Diagnosing the Ransomware Deployment Protocol (RDP)
This post is also available in: 日本語 (Japanese)
Diagnosing the Ransomware Deployment Protocol (RDP)
Remote Desktop Protocol (RDP) is the most popular initial ransomware attack vector and has been for years. For the 2020 Unit 42 Incident Response and Data Breach Report, Unit 42 studied data from over 1,000 incidents and found in 50% of ransomware deployment cases, RDP was the initial attack vector. In the 2021 Cortex Xpanse Attack Surface Threat Report, Cortex Xpanse researchers found that RDP accounted for 30% of total exposures, which more than doubles the next most common exposure.
RDP is a protocol on Microsoft Windows systems that is designed to allow users to remotely connect to and control a remote system. The most common legitimate use is to allow IT support to remotely control a user's system to fix an issue. More recently, RDP has become popular for cloud computing to access virtual machines (VMs) in cloud environments or to remotely manage cloud assets.
It is extremely easy to expose RDP unintentionally by leaving RDP exposed on a forgotten system, cloud instance, device previously protected by network segmentation or by directly connecting to the internet. What’s worse is that RDP has become more widespread, more exposed and a more prevalent risk that can lead to attacks – specifically ransomware deployment – loss of data, expensive downtime and remediation efforts, as well as brand damage for organizations.
More Exposures Mean More Targets
The COVID-19 pandemic first led to a surge in working from home, meaning laptops moved from the safe space of an office network with a firewall, to home networks where security was never considered.
IT wasn’t ready for this shift, so new laptops had to be purchased and sent out very quickly to remote workers. This speed meant mistakes and more RDP exposures. The shift to remote work also exacerbated the risks associated with ephemeral dynamic DNS.
Computers on office networks with assigned IP addresses are easy to inventory and track. In individual homes, computers have IP addresses that can change day-to-day as internet service providers (ISPs) dynamically assign addresses. And, those remote assets can move from home to a coffee shop or friend’s house and back, each time getting a new IP address. This has long been a risk, but right now there are more remote workers than ever before.
The Unit 42 Cloud Threat Report, 1H 2021 found that from Q1 2020 (pre-COVID-19) to Q2 2020 (post-COVID-19) RDP exposures increased by 59% across all cloud providers. It is easier than ever to spin up new cloud instances, and the likelihood of mistakes being made only rises.
So, RDP is everywhere; RDP is a major target for threat actors; and, RDP is often the initial attack vector in ransomware attacks. Unfortunately, there’s a bit more bad news. According to the Cortex Xpanse report, RDP accounted for 32% of overall security issues found in scans of 50 million IP addresses associated with 50 global enterprises in the first three months of 2021.
Why RDP is Dangerous
RDP is a favorite target of threat actors because once an attacker is in, they have full access (up to the level of the compromised user account) to the system. If an admin account is attacked, that's a disaster. But, even if a more restricted user account is compromised, the attacker just needs to find another vulnerability on that system to elevate privileges and gain more access.
For malicious actors, finding exposed RDP requires a simple nmap script that scans the internet for an open port 3389 — the default RDP port. Today, attackers are constantly scanning for port 3389, as shown in Figure X.
