Search
2022 incident response attack trends, most common incident types, how attackers gain
initial access, what vulnerabilities they exploit and which industries they target
01
RANSOMWARE
Attackers are asking for and getting higher ransom payouts
As of June, the average ransomware payment in cases worked by Unit 42 incident responders in 2022 was US$925,162 – a 71% increase compared to 2021.
$30MUSD
Biggest Ask
$8.5MUSD
Biggest Payout
Case Study:
BlackCat Ransomware
Watch now

















Attackers use multiextortion techniques to maximize profit.
Ransomware actors typically encrypt an organization’s files – but increasingly, they also name and
shame their victims, increasing the pressure to pay. Many ransomware groups maintain dark web leak
sites for the purpose of double extortion.
Threat actors have increasingly favored extortion – whether in combination with other techniques or
on its own.
4%
of Unit 42 cases involved extortion without encryption, and we expect this percentage to rise.
RaaS is helping drive an increase in unskilled threat actors.
Ransomware as a service (RaaS) is a business for criminals, by criminals. They normally set the
terms for ransomware, often in exchange for monthly fees or a percentage of ransoms paid. RaaS makes
carrying out attacks that much easier, lowering the barrier to entry and accelerating the growth of
ransomware.
02
CLOUD INCIDENTS
Misconfiguration is the primary cause in
cloud breaches
Nearly 65% of known cloud security incidents were due to misconfigurations. The main
culprit? IAM configuration.
We analyzed more than 680,000 identities across 18,000 cloud accounts from 200 different
organizations. What we found is that nearly all lacked the proper IAM policy controls to
remain secure.
03
BEC
Business email compromise is more than a nuisance.
The U.S. Federal Bureau of Investigation calls BEC the “$43 billion
scam.” This refers to the incidents reported to the Internet Crime Complaint Center from
2016–2021.
Unit 42’s telemetry on BEC attack campaigns has resulted in BEC actors
arrested in Operation Falcon II and Operation Delilah.
insights on
How Attackers Get In
The top three initial access vectors for adversaries were phishing, known software
vulnerabilities and brute force credential attacks (primarily on remote desktop protocol).
77%
of suspected root causes for intrusions came from phishing, vulnerablity exploit, and brute
force attacks.
04
Vectors
Attackers used phishing 40% of the time to gain initial access
Attackers are looking for easy ways in. Phishing is a low-cost method with high results for
attackers. We've provided “10 Recommendations to Prevent Phishing Attacks” in our report.

05
LOG4SHELL
Log4Shell: A critical vulnerability with continuing impact
A zero-day remote code execution (RCE) vulnerability in
Apache Log4j 2 was
identified as being exploited in the wild on December 9, 2021. Log4Shell was rated a
10 on the
Common Vulnerability Scoring System (CVSS) – the highest possible score.
By February 2, we observed almost 126 million hits
triggering the Threat
Prevention signature meant to protect against attempts to exploit the Log4j
vulnerability. Log4j
accounted for nearly 14% of the cases in which attackers exploited vulnerabilities
to gain access
over the last year – despite only being public for a few months of the time period
we studied.
As recently as June 23, CISA released an advisory warning that malicious actors continue to
exploit Log4Shell in VMware Horizon
Systems.
06
zoho
Zoho Vulnerabilities Used by Sophisticated, Difficult-to-Detect Campaigns
U.S. CISA released an alert on September 16, 2021, warning
that advanced
persistent threat (APT) actors were actively exploiting newly identified
vulnerabilities in the
self-service password management and single sign-on solution Zoho ManageEngine
ADSelfService Plus.
Unit 42 later disclosed a persistent, sophisticated, active and difficult-to-detect
campaign using
the vulnerabilities tracked as TiltedTemple.
The TiltedTemple campaign attacked more than 13 targets across the technology,
defense, healthcare,
energy, finance and education industries, apparently aiming to gather and exfiltrate
sensitive
documents from compromised organizations.
Zoho ManageEngine ADSelfService Plus accounted for about 4% of the vulnerabilities
threat actors
exploited to gain initial access in our incident response cases.
The nature of some of the observed attacks, however, underscores that volume is not
the only
consideration when evaluating risk related to a vulnerability.
