Implement Zero Trust with Just-in-Time Access
Rapid migration to cloud services presents organizations with new security challenges. A common issue security teams encounter is the excessive granting of privileges to both user and machine identities. While intended to avoid disrupting daily operations, this practice increases the risk of cyberattacks by expanding the permission surface, compromising the organization's security posture.
The complexity of identity and access management (IAM) and the lack of visibility and control over identity permissions often cause this overprivileged access dilemma. Security teams frequently lack the necessary insight into the effective permissions of identities and their usage patterns, making the remediation of over-privileged access a daunting task.
IAM is a factor in nearly every cloud attack. Research by ESG indicates that 99% of organizations to have suffered a cybersecurity incident acknowledge the role of credentials in exposing their cloud environment.1 It’s imperative to understand the overall cloud IAM risk and to devise a plan to minimize it.
Traditional IAM solutions, like least privilege access controls, attempt to mitigate the risk of overprivileged access but often fall short. These solutions grant permissions that are only occasionally needed by the users and machine identities that receive them. Consider a user who needs elevated permissions to deploy a new application. With traditional IAM solutions, this user would continuously possess the elevated permissions, inadvertently creating opportunities for security breaches if their account is compromised.
While least privilege access controls undoubtedly help reduce risk, they don’t eliminate it. If permissions remain constant, referred to as "standing permissions," the potential for a compromised identity to provide access to the environment exists. To effectively tackle the problem of overprivileged access in cloud security, a more agile security solution is needed.
Level Up Identity Security with Just-in-Time Access
To address modern security challenges, just-in-time (JIT) access has become a pivotal security practice. The true Zero Trust approach to managing cloud identities involves removing risky permissions and then authorizing access to cloud resources only when needed. With JIT access, user and machine identities request precise permissions on an as-needed, time-limited basis.
Over 50% of identities are Super Admins — users or workloads with access to all permissions and resources — which poses a significant risk to an organization. If any of these identities become compromised, an attacker will have access to everything. Cloud infrastructure entitlement management (CIEM) security solutions aim to reduce the number of identities with these permissions to only those who actually need them, adhering to the principle of least privilege.
JIT allows organizations to take this security measure further by removing these standing privileges. For example, by leveraging JIT, organizations could strip all Super Admin privileges, significantly reducing their attack surface, and then only allow use of these permissions on an as-needed, time-limited basis. JIT access enables organizations to enhance their security measures to combat the evolving cloud attack landscape.
A Smarter Approach to Cloud Security: Just-In-Time Access with Prisma Cloud
Prisma Cloud is excited to introduce just-in-time access for AWS as part of its groundbreaking Darwin Release. Prisma Cloud's JIT offers a comprehensive and effective solution to cloud identity security that surpasses the offerings of most CIEM vendors.
