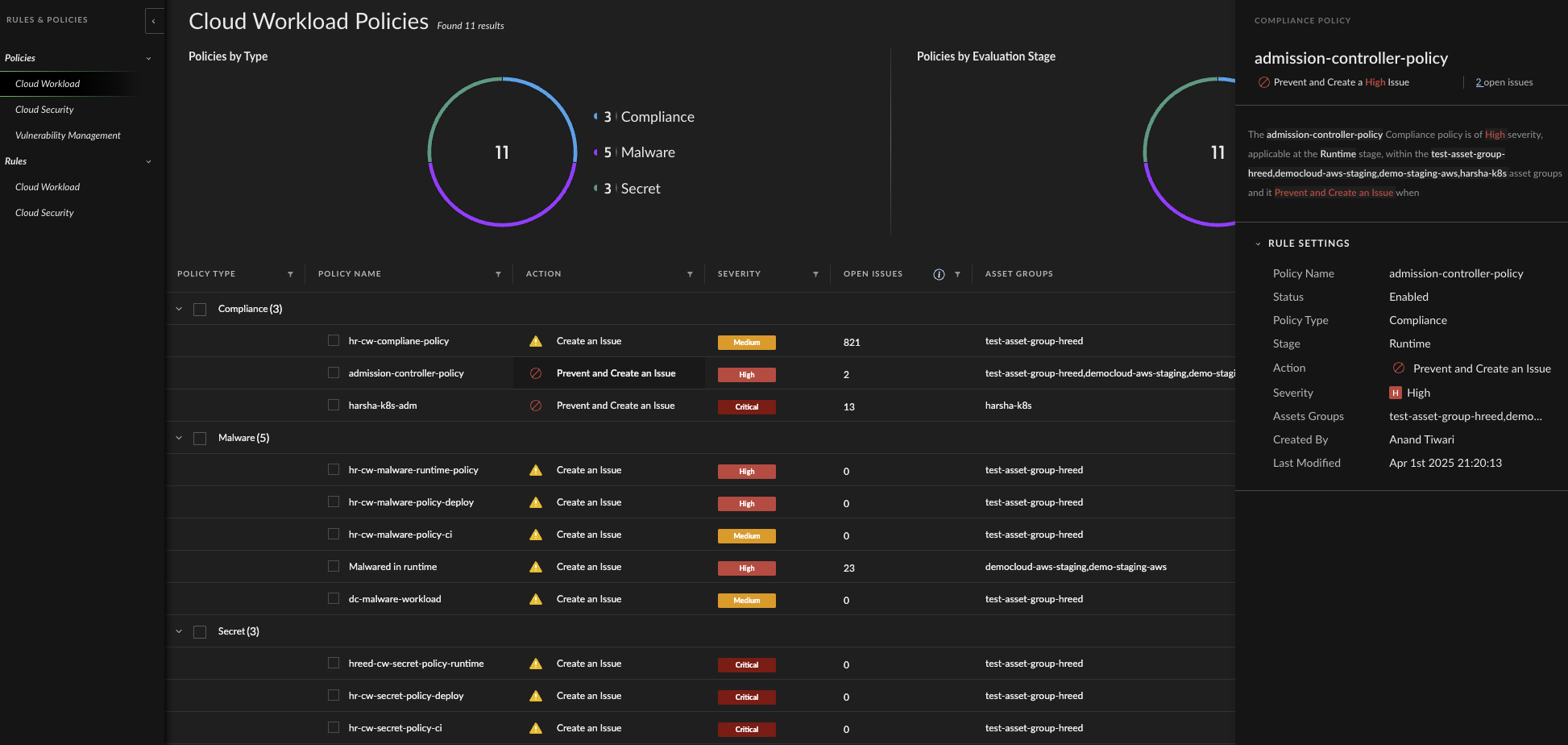
Cloud Configuration Hardening
To address misconfigurations at the cloud layer, the team strengthens identity and instance settings.
