Prisma Cloud Now Detects Threats Using the TOR Network
Malicious actors, including the notorious Lapsus$ group, tend to take advantage of stolen credentials obtained using various means such as scraping public repos or storage for credentials which are inadvertently exposed to gain access to victims' accounts. One of the effective components that can help your organization defend against these threats is the use of comprehensive User and Entity Behavior Analytics (UEBA).
Prisma Cloud UEBA leverages advanced machine learning (ML) techniques and multiple threat intelligence feeds that help detect anomalous activity in your cloud environments. Previously, we presented one of our UEBA capabilities called compute provisioning anomaly detection to detect the provisioning of virtual machines for cryptomining that has already saved customers thousands of dollars a day. We are excited to introduce our most recent UEBA capabilities for detecting suspicious activity originating from The Onion Routing (TOR) network!
Why Attackers use TOR Anonymity Networks
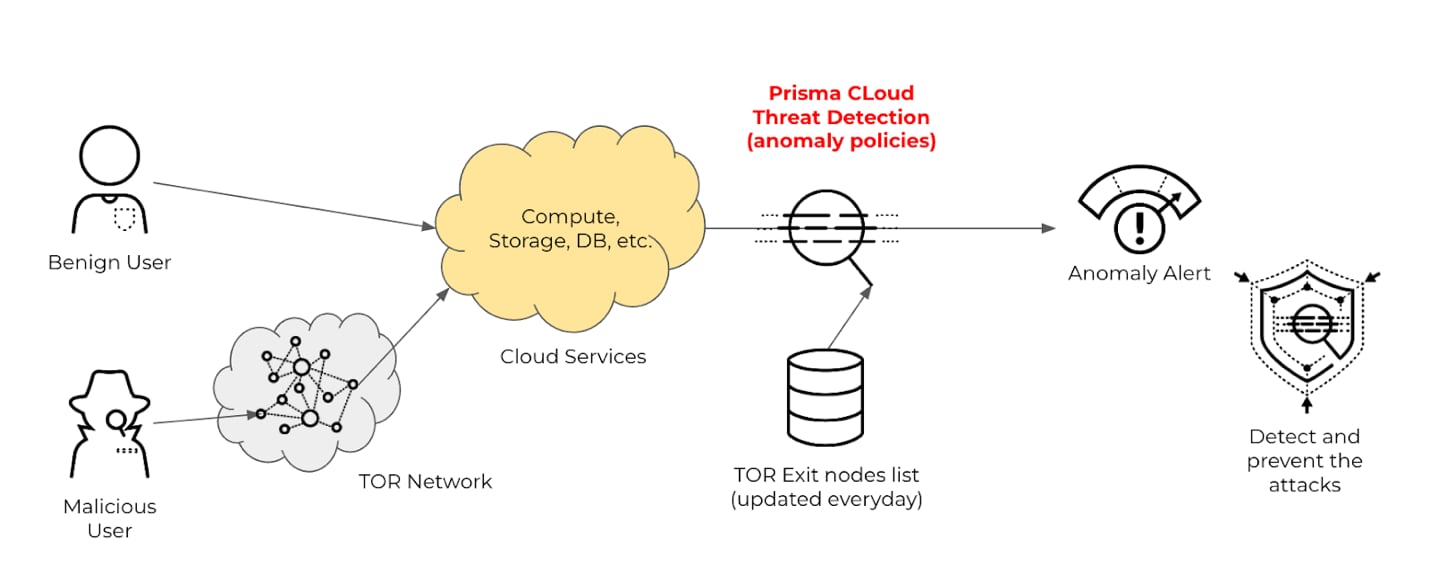
TOR is a tool that offers users the ability to perform their activity anonymously by encrypting and routing requests through multiple relay layers or nodes (like an onion). The online activities using TOR would appear to have originated from one of the TOR exit nodes, instead of the IP address of the user’s device. In general, attackers use TOR networks to perform activities that help in the preparation of attacks such as data exfiltration of personal or financial data and cryptojacking. Hence, early identification of such TOR-based events is critical for preventing these attacks.
