Host Security: Automating Protection for VMs Across Public Clouds
As customers extend their deployments across multiple clouds, visibility and standardized security coverage remain a key challenge in multi-cloud management. Further, as these organizations begin to scale these diverse environments, most find that it is not sustainable to manually detect and confirm configurations for each resource.
In the January 2021 release for Prisma Cloud, we added the ability to automatically scan Amazon Web Services (AWS) accounts, allowing users to discover all cloud hosts and determine their protection coverage.
Subsequently, in April 2021, we added support for discovery across all major cloud providers, including Azure and Google Cloud, with support for automated protection with auto-deployment of the Defenders on AWS EC2 instances.
Now as a part of the August 2021 release, we are extending that coverage and supporting the automated deployment of Defenders on unprotected hosts across Azure and GCP. Ultimately, these capabilities allow easier deployment and management of the agents that are required to protect cloud VMs.
Visibility in Clouds
Prisma Cloud automatically discovers machines (instances) on AWS, Azure, and Google Cloud. Users can import or add their cloud service accounts in Prisma Cloud Compute and kick off a discovery scan automatically. The scan identifies all the virtual machines across all regions within those accounts, and populates the Cloud Radar.
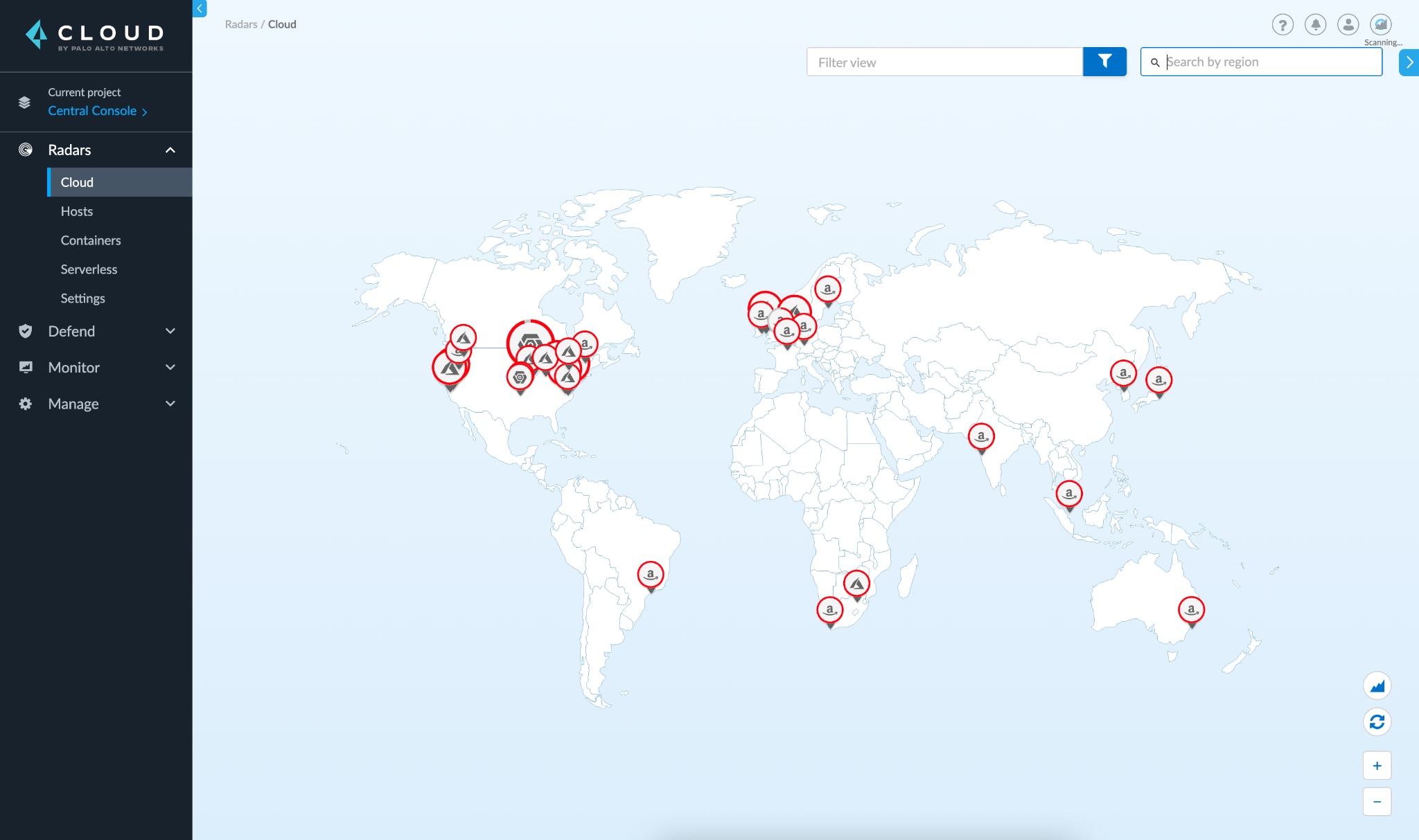
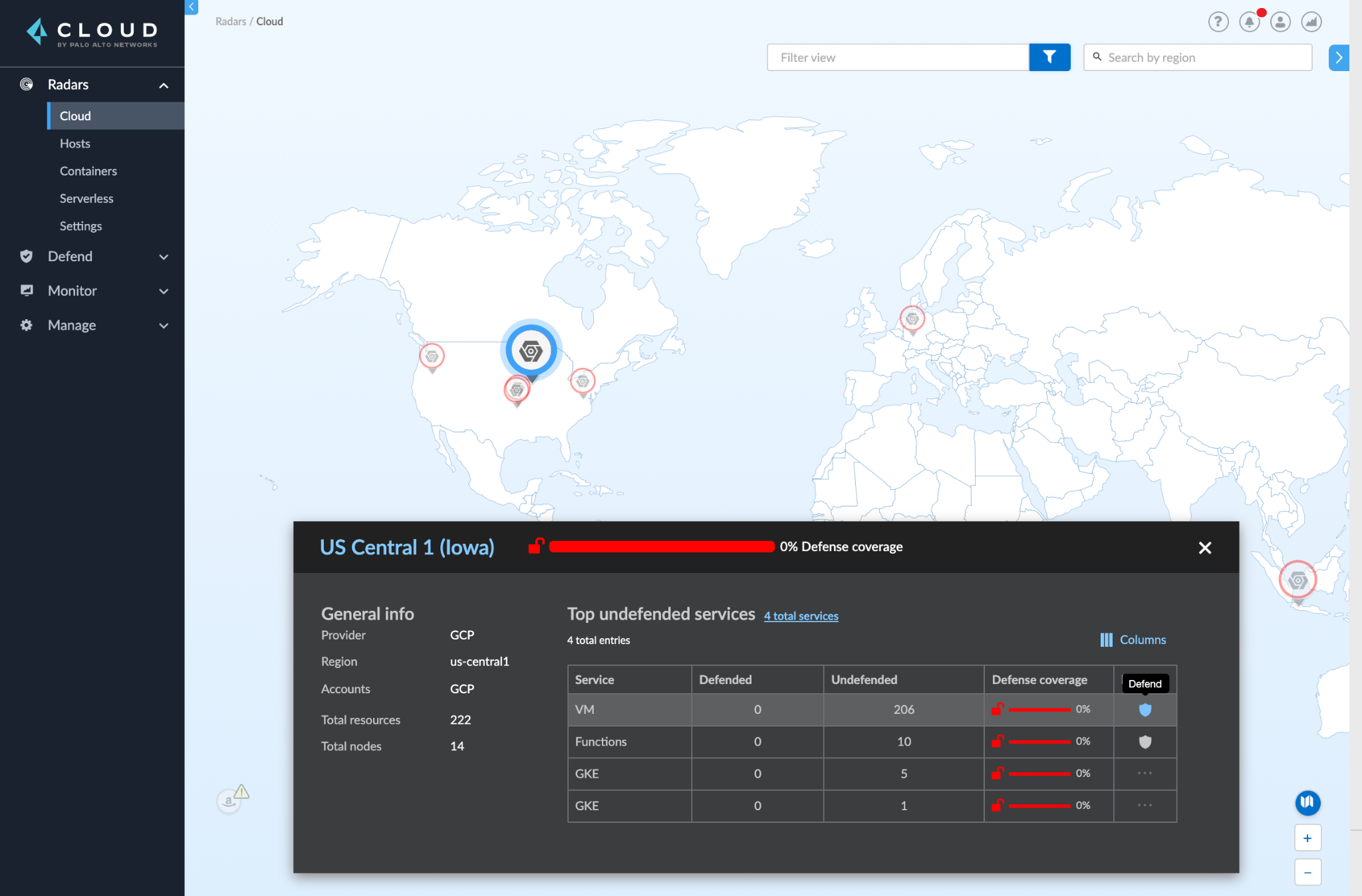
Then, users can drill down into the specific cloud provider and region to view the details of the discovered assets and their security coverage status, as highlighted in the screenshot below.