- IMDSv2 Enforcement: Replaces all IMDSv1 endpoints with IMDSv2
- IAM Role Hardening: Blocks role self-attachment with updated permissions
- Patch Management: Establishes a workflow for continuous patching of cloud workloads
Shifting Security Left with Application-Aware Controls
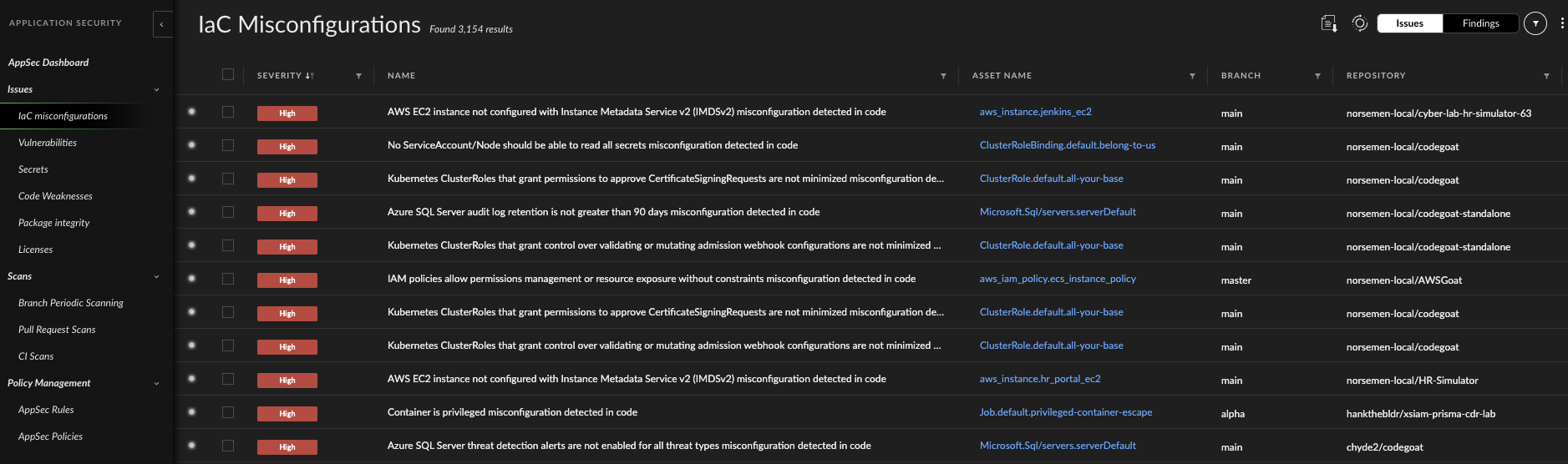
Cortex Cloud’s AppSec capabilities help prevent insecure code and misconfigurations from reaching production.
Code-Level Security
The team integrates scanning into development workflows:
- Software Composition Analysis (SCA): Detects vulnerable packages in application dependencies
- Infrastructure as Code (IaC) Scanning: Flags misconfigurations in manifests and Terraform files