Detecting TOR-based Suspicious Activities Using Prisma Cloud
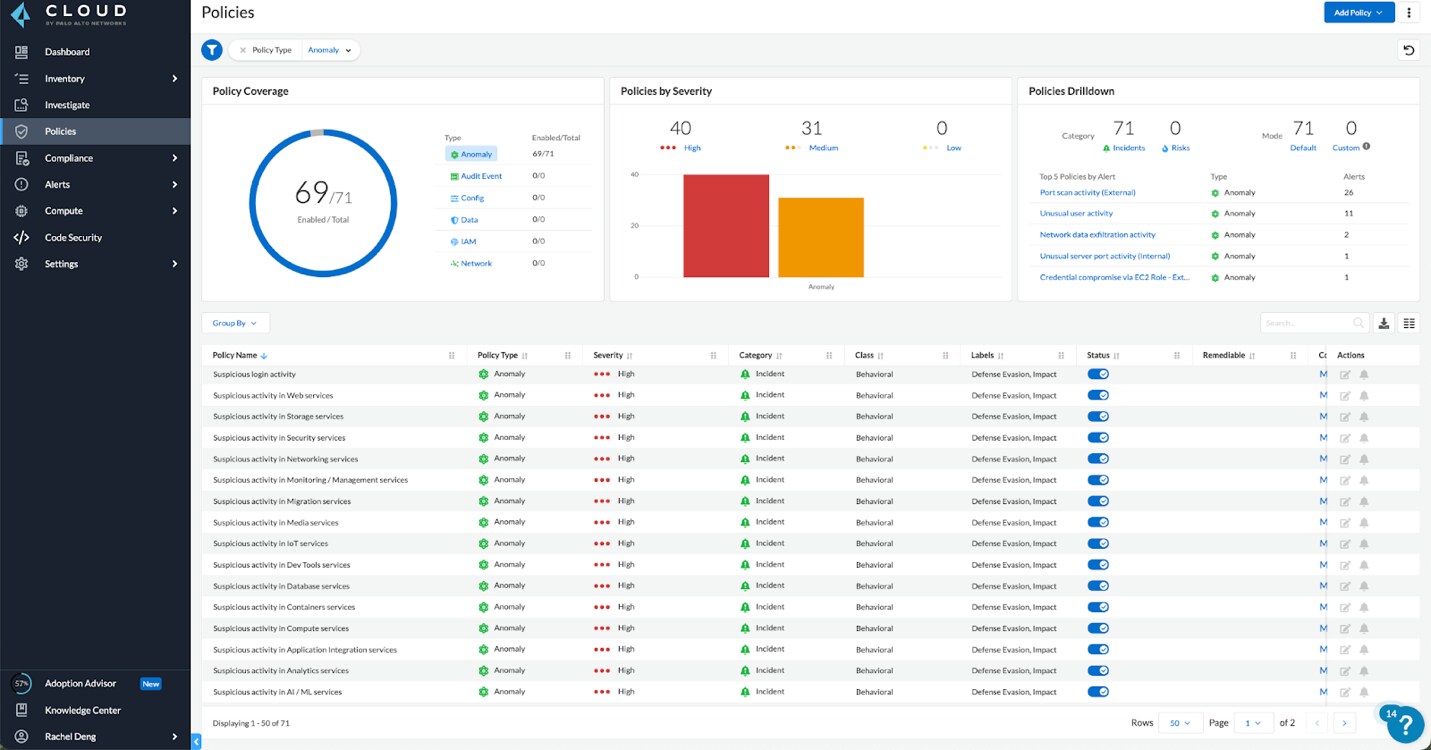
Prisma Cloud continuously scans the event logs from the activity of all the users in the customers' accounts. The source IP from the audit logs is mapped with the recent TOR exit nodes list, which is a threat intelligence source updated every day. If the IP address matches with one of the TOR exit nodes, then an alert is generated.
