Organizations must be able to absorb economic stress, recover quickly, and adjust to changing business circumstances to be successful. Business resilience alone, however, is insufficient in today’s digital-first world. With the increasing adoption of SaaS apps, hybrid workers, and the potential for irreparable harm from a single data breach or ransomware attack, business resilience must extend to cyber resilience with a multilayered web defense.
Palo Alto Networks Remote Browser Isolation (RBI) coupled with Cloud Secure Web Gateway (SWG) and Enterprise DLP present a formidable combination that not only fortifies web defenses, but improves user productivity and streamlines operations.
Introducing the Next-Generation RBI for Prisma SASE
RBI is an advanced security approach that separates web browsing activities from local devices by executing them in a secure remote environment. The browser session occurs on virtual machines hosted in the cloud, confining any malicious code encountered during browsing to the isolated session and poses no threat to the user's device or network.
However, running browser sessions far away from local devices has the potential for user disruption. Throughout its evolution, traditional RBI approaches have tried but fallen short when governing the tension between performance and security.
Palo Alto Networks Next-Generation RBI for Prisma SASE creates a no-code execution isolation channel between users and browsers to keep zero-day web threats at bay, never allowing malicious files to execute on user machines.
Unlike traditional pixel-pushing reconstruction that causes high latency or DOM-based approaches that expose security gaps, Palo Alto Networks RBI isolation platform combines the latest rendering technologies for superior isolation outcomes while simultaneously delivering a near-native user experience.
Zero-Day Threat Protection
Zero-day vulnerabilities exploit unknown and unpatched software flaws, posing significant challenges for traditional cybersecurity solutions. However, RBI neutralizes zero-day threats by executing a web browsing session in a protected environment away from the local device. RBI mitigates the risk of system compromise by rendering zero-day exploits harmless once the web browsing session ends.
Reducing the External Attack Surface
RBI minimizes the attack surface by preventing webpage code from executing on local devices.
RBI confines malicious code, malware, and phishing attempts to the isolated browser session, eliminating the risk of unauthorized access to the user's device or sensitive corporate data. This approach reduces the potential impact of successful attacks and strengthens the overall security posture.
High-value users with access to sensitive data are often targets of these attacks, and RBI can further reduce the attack surface with granular user controls that help keep sensitive data safe and secure.
Near-Native Web Browsing User Experience
RBI leverages modern web technologies to ensure that web applications render in a way that is nearly native to the user, providing a seamless user experience between a web browsing session that happens inside or outside isolation. We have engineered our isolation technology to disallow code execution on the user’s machine, providing uncompromising security for even the most dynamic and demanding web applications.
RBI Natively Integrated with SWG and DLP
SWGs act as a proxy between users and the internet, monitoring and controlling all web traffic for potential threats. It applies various security measures, including URL Filtering, content inspection, and antivirus scanning, to prevent unauthorized access and to block threats. Along with these services, DLP helps discover, monitor, and protect sensitive data across every network, cloud, and user.
Combining RBI with SWG and DLP creates a multilayered defense against modern web threats.
SWG provides comprehensive security checks on web traffic before and after it reaches the remote browser isolation environment. This proactive approach ensures that even if a threat bypasses one layer of security, another layer will catch it, significantly reducing the risk of zero-day web attacks.
When viewing through a data security lens, DLP policies work holistically on a user’s session, regardless of whether the user is in or outside of isolation. RBI introduces a host of granular browser-level controls that help to augment the delivery and enforcement of data security to the user level, working hand-in-hand with existing Enterprise DLP policies.
Centralized Management and Enforcement with Prisma SASE
Organizations can enforce consistent security policies across all web traffic for all users from all locations. SASE ensures that all user activities, including web browsing, adhere to corporate security guidelines, restricting access to risky or unknown websites. At the same time, RBI maintains the isolation principle, providing an extra layer of defense against potential zero-day threats arising from user interactions with the web.
