Executive Summary
In this article we outline a comprehensive approach to detecting covert malicious communication as part of Palo Alto Networks’ Precision AI® advanced capabilities, specifically focusing on command and control (C2) and data exfiltration. We will provide a rare glimpse into our thought process, implementing a "divide and conquer" strategy for classification. This strategy leverages diverse data sources like endpoint detection and response (EDR) and network detection and response (NDR) for a holistic extended detection and response (XDR) view. A case study provides readers with insight into how initial stealth tactics, like mimicking legitimate software and using valid domains, ultimately generate anomalies that advanced security controls could detect, such as missing digital signatures and unusual communication patterns.
Defining The Problem
Effective cybersecurity, even when it involves advanced AI-infused models, begins with a clear understanding of the threats we aim to counter. To ensure comprehensive coverage for C2 communication and data exfiltration, we must first define the problems that we intend to solve.
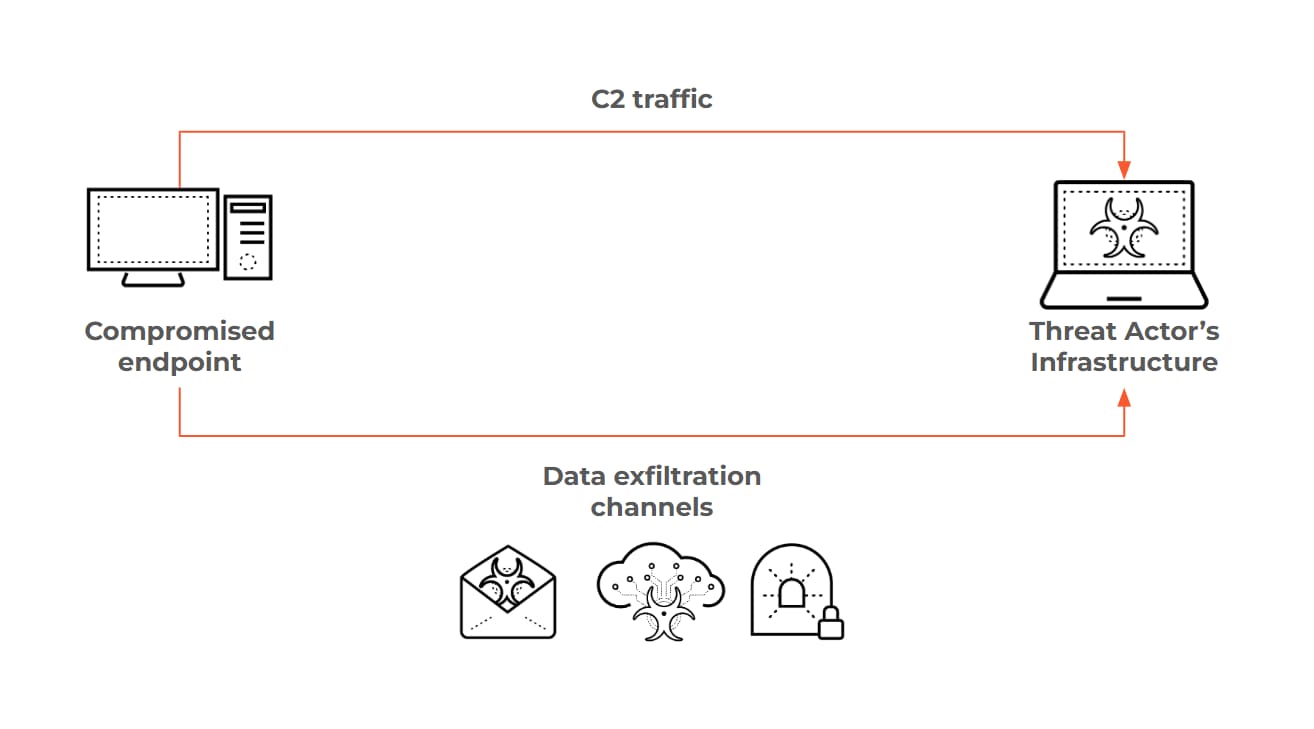
We decided to scope our research to these concepts:
- C2 Communication: Covert, bi-directional communication channel established between a compromised system and an attacker-controlled command and control server after initial malware installation or system compromise has occurred.
