Cloud Discovery and Exposure Management: Unveiling the Hidden Landscape
Identify shadow cloud assets, assess internet-accessible exposure risks, and remediate previously unmanaged risks with Prisma Cloud.
Speed and agility in application development often take precedence over security. While rapid innovation can fuel business growth, it can also spawn unknown and unmanaged assets — commonly referred to as shadow assets. These shadow assets compromise cloud security, exposing organizations to a myriad of risks.
Enter cloud discovery and exposure management (CDEM), a pivotal CNAPP capability that empowers security teams to identify, assess and remediate hidden cloud assets.
Rogue Cloud Sprawl Leaves Security Blind Spots
The cloud's inherent flexibility and scalability offer organizations a solid tech foundation for innovation. The same attributes, though, can lead to cloud asset sprawl. Cloud-based IT infrastructure exists in a state of flux with an average 20% of externally accessible cloud services changing every month.1 Without continuous visibility, it’s easy to lose track of accidental misconfigurations and the steady spread of shadow IT within an organization.
Research from Palo Alto Networks paints a sobering picture. Though difficult to fathom, approximately 30% to 40% of an organization's publicly accessible attack surface is unknown.2 In other words, a large portion of an organization's workloads are outside the purview of security teams.
These unknown assets can range from unsecured databases and exposed APIs to rogue virtual machines. The worst part is that attackers can discover and exploit them before internal security teams even know about them.
Introducing Cloud Discovery and Exposure Management
In our recent Darwin release, Prisma Cloud introduces cloud discovery and exposure management (CDEM) functionality, giving security professionals an outside-looking-in view of their cloud environment and the critical ability to discover, evaluate, and mitigate unknown and unmanaged internet exposure risks.
