Detect DNS Threats for AWS Environments with Prisma Cloud
Given the prevalence of the Domain Name System (DNS) protocol on any type of network, it's essential for organizations to monitor DNS traffic for suspicious activity, as cyber attacks may leave traces in the DNS traffic logs. For instance a malware could download a payload from a URL known to host malware. On a global scale, 88% of organizations have suffered DNS attacks — with companies suffering an average of seven attacks per year at a cost of $942k per attack, according to the IDC 2022 Global DNS Threat Report.
Monitoring DNS traffic will allow you to detect incidents that can have serious consequences, including service downtime, resources and data theft, infiltration, or even malware infections.
DNS is still a common blind spot for many organizations, but the good news is Prisma Cloud can actively monitor DNS traffic on AWS with our agentless threat detection capabilities.
Prisma Cloud Surfaces DNS Attack Tactics
Prisma Cloud detects threats hidden in DNS traffic for AWS environments, including domain generation algorithm (DGA) activity, cryptomining domain request activity and DNS rebinding activity. AWS customers who use Prisma Cloud can thwart network exploits without reconfiguring their DNS or network infrastructure.
How It Works
Prisma Cloud delivers threat detection as a function of cloud security posture management (CSPM) and requires no agent installation. Instead, security practitioners can simply connect Prisma Cloud to their cloud environments, enable threat detection and the platform will surface threats and anomalous behaviors.
Prisma Cloud ingests data from several sources such as cloud configurations, network flow logs, audit events, and more — processing 1 trillion cloud events daily. Using this data, the context-driven platform leverages Palo Alto Networks Unit 42 threat intelligence, third party intelligence streams, machine learning (ML) and user and entity behavior analytics (UEBA) to identify threats lurking across cloud environments. With each threat detected, Prisma Cloud provides actionable remediation steps to help you respond.
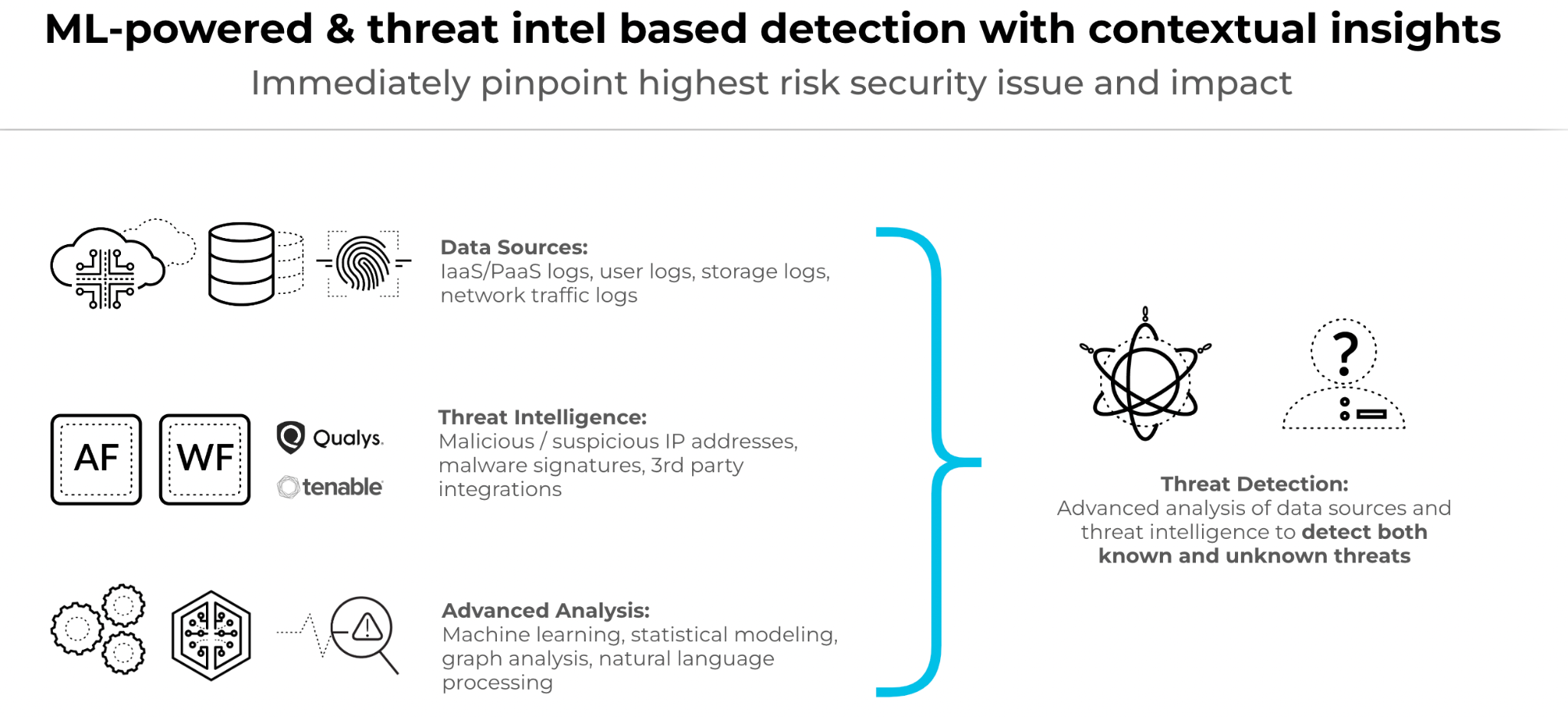
Additionally, Prisma Cloud integrates with AWS Route53 query logging service and analyzes DNS logs for indicators of compromise. Here are some examples of what Prisma Cloud can find:
Attacks Using Domain Generation Algorithm (DGA)
A domain generation algorithm (DGA) generates domain names based on a dynamic seed and an algorithm. Using this technique, attackers may register new random-looking domains for their victims to rendezvous with the attacker’s network. These randomly looking domains make the attacker’s network resilient to detection and block lists.