- Secrets Scanning: Identifies embedded credentials in source code repositories
CI/CD Pipeline Security
Security becomes part of the delivery process:
- Admission Control Integration: Blocks unsafe deployments at build time
- Automated Pull Requests: Submits remediations directly into developer workflows
- Policy Guardrails: Enforces configuration baselines without disrupting development
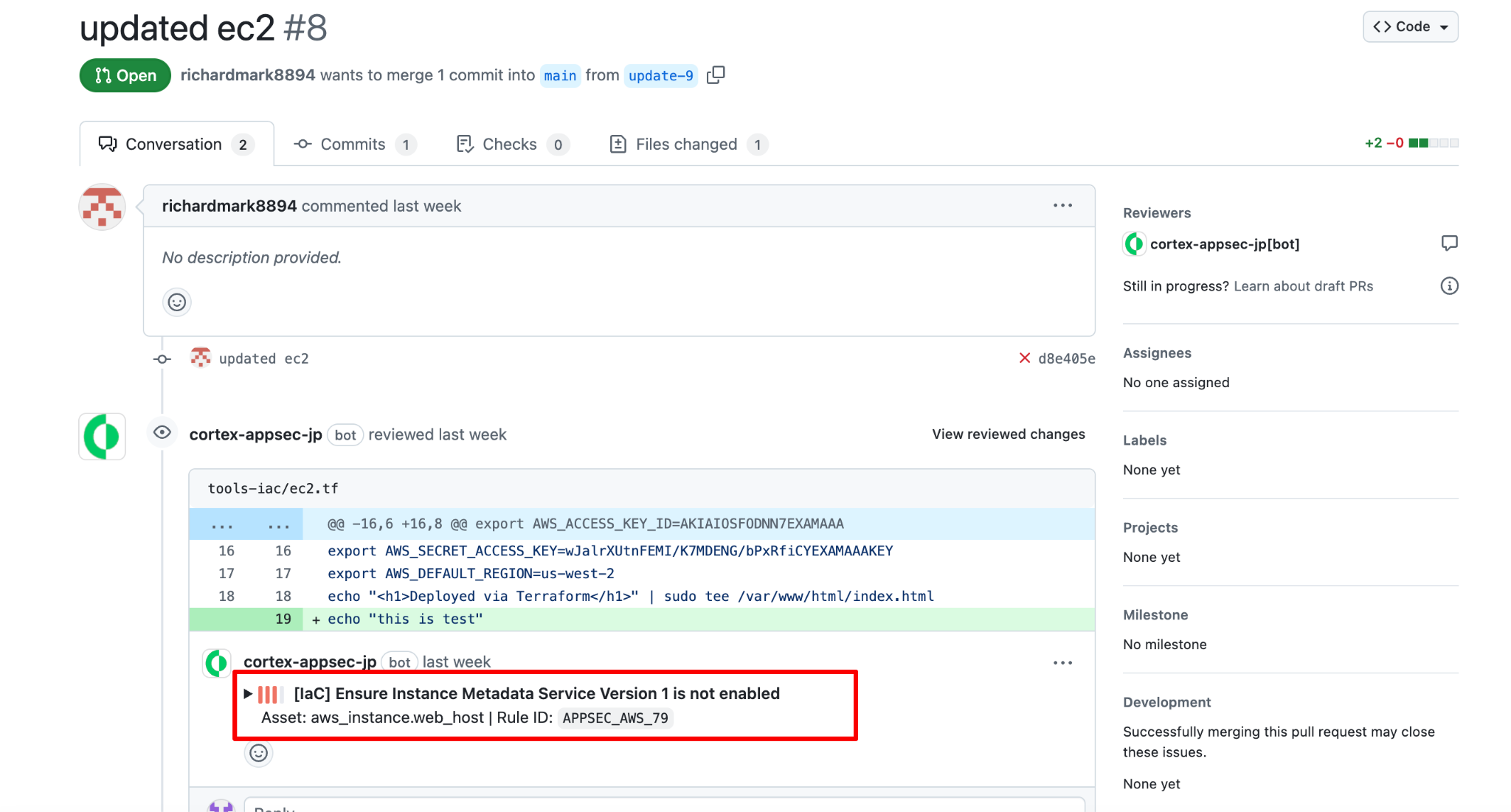
Intelligent Risk Prioritization
With findings across multiple environments, the team needs to focus on what matters most.
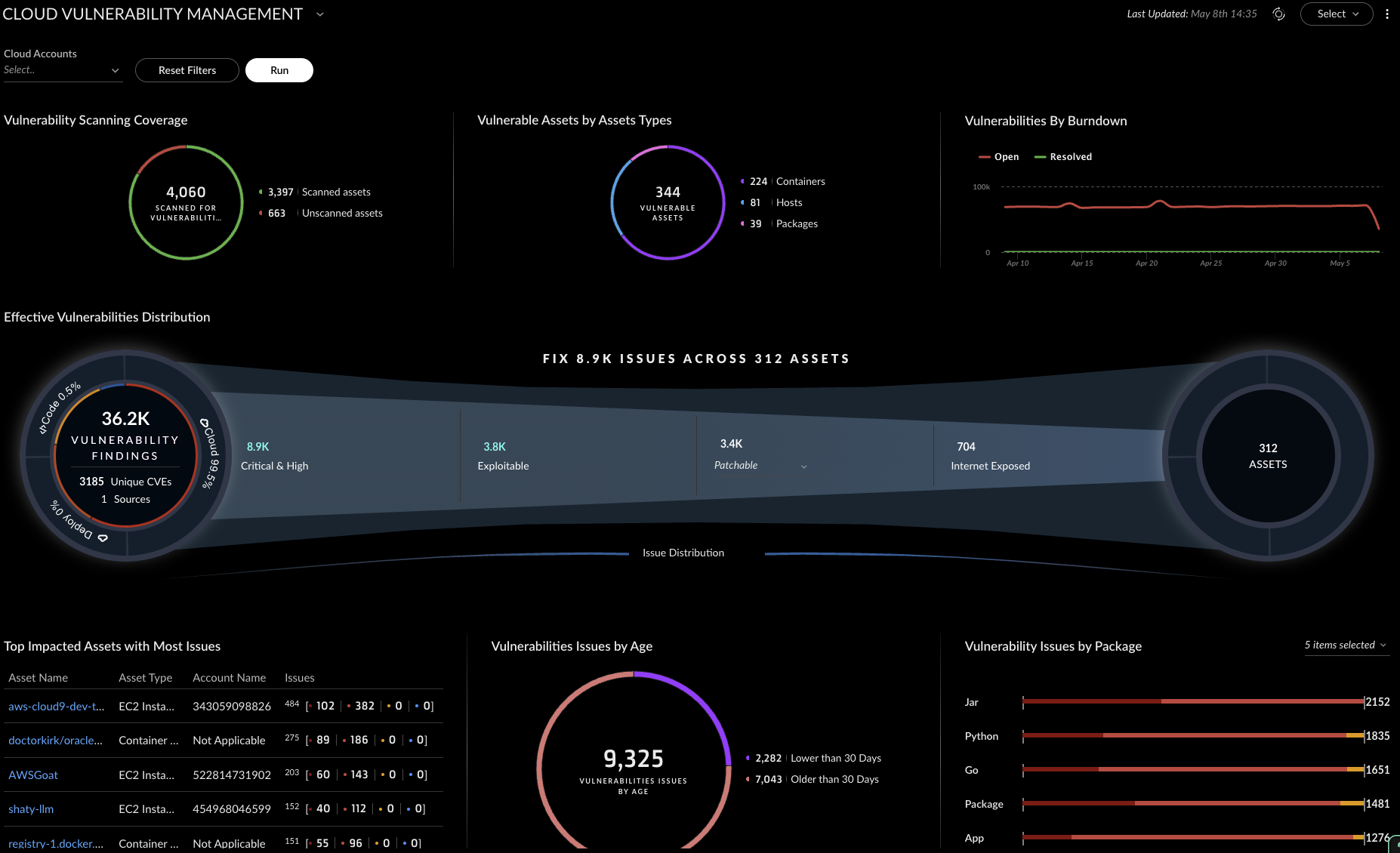
- Runtime Context: Prioritizes vulnerabilities in loaded components