- Data Exfiltration: A specific subset of malicious communication relates to the unauthorized, unidirectional transfer of sensitive data from a compromised network or system to an external destination. This exporting of data represents a significant breach of confidentiality and can lead to severe consequences for organizations, including financial losses, reputational damage, and regulatory penalties.
Modern endpoints are extremely complex with countless processes communicating with each other and across networks, classifying “bad” vs. “good” comms is an extremely difficult task. By properly scoping what we will tackle, we can tailor our security solutions to detect, prevent, and respond effectively to the distinct, yet often interconnected, stages of a cyberattack lifecycle. This allows us to develop more robust and targeted defenses, ultimately providing superior protection to our customers against the evolving threat landscape.
Methodically Defeating C2 Infrastructure
Divide and Conquer
Now that we’ve defined the problem, we need to plan how we validate and improve our coverage. The most effective way of doing so is solving clear sub-problems given how immense the world of C2 and data exfiltration is. In order to do so, we classified various genres of malicious clients and servers, which in turn allowed us to pick appropriate features for each “C2 flavor”.
For instance, the methodologies we use to detect the abuse of living off the land binaries (LOLBINs) for C2 purposes differ significantly from those we use to identify a novel, recently compiled binary. Similarly, data exfiltration to a legitimate cloud storage service presents a different detection challenge compared to uploading data to an IP address hosted on an internet service provider (ISP) that is known to be suspicious. Each scenario necessitates a tailored approach to feature selection and detection logic.
The volume and diversity of data make it increasingly difficult to figure out which features to include, and which to exclude from our detection logic. At Cortex, we integrate a multitude of data sources, combining classic EDR and NDR data. This combined approach provides a more holistic and accurate view of potential threats than traditional security products.
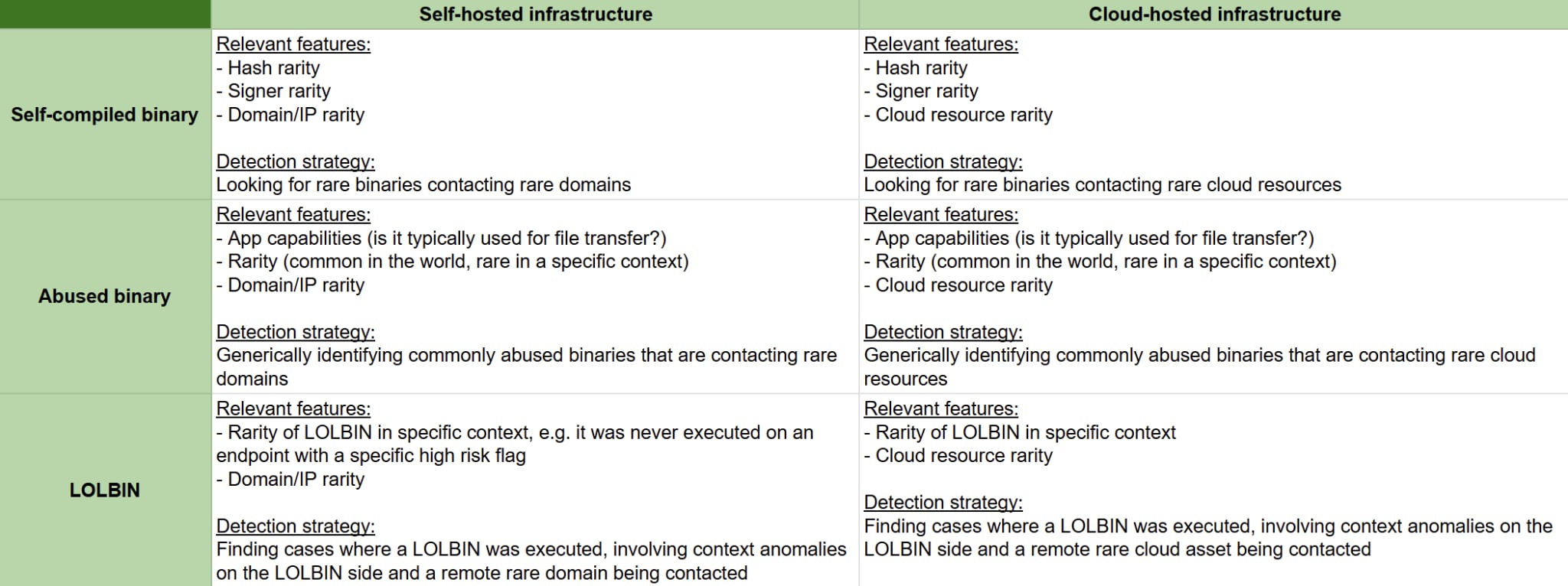
Having defined the scope of the problem and the types of entities we are likely to encounter, we then cataloged every feature that could prove useful in this context. Ranging from a binary’s signature status and the rarity of its signer to the intricate TLS fingerprints of both client and server communications, this comprehensive list of features helps us to capture a broad spectrum of threat actors’ techniques.