While DGAs tend to generate random-looking domain names, Prisma Cloud monitors the DNS queries and leverages advanced machine learning techniques to detect suspicious DGA domain request activities. An alert would be triggered when multiple potential DGA-looking domain name queries have been executed by one resource in the cloud environment. This alert may indicate the resource performing these domain name queries is compromised.
Cryptomining Domain Request Activity
Cryptojacking is the process of illegally exploiting computational resources to mine cryptocurrencies using systems that aren’t owned or maintained by the mining operators. It produces financial losses to the victims and gains for the attacker. As the value of cryptocurrencies soared, cryptojacking became one of the biggest security concerns of organizations. Since 2021, there’s been a 300% increase in cryptomining malware.
Enhancing its capacity to detect cryptomining activities based on audit event logs and network flow logs, Prisma Cloud now detects cryptomining activity traces left on DNS logs. With the always up-to-date threat intelligence, Prisma Cloud will identify client hosts inside the cloud environment that initiate suspicious DNS queries to domain names associated with known cryptomining pools.
DNS Rebinding Activity
DNS rebinding attacks can allow an attacker to bypass network security controls and gain unauthorized access to sensitive resources. The attack works by exploiting the way web browsers handle the same-origin policy, which is designed to prevent scripts from one domain from accessing resources on another domain.