- Exposure Context: Surfaces risks in public-facing workloads first
- Sensitive Data Context: Elevates issues in applications tied to financial systems
Context-aware prioritization reduces noise and focuses response efforts on active, high-impact risks.
Setting Guardrails Without Slowing Development
To support speed and safety, the team configures Cortex Cloud’s intelligent guardrails that:
- Allow unrestricted dependencies in test environments
- Enforce stricter controls in production
- Guide developers through remediation with clear, contextual recommendations
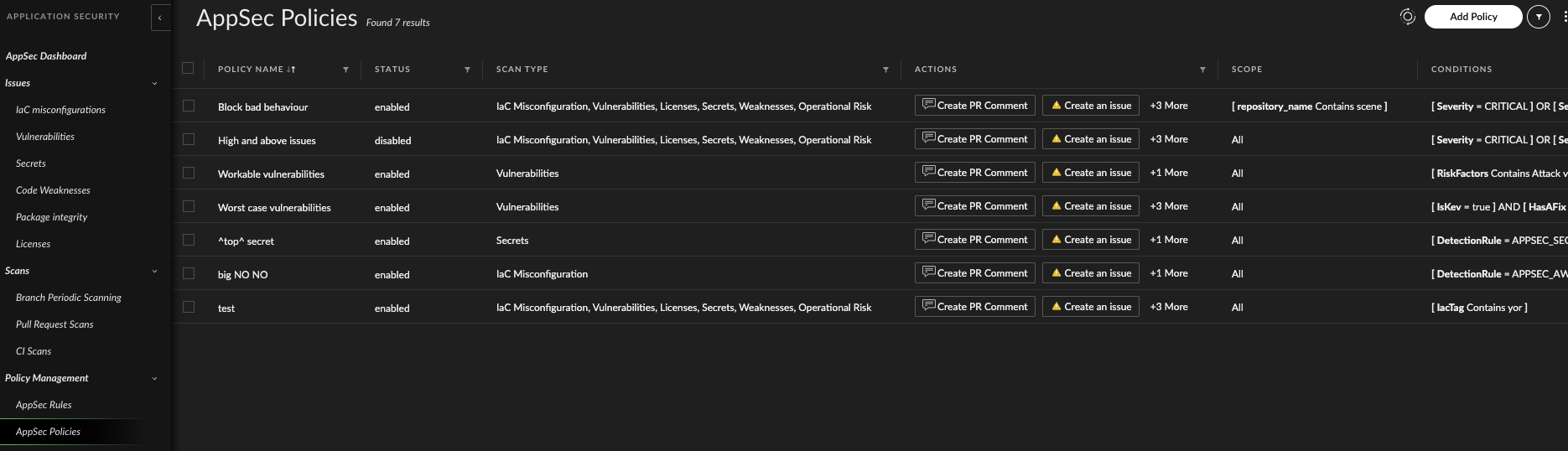
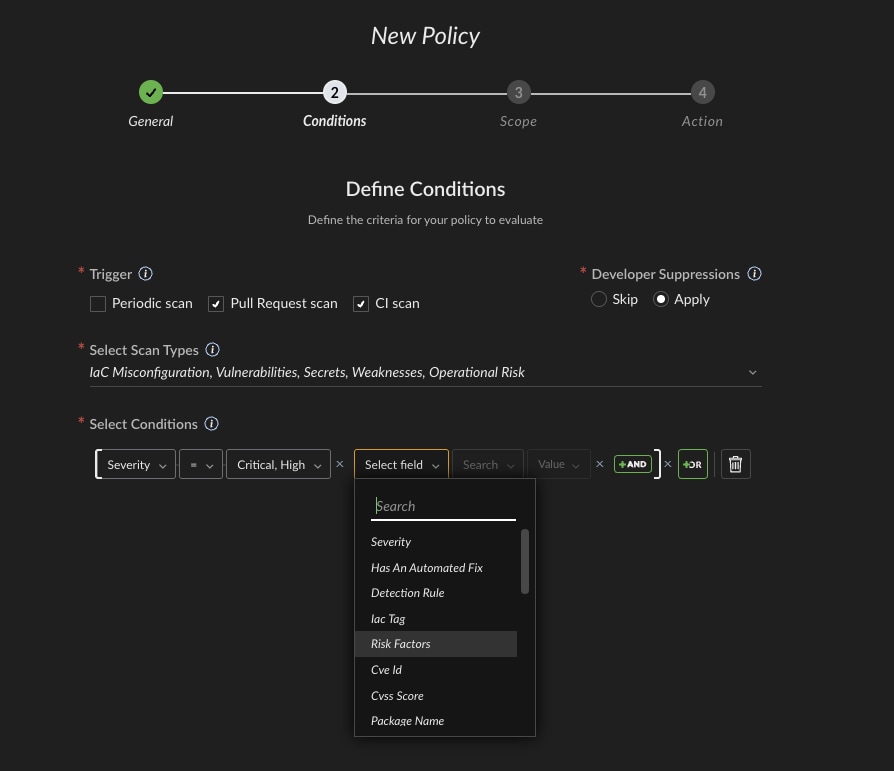
Guardrails maintain momentum without sacrificing security posture.
Results and Business Impact
Cortex Cloud enables lasting gains for the team and the organization:
- Reduced Attack Surface: Fewer misconfigurations across workloads and environments
- Faster Detection: MTTD drops from days to minutes
- Improved Developer Feedback: Security shifts earlier in the pipeline
- Automated Compliance: Continuous alignment with CIS EKS and internal policies
Learn More
Cortex Cloud delivers integrated protection across application security, cloud posture, runtime environments and SOC workflows — enabling teams to secure cloud-native applications with speed and precision.
If you haven’t seen Cortex Cloud up close and in action, schedule your demo today.