Prisma Cloud Integration With AWS IAM Identity Center and AWS Tag Support
Prisma Cloud helps AWS customers have a deeper view into entitlements and enforce consistent, least-privilege access for all users accessing AWS infrastructure.
Identities have become the new cloud perimeter for security teams. Unit 42 threat researchers found an average of 3,400 cloud identities per company in a survey of 200 organizations. The alarming detail is that 99% of those identities had unused privileges, creating a massive attack surface.
The cloud infrastructure entitlement management (CIEM) capabilities built into Prisma Cloud help customers reduce identity risks. We’re thrilled to release new enhancements for AWS customers, specifically the integration between Prisma Cloud and AWS IAM Identity Center and new support for AWS tags.
Why AWS IAM Identity Center?
Users often access cloud infrastructure through identity providers (IdPs) or single sign-on (SSO) tools such as Azure AD or Okta. Using IdPs complicates permissions management because they need to be defined within each cloud account.
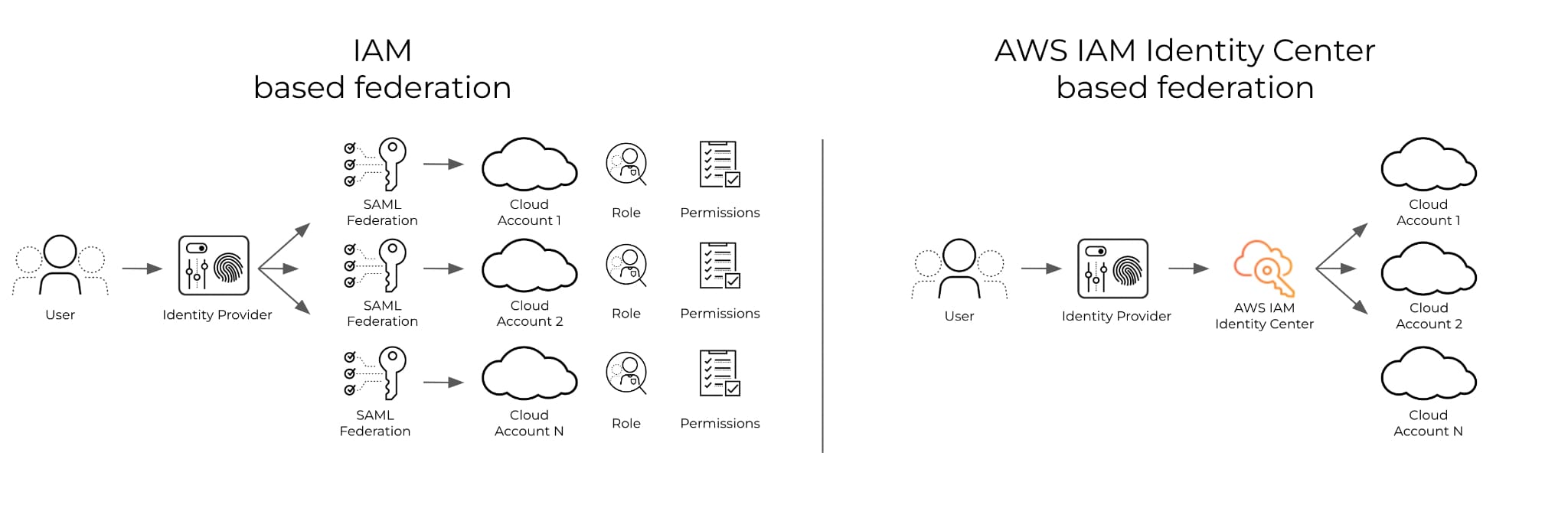
IAM Identity Center aims to centralize the management of roles and policies for AWS users and scale permissions management with a growing number of accounts. IAM Identity Center is a great first step to simplifying the management of your AWS user identities. To evaluate the overall identity risk in a cloud environment, though, you need to calculate the net-effective permissions, which is done by understanding which identities have access to critical infrastructure.
Net-effective permissions are too complex to calculate manually for many reasons, including:
- Identities extend beyond users to include machines and resources
- Companies are using multiple clouds with inconsistent IAM frameworks
- Identities may access cloud infrastructure through IdPs and SSOs
Automating permissions mapping is great for understanding IAM risk, but managing that risk is something else entirely. Through net-effective permissions calculations, security teams can highlight overly permissive identities and remediate them to enforce least-privilege access — ensuring that if unauthorized users gain access to a role, the damage they can do is limited.