07
PROXYSHELL
ProxyShell most common vulnerabilities exploited by attackers in recent Unit 42 cases
ProxyShell is an attack chain that works by exploiting three
vulnerabilities
in Microsoft Exchange: CVE-2021-34473, CVE-2021-34523 and CVE-2021-31207.
The attack chain allows attackers to perform remote code execution, which means they
would be able
to run malicious code on compromised systems without needing physical access to
them.
U.S. CISA issued an urgent
advisory against ProxyShell on August 21,
2021.
Attackers actively exploited ProxyShell almost as soon as it was disclosed – in Unit
42 cases where
attackers gained initial access by exploiting a vulnerability, they used ProxyShell
more than half
the time.
insights on
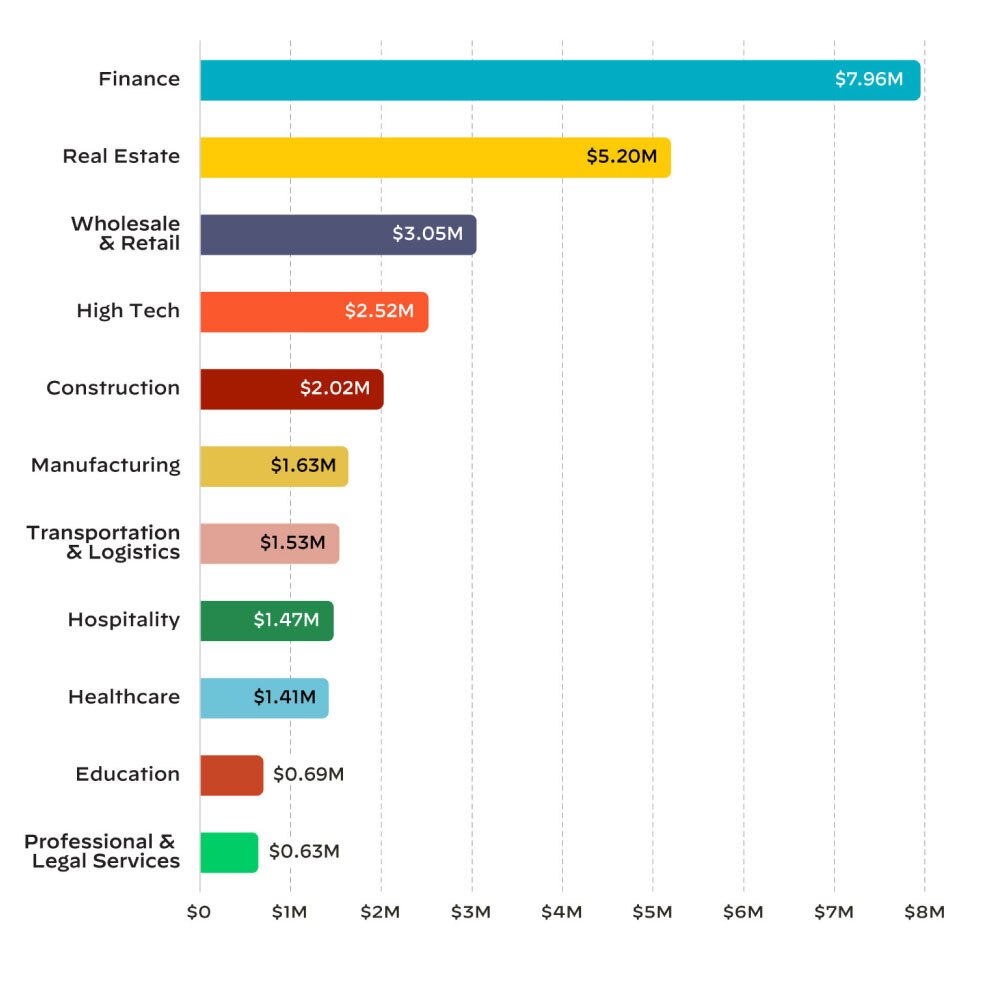
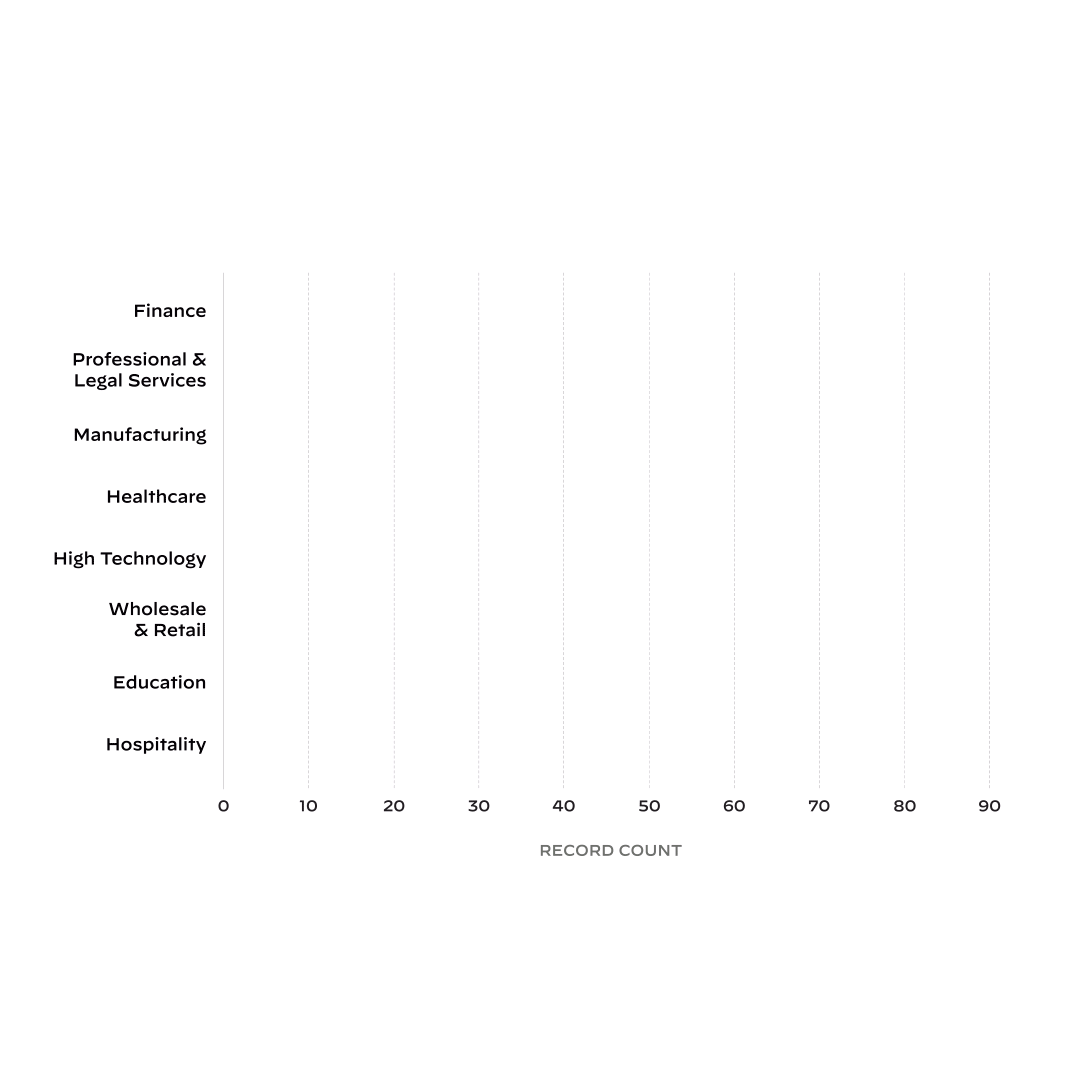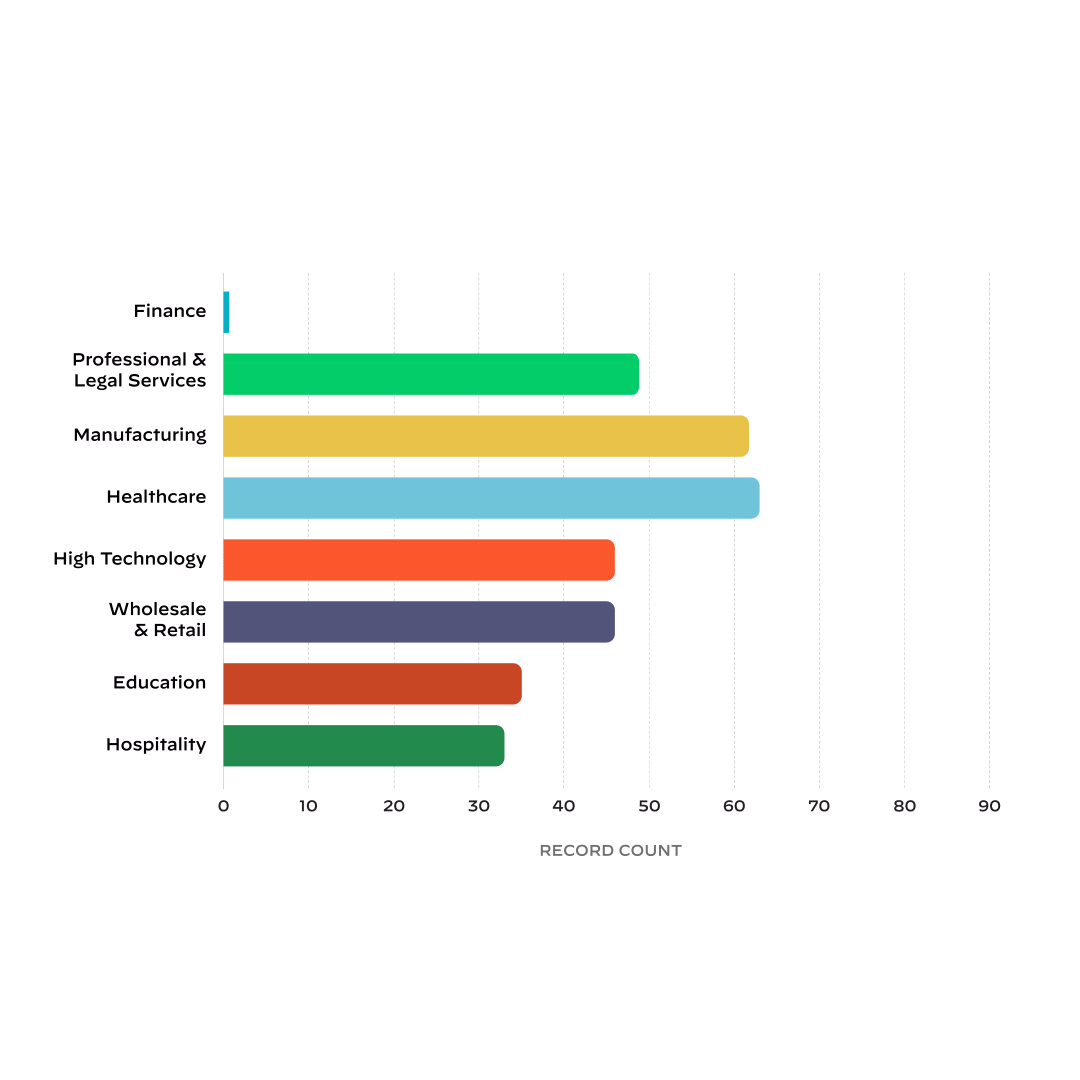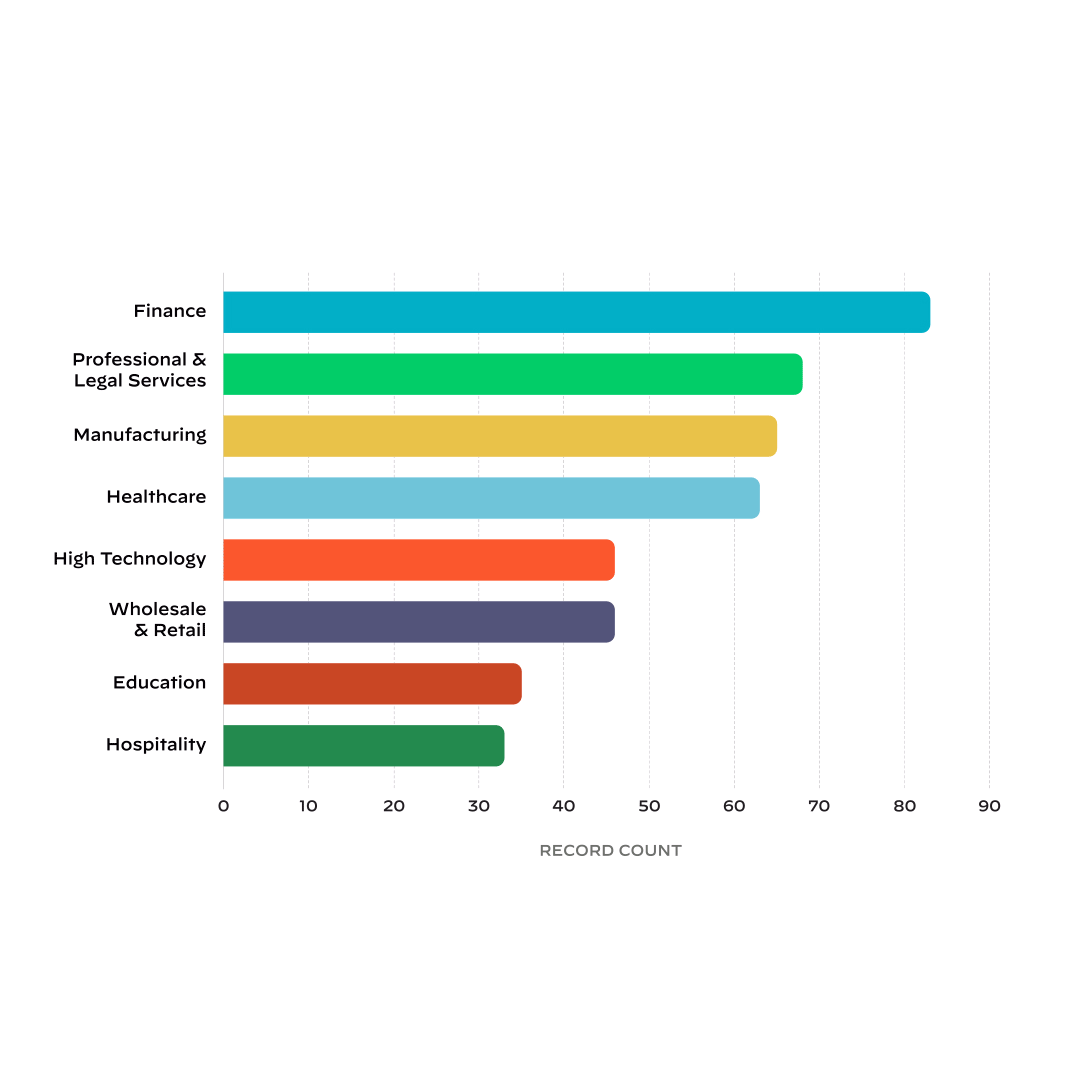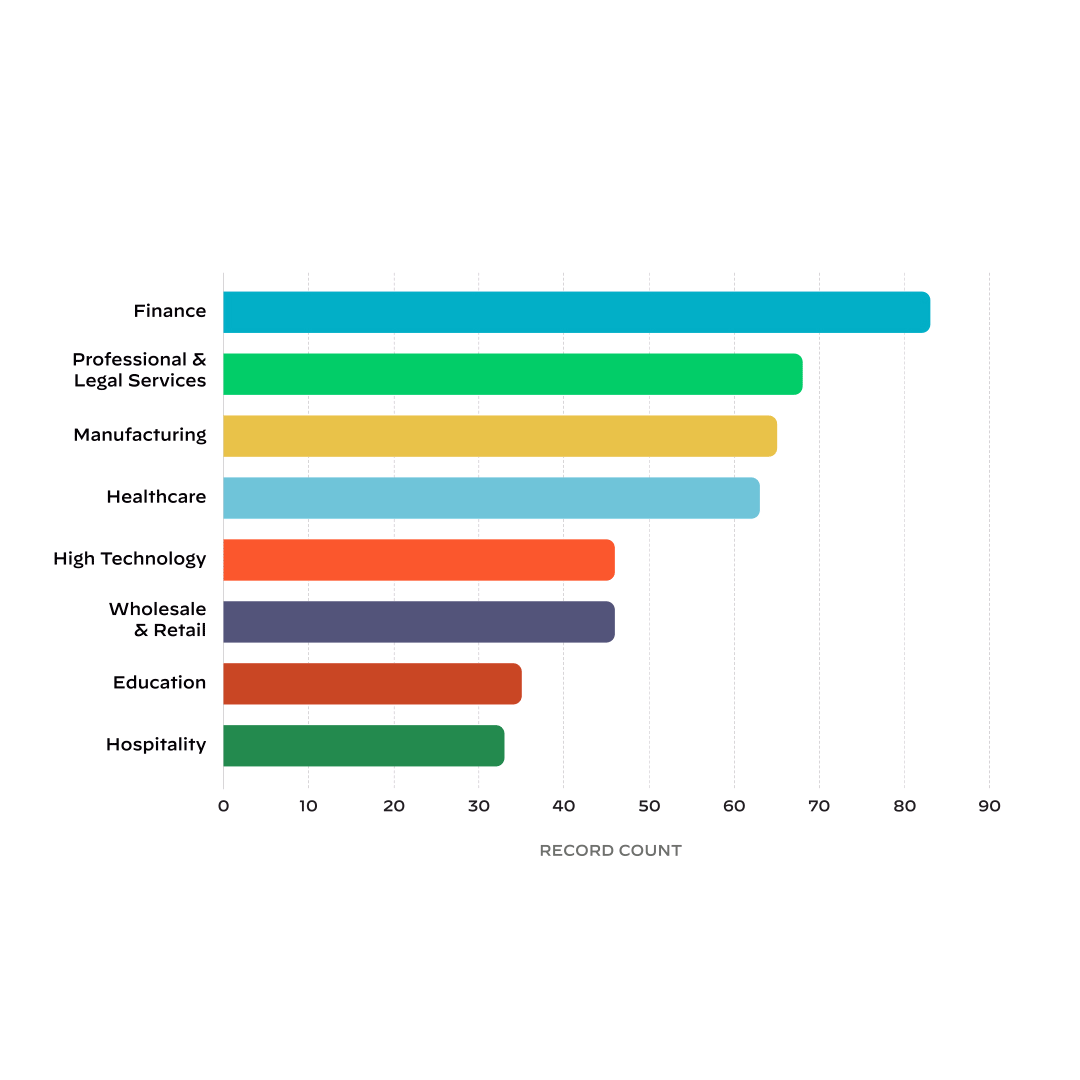
Industries
The top affected industries in our case data were finance, professional and
legal
services, manufacturing, healthcare, high tech, wholesale and retail.
These industries accounted for 63% of our cases.
Organizations within these industries store, transmit and process high
volumes of
monetizable sensitive information, which may attract threat actors.
Attackers are often opportunistic – in some cases, an industry may be particularly affected because,