Detection Strategies
As part of our classification process, we matched each identified feature to its appropriate use case, for example:
- A binary compiled by a sophisticated threat actor is unlikely to have a commonly used binary signing certificate, even if it is signed. This makes the rarity of the signer an excellent feature for detecting bespoke malware.
- A C2 server set up by a threat actor and associated with a newly registered domain might seem like a surprising technique in the current threat landscape, but as it turns out, this tactic provides readily accessible, "low-hanging fruit" features that we can leverage to detect anomalous hosts and their malicious activities.
The following table summarizes some of the features we’ve matched to a use case in our research:
A Case Study - Generic Detection of a Clever Malvertising Campaign
Using our newly crafted detection strategies we tracked down multiple advanced malicious campaigns. We are sharing with you one of these cases which demonstrates how our proper meticulous process proved itself against a threat actor leveraging creative tactics.
Malvertising Infection Vector
Since early August 2025 we have identified multiple malvertising campaigns that target users who search for the GitHub desktop client. In the case that we study here, the threat actor combined dangling commits with a more traditional malvertising campaign.
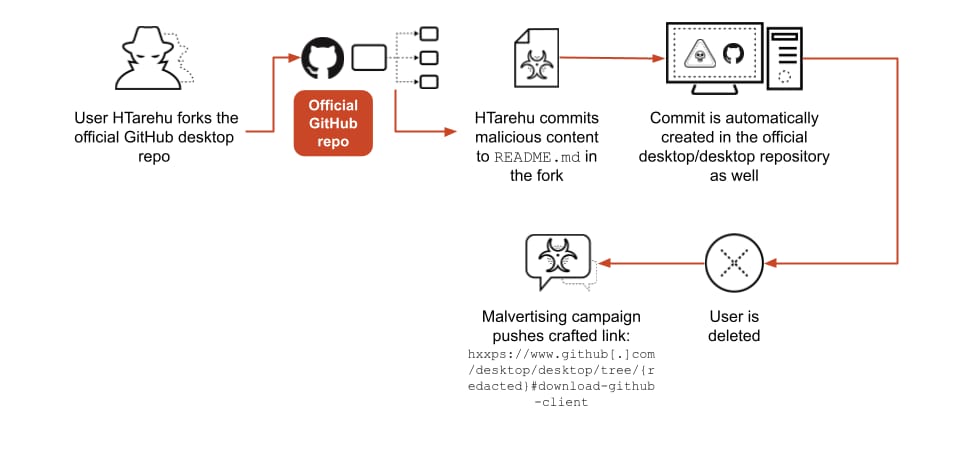
The campaign was designed to work as follows:
- The threat actor creates a disposable GitHub user.
- The user forks the target repository.
- A malicious commit is added to the user’s downstream fork.
- The threat actor crafts a URL that includes the downstream commit hash with the upstream original repository address.
- The threat actor pushes the crafted link to the malicious commit in a malvertising campaign, abusing the trusted upstream repository.
We identified several malicious commits, including one in which the GitHub user @hTarehu forked the official GitHub desktop client repository, and added a malicious commit to the downstream repository on August 4, 2025.