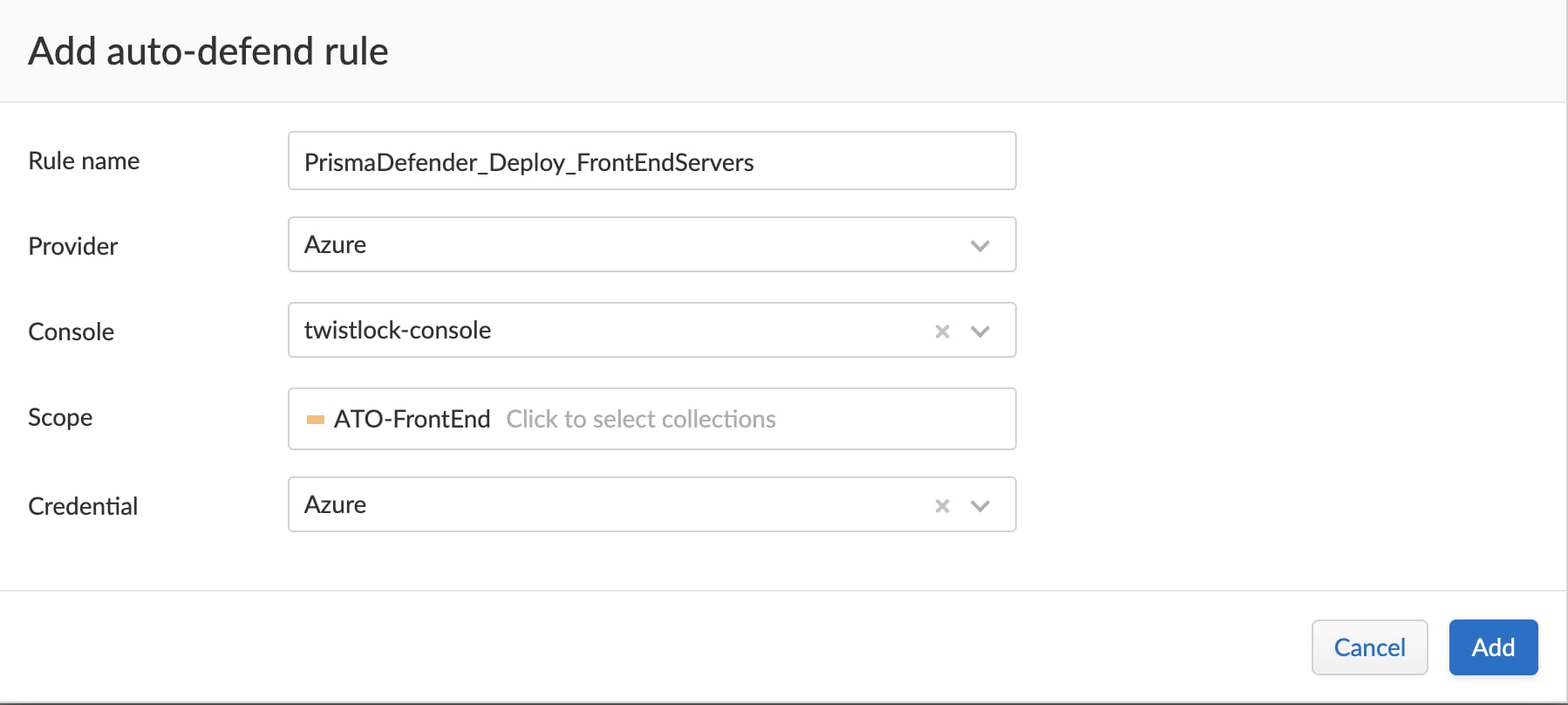
Host Auto-Protection for Azure
Prisma Cloud uses the Azure VM agent’s Run Command option to deploy Host defenders. To use this feature, users need to ensure the subscription is configured with the necessary permissions to invoke the run command.
Users can then create one or more auto-defend rules, and use filters like account, region, and tags to further target hosts in specific areas of their deployments.
Host Auto-Protection for Google Cloud
For auto-deploying Defenders on Google Cloud Compute Engine Instances, Prisma Cloud uses the OS Patch Management service. With sufficient access to hosts, users can automate the deployment of the Defenders across all unprotected Linux hosts across the global regions.