for example, organizations in that industry make widespread use of certain software with known
vulnerabilities.
08
Top Affected Industries in 2022
Finance
The average ransom demand we observed in the past year for the finance industry was nearly US$8
million. However, the average payment was only about US$154,000 – representing about 2% on average
of the demand in cases where organizations decided to pay the ransom.
Healthcare
The average ransom demand we observed in the past year for the healthcare industry was over
US$1.4 million. And the average payment was US$1.2 million, representing about 90% on average of the
demand in cases where organizations decided to pay the ransom.
09
Top 6 Recommended Best Practices
The cyberthreat landscape can be overwhelming. Every day brings news of more cyberattacks and more
sophisticated attack types. Some organizations may not know where to start, but our security
consultants have some suggestions. Here are six of them:
1
Conduct recurring training for employees and contractors in phishing prevention and security
best practices.
2
Disable any direct external RDP access by always using an enterprise-grade MFA VPN.
3
Patch internet-exposed systems as quickly as possible to prevent vulnerability exploitation.
4
Implement MFA as a security policy for all users.
5
Require all payment verification to take place outside of email, ensuring a multistep
verification process.
6
Consider a credential breach detection service and/or attack surface management solution to help
track vulnerable systems and potential breaches.
Dive Deeper with Unit 42 Experts



Stay ahead of attacks.
Ransomware and business email compromise (BEC) made up the majority of
cases Unit 42 responded to over the past year. Hear expert insights on
preparing for and responding to the evolving threat landscape.



Perfect your pitch.
Our clients ask for help to frame risks and threats with their
leadership, especially the board of directors. Join our executives for a conversation on
how to use the Incident Response Report to strengthen your argument.





















Dive Deeper with Unit 42 Experts
Stay ahead of attacks.
Perfect your pitch.