By discovering unattributed and internet-exposed assets across Amazon Web Services, Azure, and Google Cloud Platform, Prisma Cloud enables security teams to investigate risks and communicate them to application owners to help facilitate their timely remediation. Prisma Cloud also provides native workflows to convert unmanaged assets into managed assets protected by the continuous, automated monitoring of cloud security posture management (CSPM).
With Prisma Cloud, users can:
- Compile a complete asset inventory that includes managed and unmanaged cloud assets
- Determine internet exposure risks with an outside-in view of shadow IT assets in the public cloud
- Remediate hidden exposures to improve cloud security posture
Discover Your Unmanaged Assets
Cloud security posture is only as strong as visibility is long. Prisma Cloud provides comprehensive visibility into all your resources — those within and beyond your security teams' view — by scanning the entire IPv4 space. In regularly performed scans, it identifies all cloud assets associated with your organization, including shadow resources you unknowingly inherited through any number of common practices.
Taking an attacker’s view of internet exposures, Prisma Cloud correlates data from a variety of sources, including IP registration, autonomous system number (ASN) advertisement, certificates and domain name system. It then matches this data to the full set of internet-facing systems and services to attribute assets the organization and provide the organization with accurate ownership details.
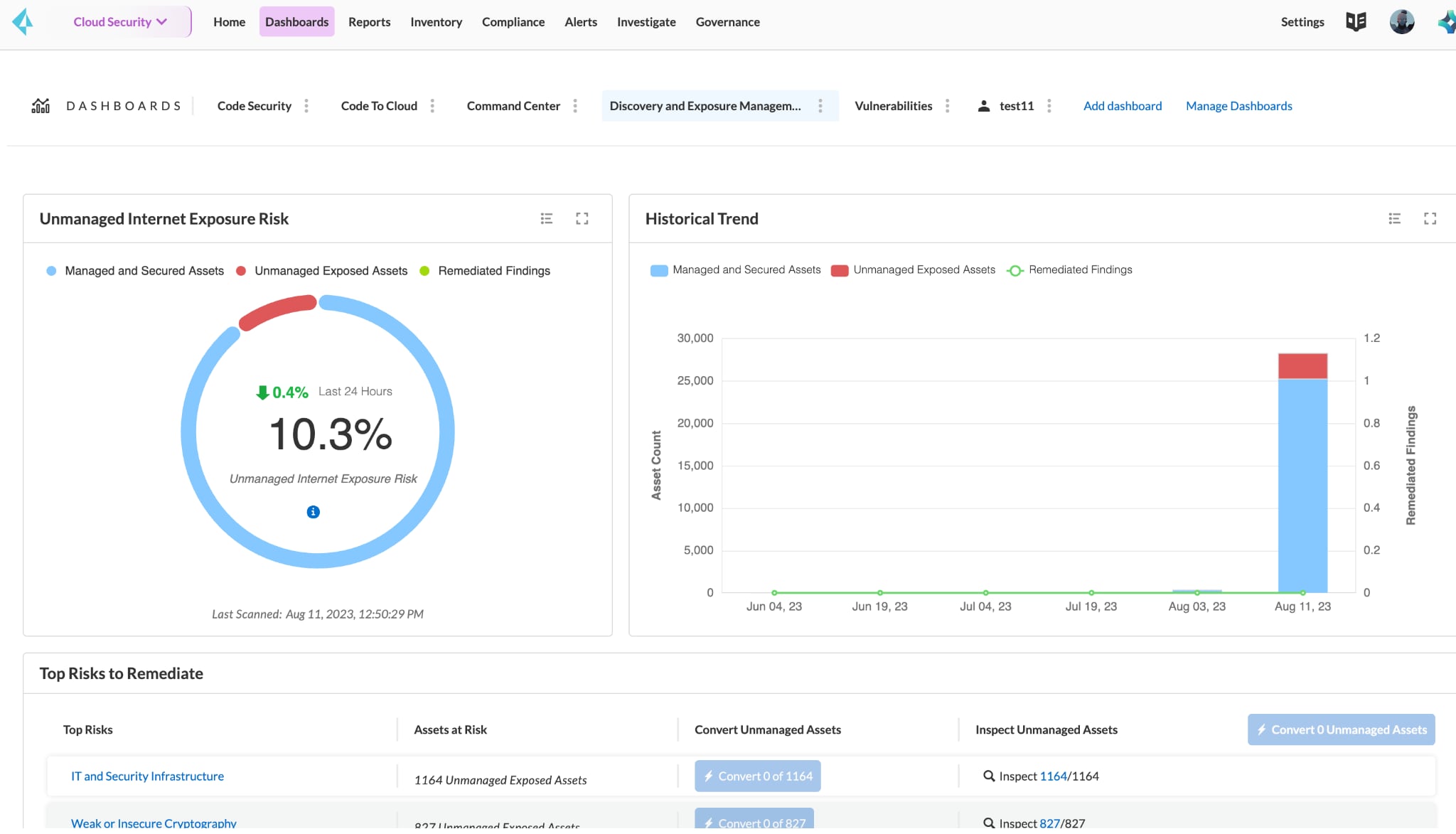
Exposure Risk Assessment
Identifying rogue assets is only half the battle. Understanding the risks they pose is equally crucial. Once Prisma Cloud identifies and attributes all internet-exposed assets to a specific organization, the platform conducts an exhaustive assessment of internet exposure risk.
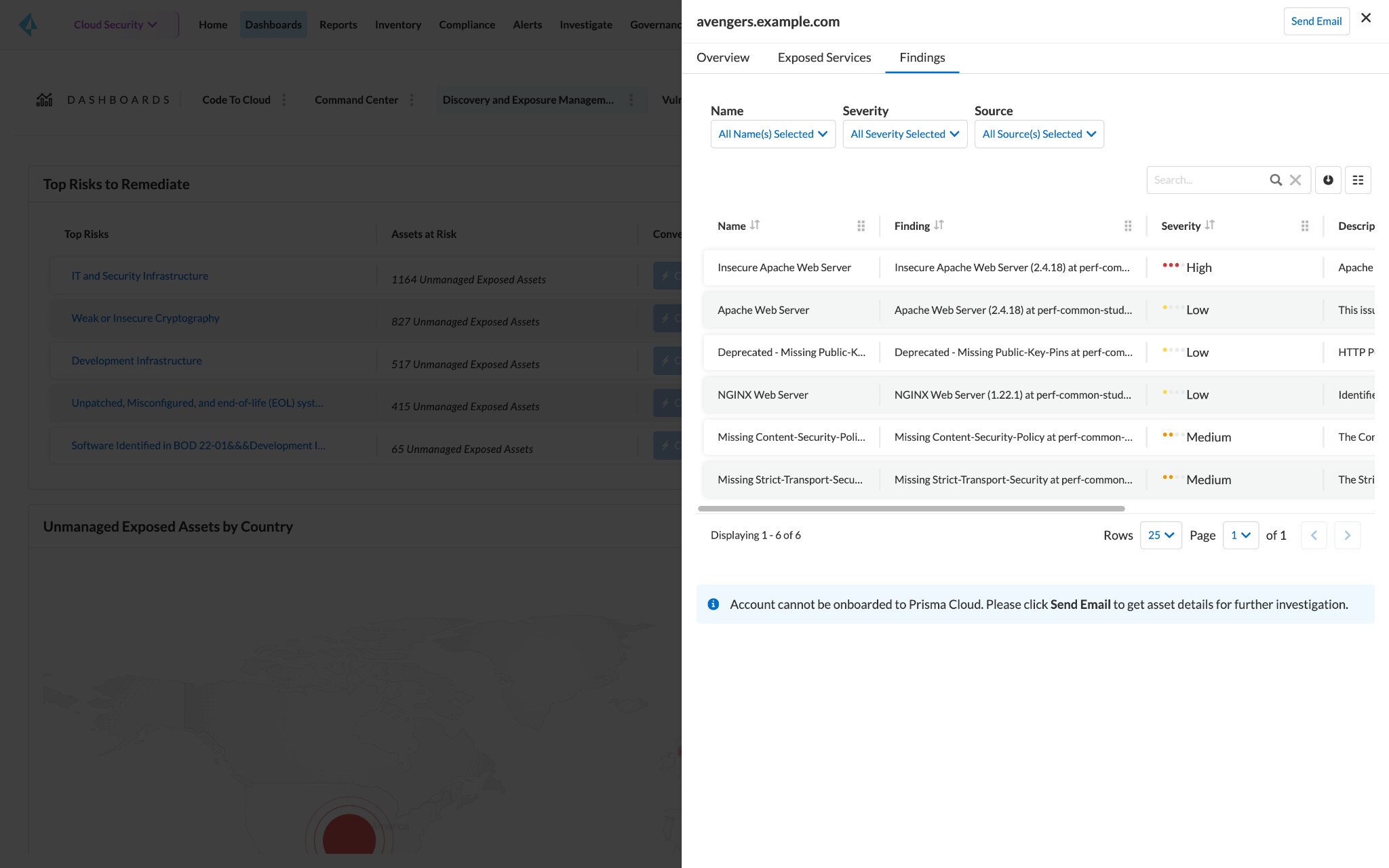
The platform identifies risks based on more than 650 predefined policies across 12 categories, each meticulously crafted to address specific vulnerabilities. It can spot publicly exposed databases, for instance, and insecure file-sharing services, such as unencrypted FTP servers and unclaimed S3 buckets.