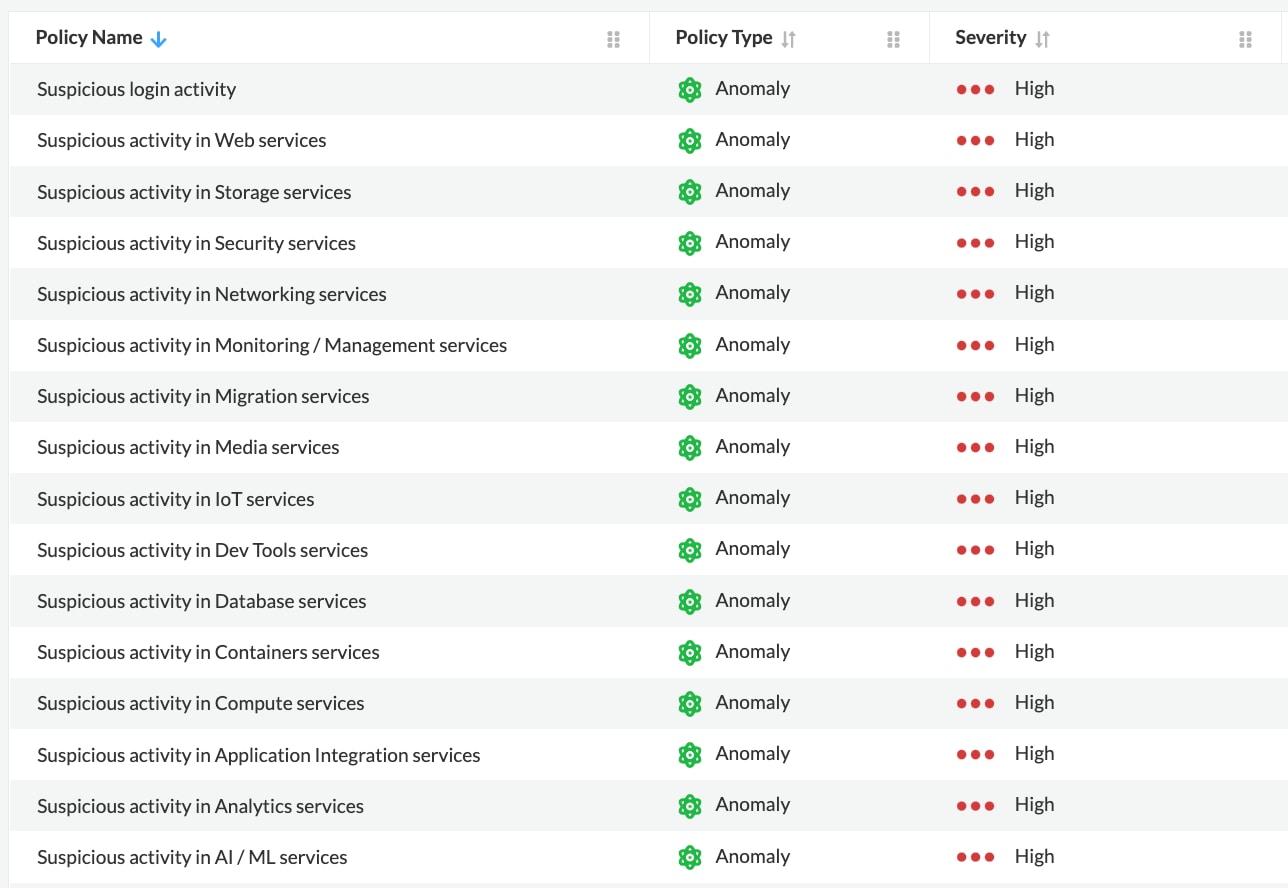
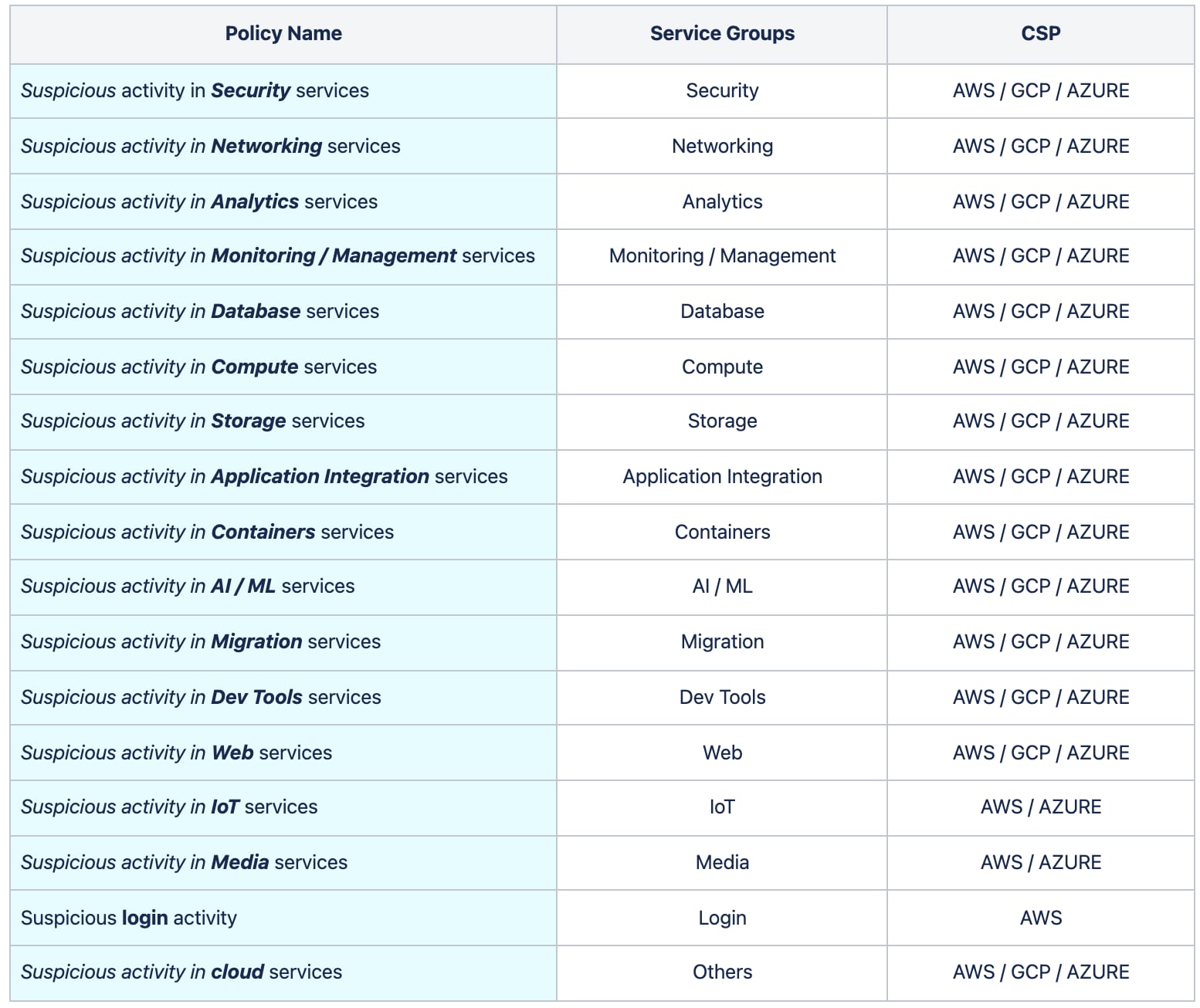
Commonly, the activities related to data exfiltration or cryptojacking attempts involve security sensitive operations such as making copies of VM images, attaching, or removing policies to an account to modify the permissions, adding, or removing keypairs, and so on. Prisma Cloud formulated the new anomaly policies based on the service group of the resources the user is trying to access from a TOR exit node. We categorized the cloud resources, from the Cloud Service Providers (CSPs), into 16 service groups and developed a policy for each service group as listed in the table below.