In a DNS rebinding attack, an attacker controls a name resolver and a website hosting a malicious script. When a user or a service visits the attacker’s website with a browser capable of executing the malicious script, the attacker will trick the browser into holding the connection to force the browser’s DNS cache to expire, giving the attacker an opportunity to change DNS records to point to the victim's local network. If successful the attacker now has access to internal web applications, such as the AWS Metadata service.
Detecting DNS rebinding attacks in cloud environments is essential as headless browsers become increasingly popular for web scraping, automated testing of web applications, and web analytics. With Prisma Cloud DNS rebinding activity detection capabilities, you will be able to cover typically overlooked security blind spots.
Customizing Prisma Cloud Threat Detection
Prisma Cloud offers granular control of threat detection, allowing customers to tune DNS-based threat detection settings for their distinct requirements.
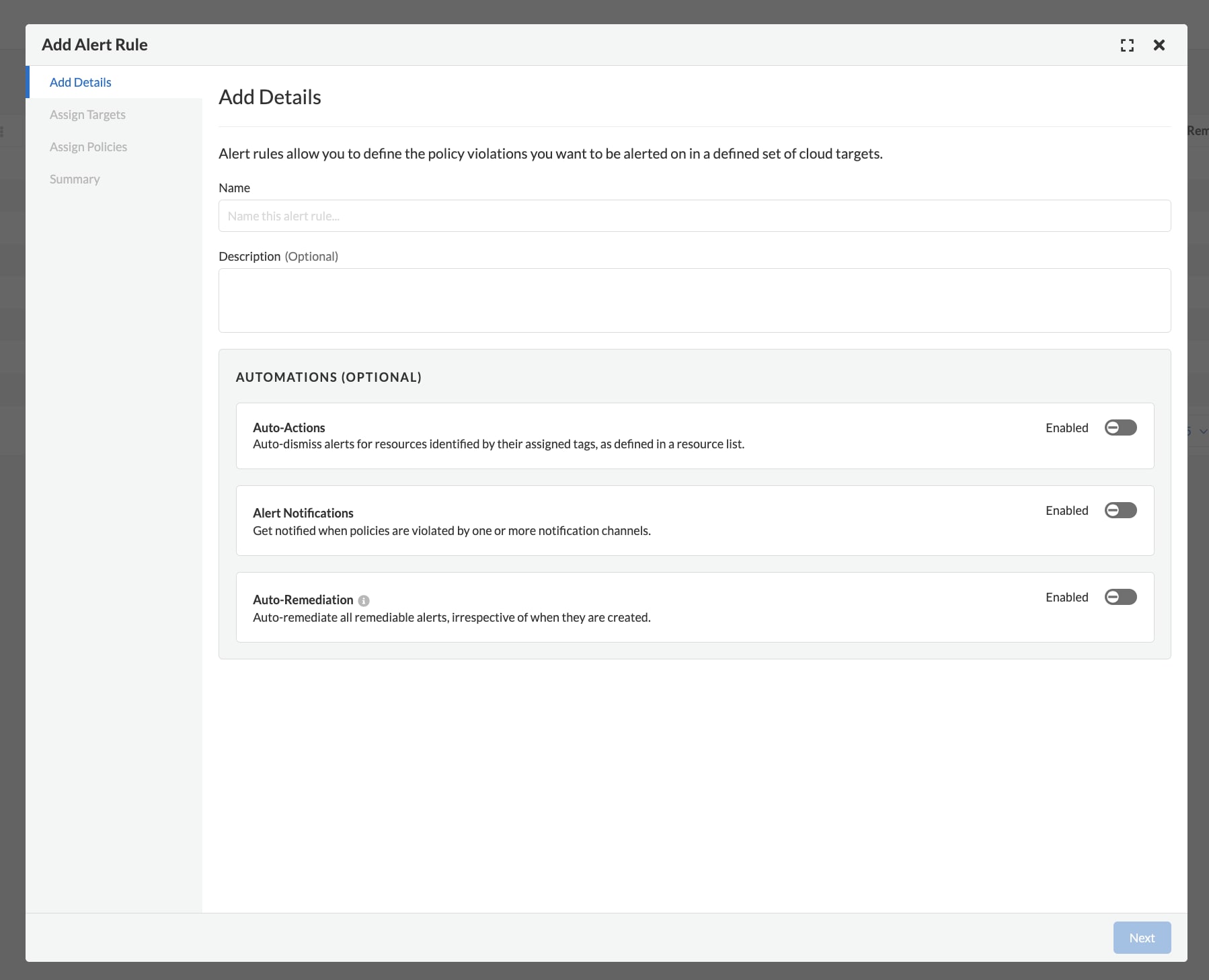
Alert Rules: Allow customers to define the policy violations in a selected set of cloud accounts for which they want to trigger alerts for the DNS-based threat detection.
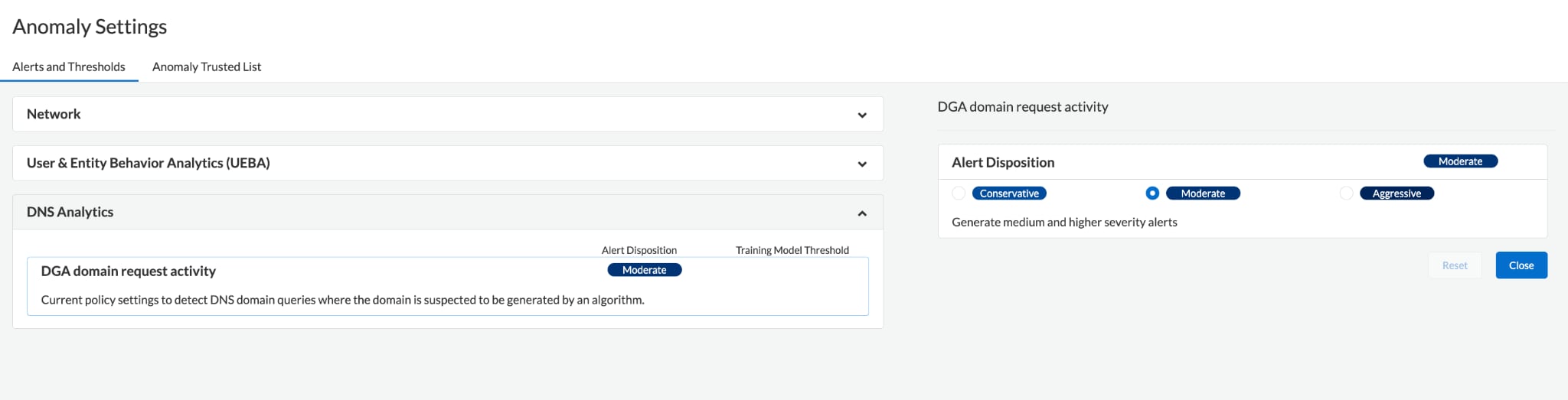
Alert Disposition: Modify what level of the DGA domain request activity alerts would be notified, from every suspicious incident to only the highest severity alerts.
Trusted Lists: Prevent legitimate activities (e.g., vulnerability scanning or PenTest tools) from generating alerts for the DNS-based threat detection.
Begin Detecting DNS-Based Threats with Prisma Cloud
Prisma Cloud customers on AWS can now avert DNS-based attacks. If you want to test drive threat detection capabilities from Prisma Cloud, request a 30-day trial of Cloud Security Posture Management.
Related Blogs
Subscribe to Cloud Native Security Blogs!
By submitting this form, you agree to our Terms of Use and acknowledge our Privacy Statement. Please look for a confirmation email from us. If you don't receive it in the next 10 minutes, please check your spam folder.