JIT access not only allows users to minimize their permissions surface by eliminating standing privileges and granting them as needed, but it’s also straightforward to implement. Integrations with Slack will enable JIT from Prisma Cloud to blend seamlessly into existing workflows, allowing users to request and manage permissions without logging into Prisma Cloud. Users can request multiple sessions simultaneously and even schedule sessions in advance.
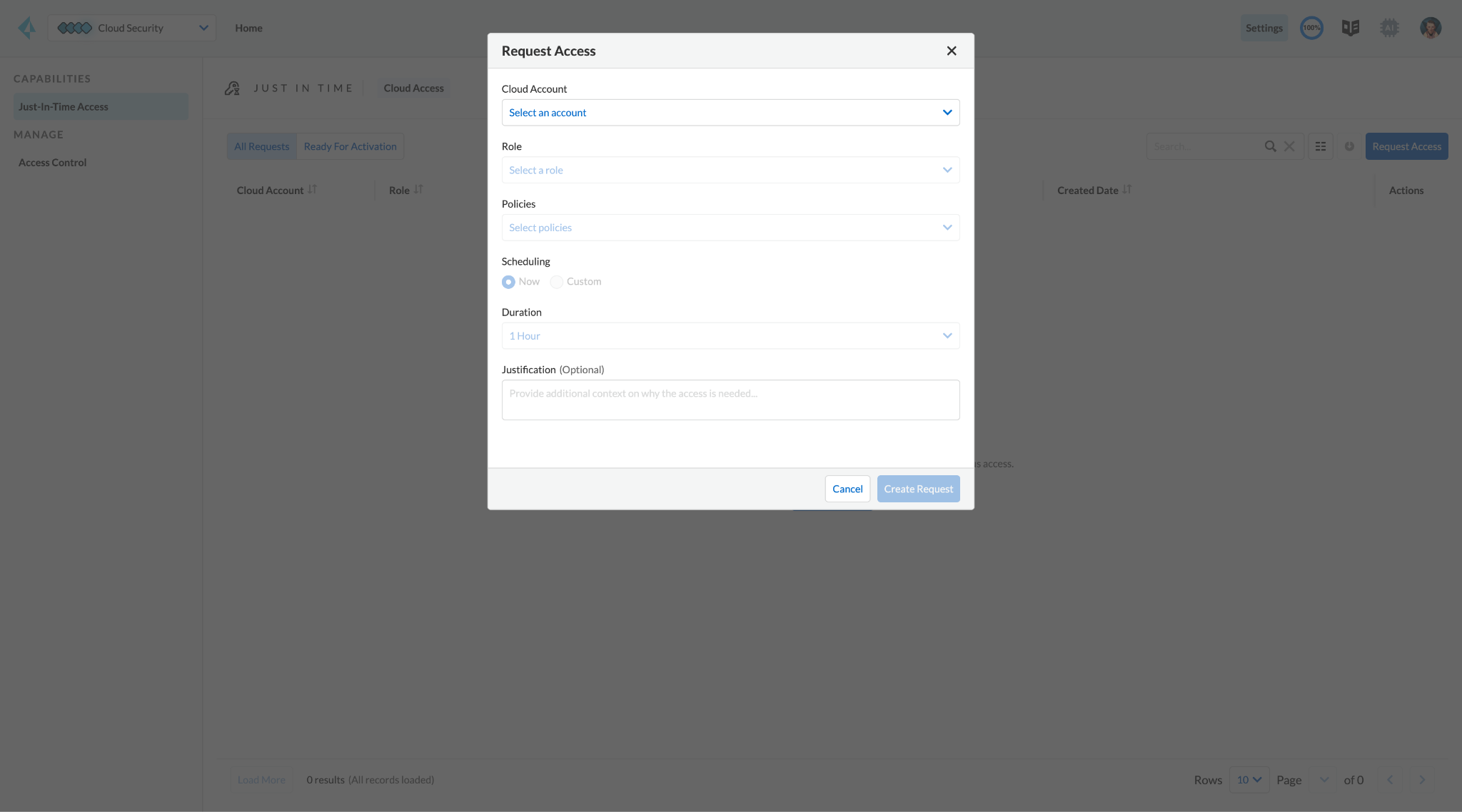
The simplicity of managing user permissions with JIT promotes better compliance with security regulations and reduces the risk of violations. Security teams can monitor active sessions and terminate unauthorized sessions immediately.
Exploring Key Just-in-Time Access Use Cases
Prisma Cloud JIT access empowers businesses to reimagine their cloud security strategy through various use cases.
Deployment and Maintenance: Streamlined Access Management
JIT access significantly streamlines permission management for deployment and maintenance processes. For instance, a user might require elevated permissions to deploy a new application once a week. Prisma Cloud can grant these permissions solely for the deployment duration. Once the session ends, the user's elevated permissions are automatically revoked, simplifying IAM access maintenance for cloud security teams.
Incident Response: Rapid and Secure Access for Security Analysts
Timely response to security incidents is vital to minimize damage. JIT access ensures that security analysts can quickly and securely access necessary resources during investigations. An analyst might require temporary elevated permissions to probe a suspicious event in the cloud, for example. Prisma Cloud can grant these permissions for the investigation period.
Auditing and Compliance: Simplified Access for Auditors
Auditors often need access to sensitive cloud resources to ensure compliance with security regulations. JIT access simplifies this process by providing auditors with temporary access as required. Perhaps an auditor requires access to all cloud resources to perform a compliance audit. Using Prisma Cloud JIT, the auditor can receive access for the duration of the audit, after which the access is automatically revoked.
Unlock Next-Level Cloud Security with Prisma Cloud CNAPP
At Palo Alto Networks, we strive to offer our users a world-class experience that synergizes the needs of application developers and security professionals. Prisma Cloud's JIT access is an ideal solution for companies focused on enhancing their cloud identity security.
Prisma Cloud JIT stands out with its comprehensive cloud-native application protection platform (CNAPP) capabilities, including Code to Cloud™ intelligence. Prisma Cloud connects the dots between application risk, security signals and runtime environments throughout the application lifecycle, providing actionable context. With its revolutionary Code to Cloud intelligence, Prisma Cloud represents a significant advancement in cloud security, redefining the standards of possibility.
Learn More
To learn about Prisma Cloud's latest innovations, tune in to our on-demand virtual event, CNAPP Supercharged: A Radically New Approach to Cloud Security, where we’ll show you how to streamline app lifecycle protection.
And don’t miss an opportunity to test drive best-in-class code-to-cloud security with a free 30-day Prisma Cloud trial.
References
- Enterprise Strategy Group Research Brief, The Importance of Cloud Entitlements for Managing Cloud Security Risk, June 2023.
- Review of 2023 State of Cloud Permissions Risks Report. 2023. Microsoft Security. https://query.prod.cms.rt.microsoft.com/cms/api/am/binary/RW10qzO.
Related Blogs
Subscribe to Cloud Native Security Blogs!
By submitting this form, you agree to our Terms of Use and acknowledge our Privacy Statement. Please look for a confirmation email from us. If you don't receive it in the next 10 minutes, please check your spam folder.