Prisma Cloud’s CDEM capabilities also detect exploitable vulnerabilities and misconfigurations that enable privileged access to your environment, such as insecure open SSH and LDAP configurations. While identifying risks is crucial, prioritizing them transforms a list of vulnerabilities into actionable steps.
Risk Remediation
Prisma Cloud equips security teams with guided risk reduction workflows to remediate and triage findings.
Communicate Asset Context
Once security teams identify asset exposure details, they can easily communicate them within their organization using Prisma Cloud’s native workflows. Prisma Cloud provides details such as cloud account name, cloud provider, IP address, exposed services listing, port number, certificate details, asset ownership attribution information (like whois server, [registrar name]), and risk findings (expired certificates, weak cryptography, outdated software versions, etc.). By quickly conveying relevant information to asset owners, internal security teams can quickly address risks.
Onboard Accounts for Internal Management
While external visibility into cloud assets is a critical part of a security strategy, organizations still need to ensure ongoing internal insight and management. Using the asset context and findings, Prisma Cloud admins can convert unmanaged assets to managed, gaining full internal visibility and control.
Navigating Complex Cloud Use Cases with CDEM
Cloud discovery and exposure management addresses a variety of use cases.
Eliminating Shadow Cloud Deployments
Detect new VMs, databases and other resources in the cloud to keep security teams immediately aware of the appearances of unapproved workloads. Easily identify and reduce risks associated with rogue cloud assets by onboarding them to Prisma Cloud for ongoing security posture management.
Monitoring for Configuration Changes
Detect configuration changes to existing workloads when previously approved resources are reconfigured in a way that violates governance and compliance policies.
Streamlining Mergers and Acquisitions
Improve due diligence on security related to mergers and acquisitions by identifying newly added cloud assets and integrating them into the managed network without creating accidental exposures.
Boosting Zero-Day Response
Assess risk and reduce exposure to the latest CVEs by reducing mean time to detect (MTTD) and mean time to respond (MTTR) — without additional analysts.
Improving Compliance and Audits
Leverage complete, accurate asset lists to reduce audit duration and save costs on third-party audit and compliance processes.
Boost the Value of Cloud Security Tools
Improve cloud asset coverage and, as a result, the ROI of existing cloud vulnerability management tools, such as CSPM.
Integrated with Industry Leading CNAPP
Prisma Cloud stands out as the only CNAPP provider offering both CSPM and CDEM functionalities to effectively fortify your organization’s cloud security posture. With Prisma Cloud, you gain a holistic view of every asset across your ecosystem that identifies known and unknown assets. Armed with the dual inside-out and outside-in perspective, your teams will finally grasp the scope and context of the threats at their door — and have the horsepower to eradicate them.
Learn More
Tune in to our on-demand webinar, CNAPP Supercharged: A Radically New Approach to Cloud Security, to learn about Prisma Cloud's latest innovations and how to streamline app lifecycle protection. And don’t miss an opportunity to test drive best-in-class code-to-cloud security with a 30-day Prisma Cloud trial.
References
- 2023 Cortex Xpanse Attack Surface Threat Report, Palo Alto Networks, September, 2023.
- 2022 Cortex Xpanse Attack Surface Threat Report Vol. 2.1, Palo Alto Networks, July, 2022.
Related Blogs
Subscribe to Cloud Native Security Blogs!
By submitting this form, you agree to our Terms of Use and acknowledge our Privacy Statement. Please look for a confirmation email from us. If you don't receive it in the next 10 minutes, please check your spam folder.