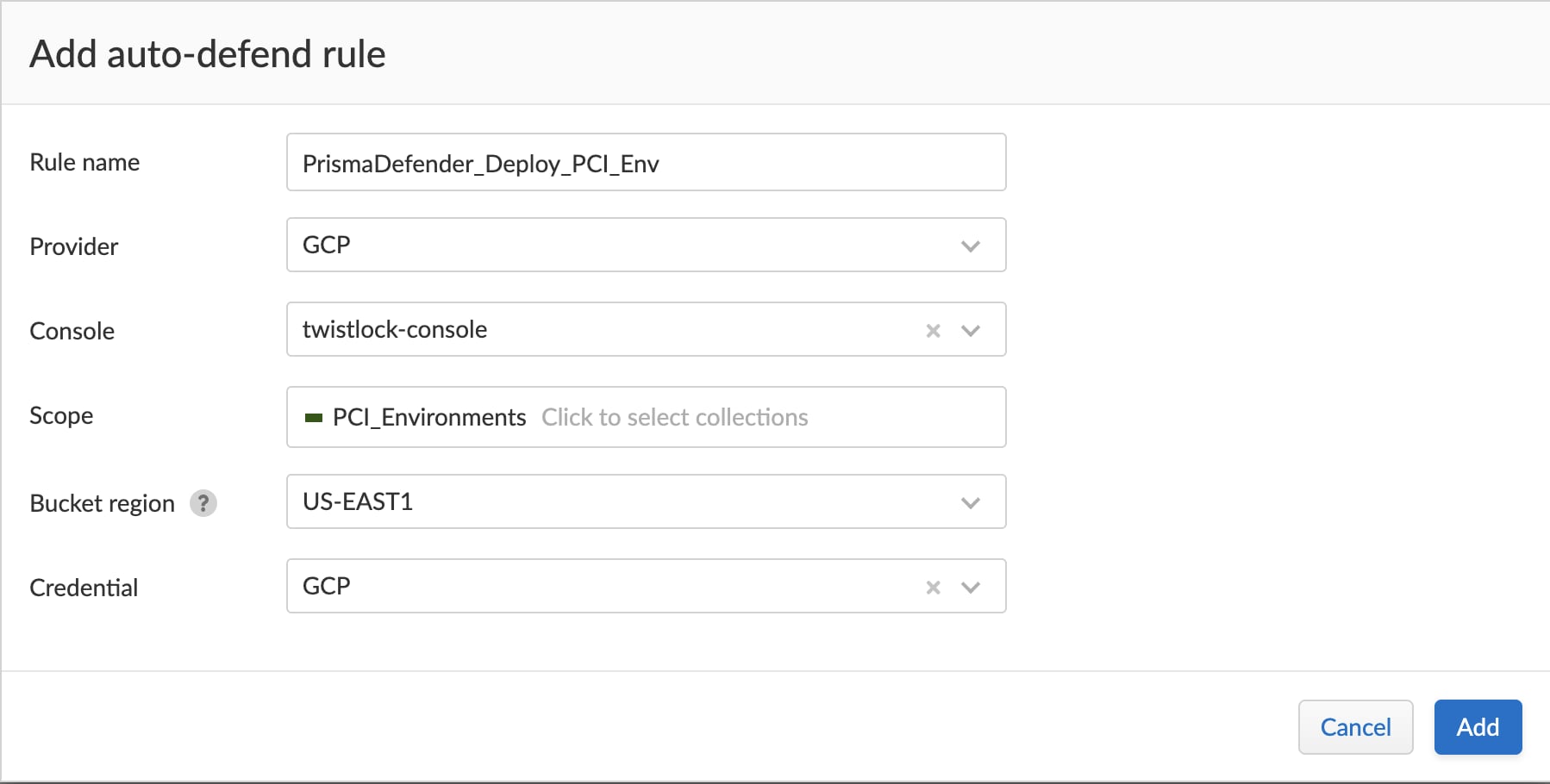
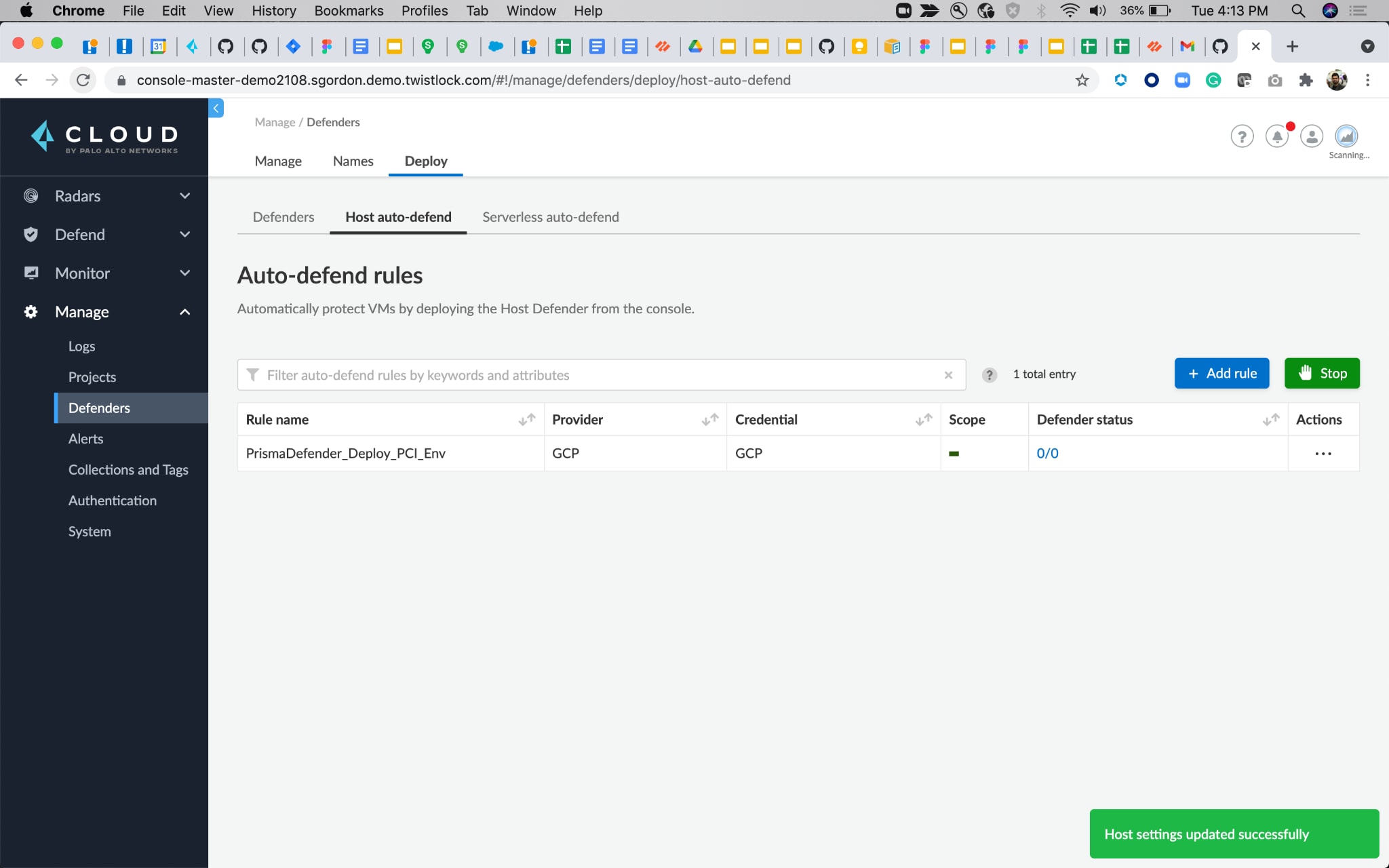
The rule deploys Defenders immediately and can be run periodically to cover any new hosts that have been spun up.
Prisma Cloud Defenders are lightweight and have a very low consumption, with their purpose-created architecture. With automated discovery, deployment and upgrades, Prisma Cloud Defenders remove the need for any manual intervention and all maintenance overheads.
Conclusion
With cloud VMs being auto-discovered and auto-protected, Prisma Cloud delivers a combination of powerful capabilities that include scanning for vulnerabilities and compliance issues. Then specifically for the running environment, Prisma Cloud provides integrated runtime protection covering malware scanning, file integrity monitoring, log introspection, and network protection across Multi-Cloud environments.
The latest features for host auto-protection provide users with unified visibility and seamless deployments across these clouds to gain visibility and gain security coverage from a single console.
You can learn more about securing diverse architectures into runtime with our latest ebook, Why and How to Add Runtime Defense to Your Cloud Security Strategy.
For technical reference, please refer to the auto defend for hosts section in the documentation.
Related Blogs
Subscribe to Cloud Native Security Blogs!
By submitting this form, you agree to our Terms of Use and acknowledge our Privacy Statement. Please look for a confirmation email from us. If you don't receive it in the next 10 minutes, please check your spam folder.