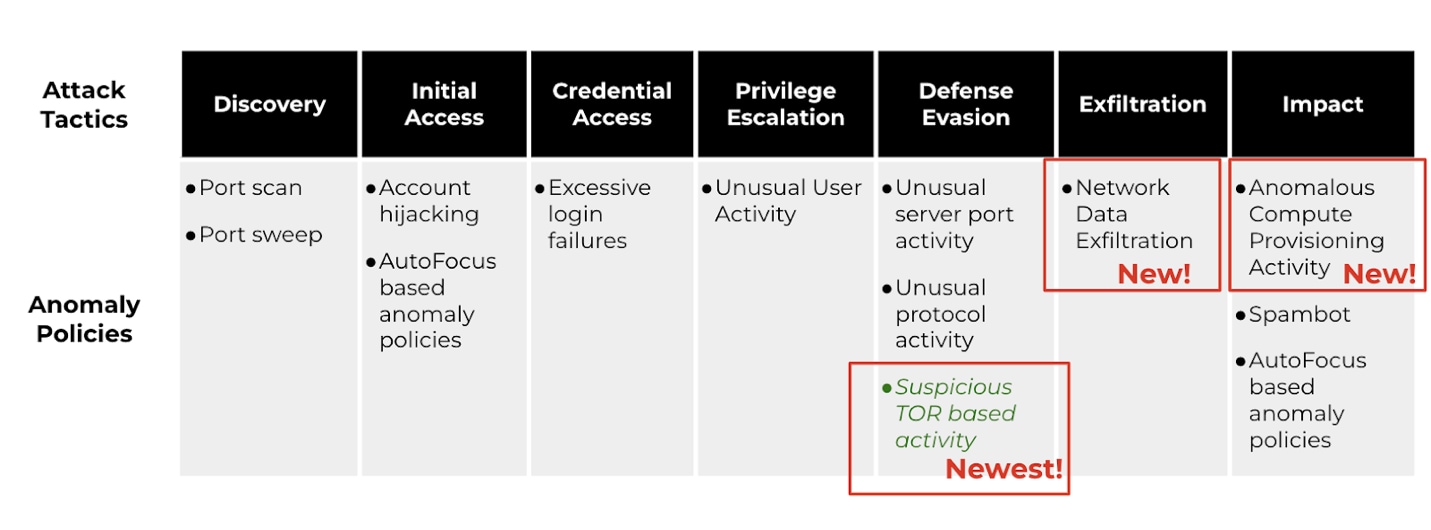
Prisma Cloud CSPM Threat Detection uses the MITRE ATT&CK framework for Cloud as our guiding principle.
The new TOR-based suspicious activity detection falls under the MITRE ATT&CK Tactics, “Defense Evasion”.
Let’s take a real customer case as an example: recently, a high-severity incident was detected for one of the Prisma Cloud customers in a Google Cloud environment. The incident involved activities covered under anomalous compute provisioning policy and suspicious activity policies. There were 4,000 compute instances created via 68 anonymous proxy IPs in a short duration including five TOR exit nodes and multiple other suspicious activities through four TOR exit nodes. It was later confirmed, by the customer, that the incident was a real cryptojacking attack. If the incident was not identified promptly by Prisma Cloud, the customer's potential financial loss could have been approx. $50,000 per day or higher!
Begin Detecting Suspicious User Behavior with Prisma Cloud
TOR-based suspicious activity detection is available in Prisma Cloud today. Existing Threat Detection customers can take advantage of this new capability. If you want to try out Threat Detection, then request a 30-day trial for Cloud Security Posture Management.
Related Blogs
Subscribe to Cloud Native Security Blogs!
By submitting this form, you agree to our Terms of Use and acknowledge our Privacy Statement. Please look for a confirmation email from us. If you don't receive it in the next 10 minutes, please check your spam folder.