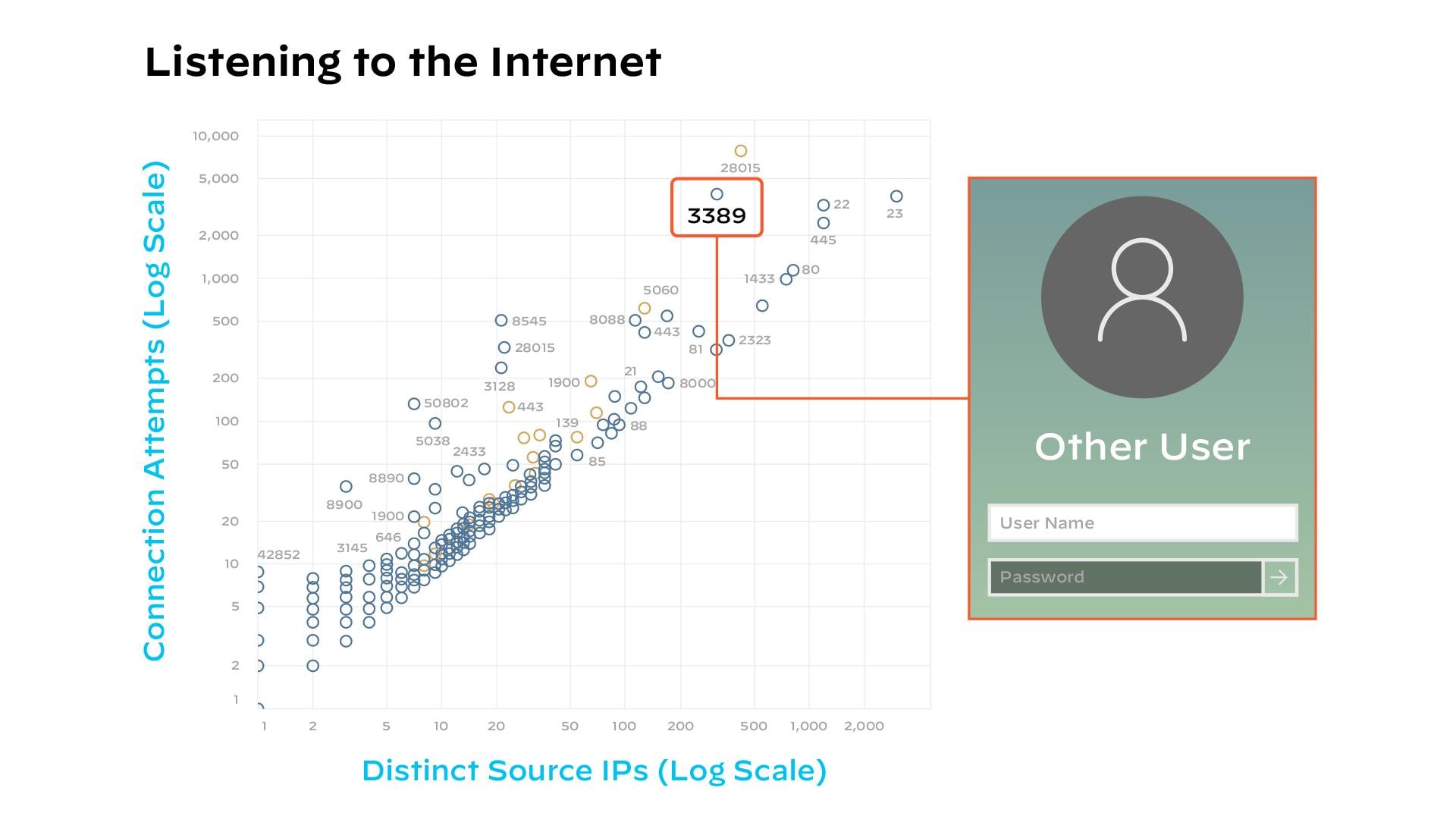
According to Cortex Xpanse research, attackers can scan the entire internet in just 45 minutes. So if RDP is exposed, it will be found, and there are multiple ways an attacker can get in:
- Use stolen credentials to login.
- Brute force the login (if the implementation allows unlimited login attempts).
- Perform a man-in-the-middle attack, if it’s an outdated version of RDP or using flawed encryption.
- Exploit known vulnerabilities in older versions of RDP, such as BlueKeep.
Avoiding the Ransomware Lottery
Malicious actors aren’t always looking for specific targets. More often than not, they’re just looking for vulnerabilities and hoping an attack will result in a payout. Ransomware is an evil lottery system and you play just by leaving the door open with exposures, like RDP.
Step one for any organization is to limit RDP risk by scanning for vulnerabilities faster than your adversaries can, and be sure to have full visibility and a full system of records for all of your internet-connected devices. This record needs to be constantly updated because new assets may pop up and known assets could have settings changed in risky ways. Vulnerability scanners can’t find these exposures if they exist in outside IP space, so you need to be scanning from the outside-in. Leading companies use mean time to inventory (MTTI) to measure how quickly they can scan for full inventory and assess potential exposures.
The number one way to ensure you don’t have unnecessary RDP exposures is to simply disable RDP on all systems where it isn’t necessary. For systems where RDP is needed, follow security measures:
- Place RDP behind a virtual private network (VPN).
- Enable multi-factor authentication (MFA). The best way to mitigate risk related to stolen credentials is to ensure MFA is enabled on all user accounts.
- Limit login attempts. Similarly, to mitigate risk of brute force attacks, limit failed login attempts rather than allowing unlimited attempts.
- Set time limits on disconnected sessions and automatically ending sessions that hit that limit.
- Consider an allow-list, so that only approved IP addresses can connect to RDP servers.
- Deploy an internet-scale Attack Surface Monitoring solution, such as Cortex Xpanse, to monitor for unintended exposures of RDP or other remote access services.
Make RDP a Priority
By now, it should be clear why RDP = Ransomware Deployment Protocol. RDP configuration should be a high priority item in all IT hygiene plans. It is a protocol that has dangerous default settings, and it is far too easy for a user to enable or use in risky ways.
If not properly configured, RDP will be used as an attack vector if/when your organization is targeted by ransomware operators. This is not a theoretical risk. It is a simple fact of IT. Unsecured RDP will be used against you at some point.
Whether or not you intend to expose RDP publicly, these exposures happen internet-wide and not just on your known IP space. This means defenders must monitor at internet-scale for any unintended or misconfigured implementations, because you can be sure the attackers are monitoring, too.
To learn more about risks to your attack surface, download the 2021 Cortex Xpanse Attack Surface Threat Report.
Related Blogs
Subscribe to the Newsletter!
By submitting this form, you agree to our Terms of Use and acknowledge our Privacy Statement. Please look for a confirmation email from us. If you don't receive it in the next 10 minutes, please check your spam folder.