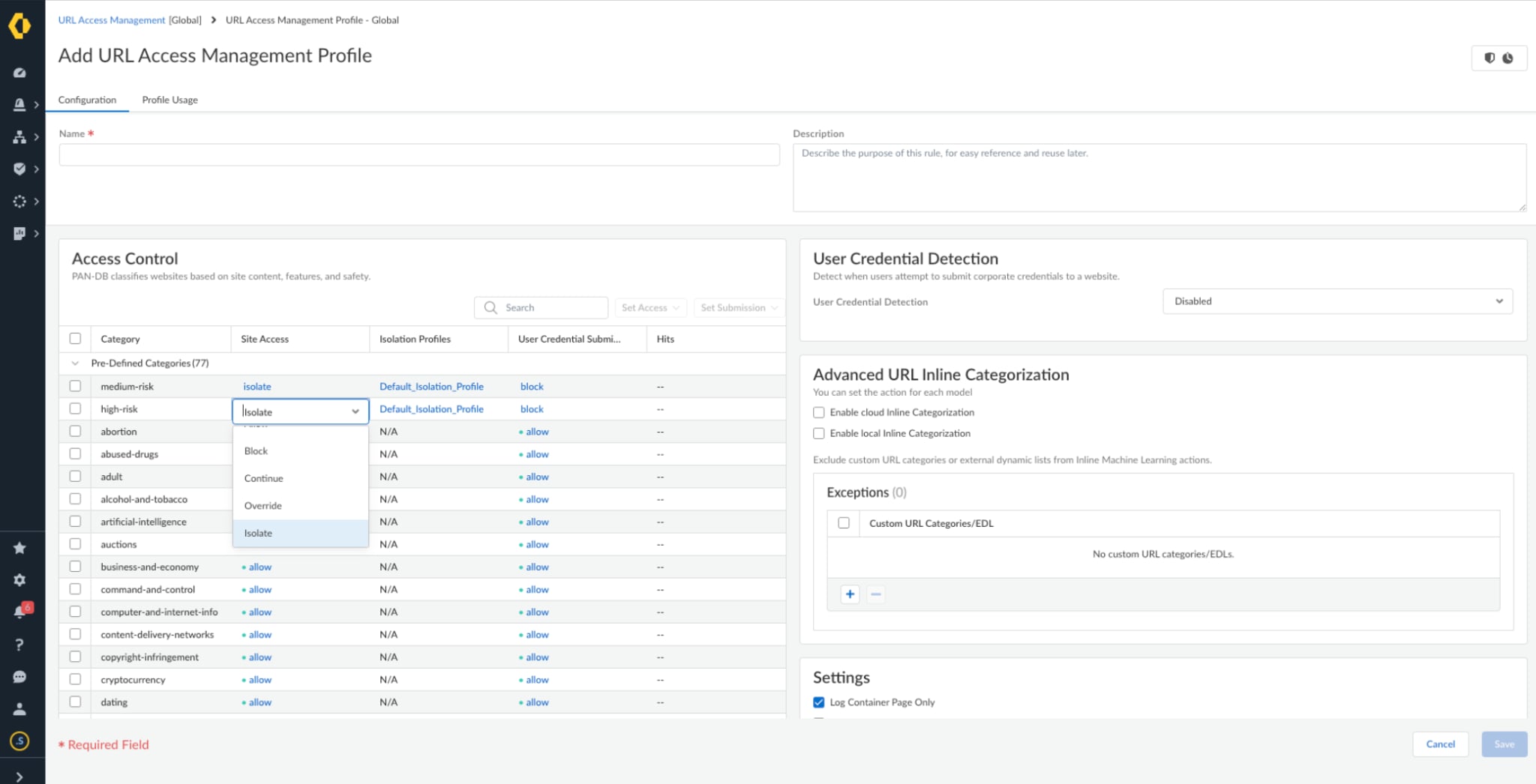
Figure 1: RBI isolation profile natively integrated with Prisma Access
Applying the isolation context to existing security policies makes it easy to start isolation for any desired segment of traffic or based on the many levers that already exist as part of Prisma Access. Organizations can monitor and view logs from user traffic in one single-pane-of-glass, allowing for an increasingly simplified and consolidated troubleshooting and investigation process.
Embracing the Power of RBI with Prisma SASE
Prisma SASE fuses RBI with SWG and DLP functionality, representing one of the most formidable defenses against web attacks with a multilayered approach for enhanced protection against zero-day threats.
By reducing the attack surface and enforcing consistent security policies, a natively integrated solution fortifies cybersecurity defenses for businesses and individuals. Moreover, the streamlined web browsing experience ensures faster access to web content and cross-product compatibility, fostering productivity while maintaining the highest levels of data protection.
Combining the power of RBI with SWG and DLP is an intelligent investment in robust cybersecurity and a proactive step toward a safer, more efficient digital future.
Learn more about RBI with Prisma SASE and all of our other recent AI-powered SASE innovations at our SASE Converge 2023 on-demand event.