Some CIEM tools can analyze data from AWS, IdPs and SSOs to automate cloud permissions and help security teams efficiently remediate cloud identity risk. But this requires CIEM providers to directly integrate and support individual IdPs, and adding more IdPs could take months to support. Here is where Prisma Cloud and AWS can help.
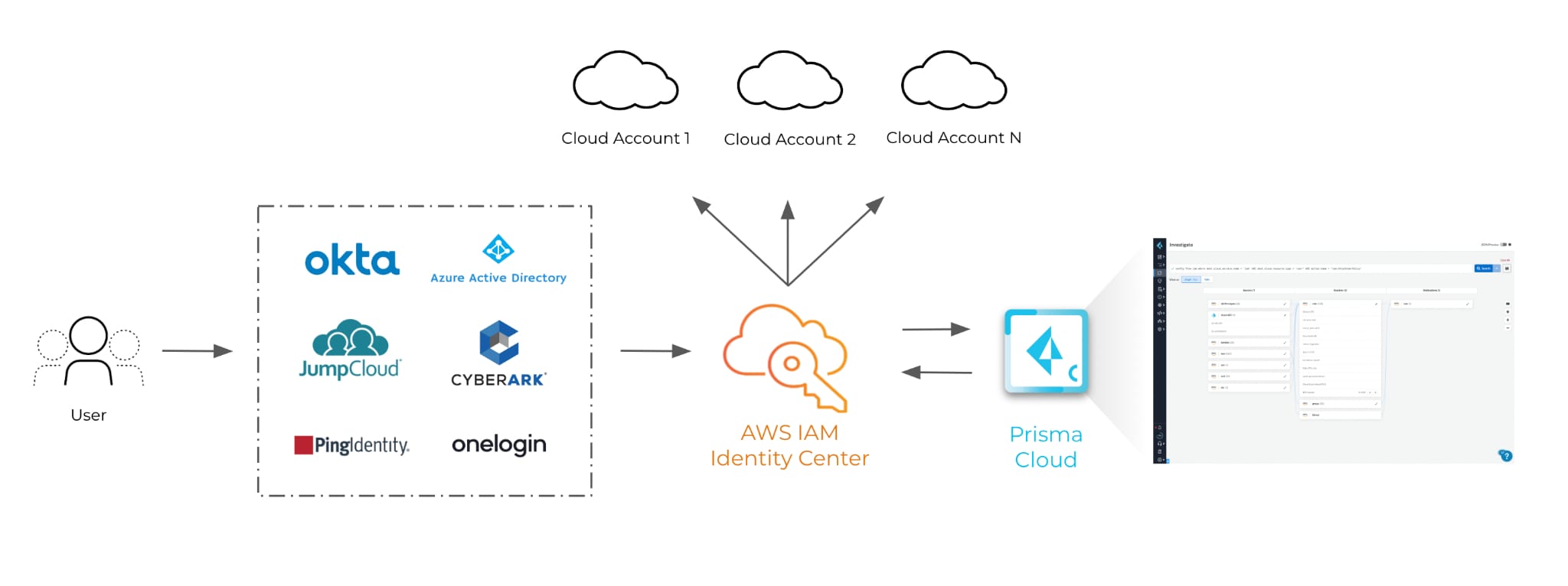
Prisma Cloud integrates with AWS IAM Identity Center to provide effective permissions mapping for any AWS user, regardless of the IdP. Prisma Cloud then aggregates this data with other data sources to automate net-effective permissions mapping so that overly permissive roles are highlighted and least-privilege can be enforced across multicloud environments. In addition to the visibility feature, users can create policies and user alerts to remediate risky permissions
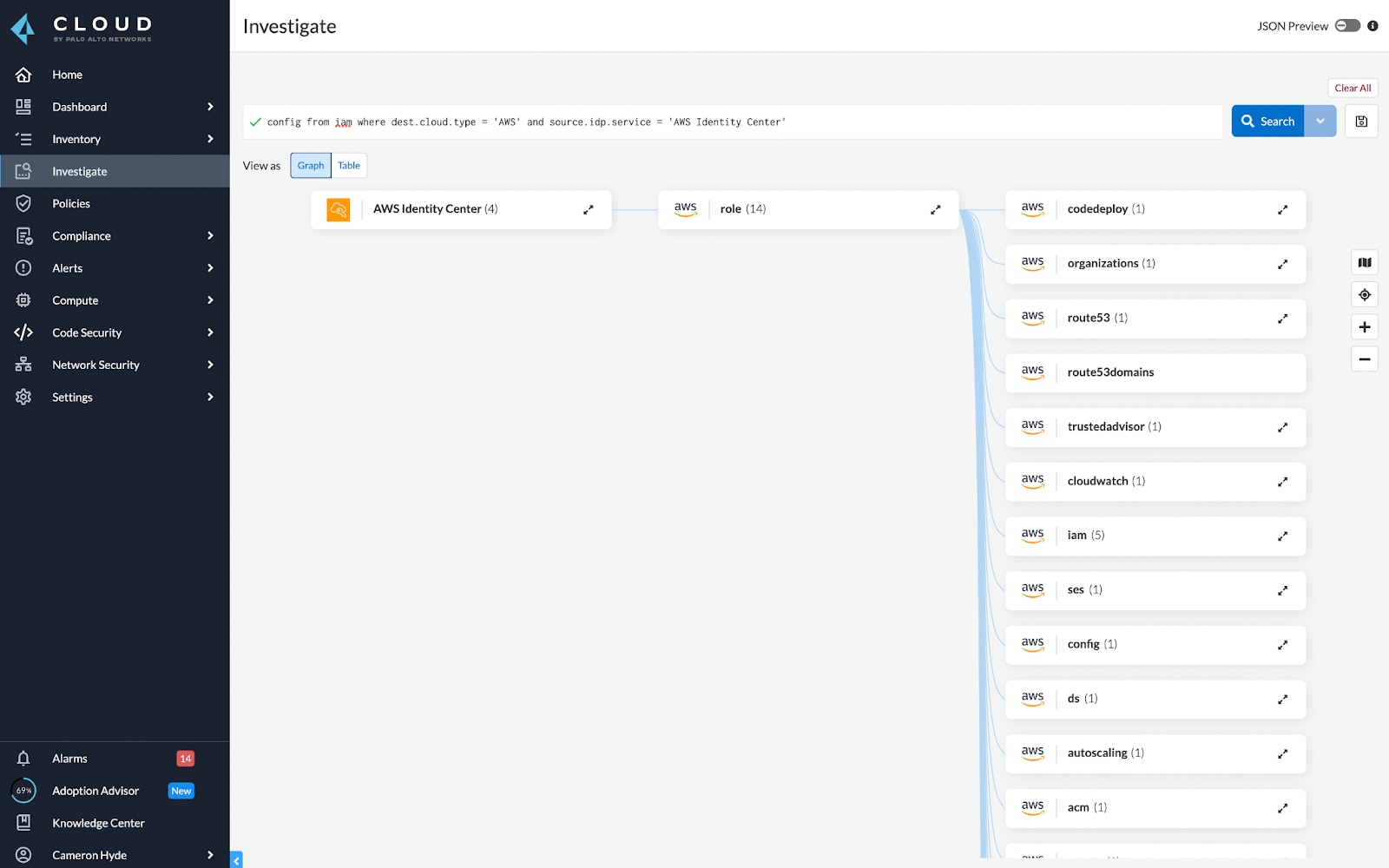
CIEM Support for AWS Tags
AWS users often use tags to group resources together, usually to classify resources based on application and business logic. Prisma Cloud now supports AWS tags within IAM investigation, so users can know what the higher level permissions are (permissions to/from application, and also within the application), in addition to the resource level permissions. This capability allows users to make custom policies more dynamic by using specific tags to group your cloud resources, roles, groups, policies, etc. when defining alert rules.
Learn More About Prisma Cloud
Prisma Cloud delivers CIEM across AWS, Azure and Google Cloud Platform. The integration with AWS IAM Identity Center and support for AWS Tags is available. If you’d like hands-on experience with these new capabilities, request a free 30-day trial.
Related Blogs
Subscribe to Cloud Native Security Blogs!
By submitting this form, you agree to our Terms of Use and acknowledge our Privacy Statement. Please look for a confirmation email from us. If you don't receive it in the next 10 minutes, please check your spam folder.