The sole change was to the README.md file, in which the threat actor embedded a section containing links to a malicious binary.
Next, the threat actor crafted the following link:
hxxps://github[.]com/desktop/desktop/tree/636f5d478fa774635da5b25ecb842822ab444009#download-github-desktop
Next, the actor promoted this link with a sponsored ad, presenting the malicious URL as an official verified website, in an effort to infect users who search for and attempt to download the GitHub desktop client.
Stealth - At What Cost?
The ingenuity of the threat actor's infection vector inadvertently generated unexpected anomalies. A crucial aspect of their deception involved leveraging a widely used and seemingly innocuous application – GitHub’s official desktop client – as a cover for their malicious activities. Further adding to the impression of legitimacy, the malicious payload was distributed from what appeared to be the verified official repository of this application. Moreover, the domain name promoted throughout their malvertising campaign was entirely legitimate, further cementing the illusion of authenticity for unsuspecting victims.
However, these very tactics were a double-edged sword. Although highly effective in the social engineering scheme to lure victims into downloading the malicious software, ultimately this approach became a point of vulnerability. Despite its effectiveness, this social engineering scheme is detected by advanced security controls, which identify the discrepancies between the initial stage of the malware and a typical, legitimate client downloaded from the authentic repository. An example of such a feature is the absence of a valid digital signature on the downloaded executable, which is a fundamental characteristic of legitimate software. Furthermore, the download itself did not originate directly from GitHub, the purported source, but rather from a third-party site – a highly suspicious deviation for an official client download.
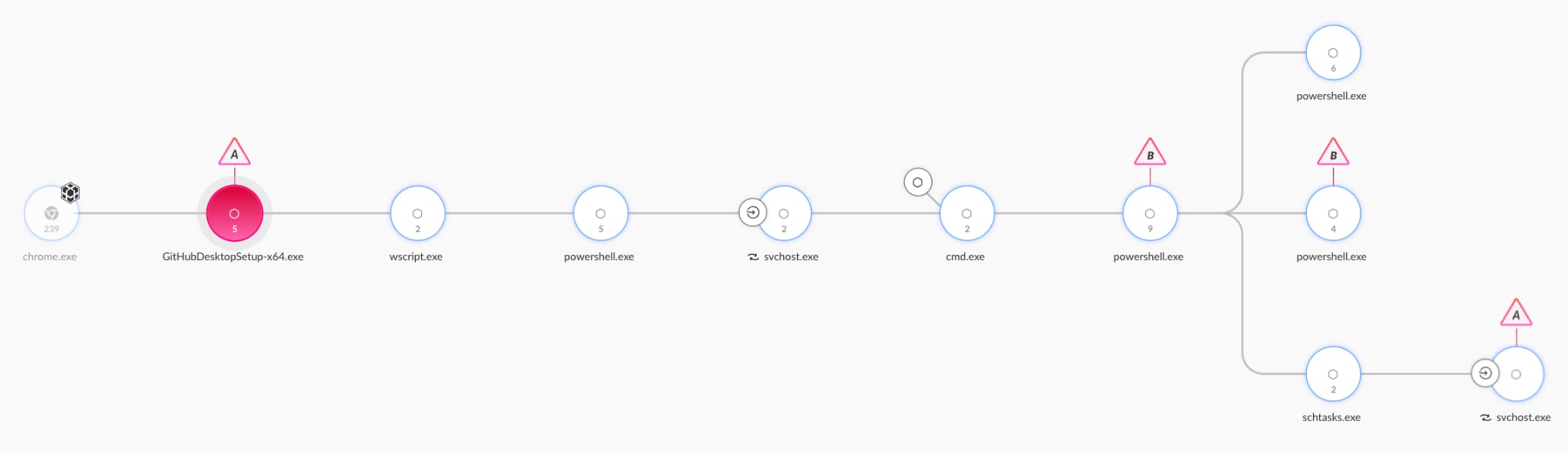
Following the download of this fake client, it proceeded to establish communication with additional staging servers. These servers, unlike those associated with the legitimate GitHub desktop client, were entirely new and previously unobserved. This behavior raises additional red flags for sophisticated security monitoring systems. The communication patterns and destinations were highly atypical for the genuine application, providing additional evidence of the malicious nature of the downloaded software.
This anomalous network activity would be a key indicator for detection systems focused on identifying command and control communications. This attack is easily detected using our divide-and-conquer strategy. We identified a binary compiled by the attacker, disguised as a legitimate client, communicating with a C2 server self-hosted by the attacker and never contacted before by the benign client. The features that we analyzed have proven to be a valuable resource, as they enable us to reveal numerous discrepancies that we use to flag this attack.
Conclusion
Our journey started in rigorously defining C2 communication and data exfiltration, and systematically categorizing malicious entities and their associated features. This in turn allowed us to get the most of our precision AI models, creating an optimal robust framework for detecting covert communication. This approach, demonstrated in our detailed case study on a clever malvertising campaign, highlights the effectiveness of integrating diverse data sources like EDR and NDR. Our continuous adaptation to evolving threat actor tactics, coupled with a thorough validation of detection strategies, ensures that our security solutions provide comprehensive and superior protection against sophisticated cyberattacks.
Appendix
C2 and Exfiltration Detectors
- Rare binary connected to a rare cloud resource
- Rare binary connected to a rare external host
- Windows LOLBIN executable connected to a rare external host
- Scripting engine connected to a rare external host
- A compromised process accessed a rare external host
- A commonly abused process connected to a rare external host
- A commonly abused process connected to a rare cloud resource
- A process connected to rare external host
- A process connected to a rare cloud resource
- Rare process created an SSH session to an uncommon cloud resource
- Rare process created an SSH session to an uncommon external host
- Rare communication over email ports to external email server by unsigned process
XQL - Malicious GitHub Client
// Description: Querying Potential Fake GitHub Client Cases
dataset = xdr_data
| filter event_type = PROCESS and action_process_file_web_mark != null
| alter ReferrerUrl = action_process_file_web_mark -> ReferrerUrl
| filter ReferrerUrl ~=
“https:\/\/github.com\/desktop\/desktop\/tree\/?[0-9a-f]{40}\?tab=readme-ov-file”
| fields agent_hostname, actor_effective_username, actor_process_image_path, ReferrerUrl
| dedup ReferrerUrl
Indicators of Compromise - Malicious GitHub Client
Known malicious commits
- 636f5d478fa774635da5b25ecb842822ab444009 (associated with @hTarehu)
- 629f3ab77b0c6840618029d39869d078f8a5a694
- 3b3e14cec9f2c7f9567bb1a50ece12d4eb337305
- a48188b0d5bdc3e8728cb37619cc51f7392b086f
Malvertised link format
hxxps://github[.com/desktop/desktop/tree/636f5d478fa774635da5b25ecb842822ab444009?tab=readme-ov-file&gad_source=1&gad_campaignid={redacted}&gclid={redacted}#download-github-desktop
Associated user
@hTarehu (vilenakoroleva000@rambler.ru)
Malicious domains
hxxps://downloadingpage[.]my
hxxps://feelsifuyerza[.]com
hxxps://git-desktop[.]app
hxxps://gitpage[.]app
hxxps://oguiuweyqwe[.]online
hxxps://poiwerpolymersinc[.]online
hxxps://powiquwieree[.]com
hxxps://slepseetwork[.]online
Payloads (SHA256)
0b9afc9019f3074c429025e860294cb9456510609dd1dca8e8378753ade5a17e
ec89c0ffc755eafc61bbf3b9106e0d9d7cbfaa9e70fbe17d9e4fbb9a7d38be64
e252bb114f5c2793fc6900d49d3c302fc9298f36447bbf242a00c10887c36d71
ad07ffab86a42b4befaf7858318480a556a2e7c272604c3f1dcae0782339482e
efcf5fe467f0ba8f990bcdfc063290b2cf3e8590455e6c7c8fe0f7373a339f36
ed1811c16a91648fe60f5ee7d69fe455d0a3855eebb2f3d56909b7912de172fd
2a1c127683dba19399cc6516d5700d4e756933889dad156cd62b992aaf732816