- 1. Firewall History Timeline
- 2. Ancient History-1980s: Firewall Predecessors
- 3. 1990s: First Generation of Firewalls—Packet Filtering Firewalls
- 4. Early 2000s: Second Generation of Firewalls—Stateful Firewalls
- 5. 2008: Third Generation of Firewalls—Next-Generation Firewalls
- 6. 2020: Fourth Generation of Firewalls—ML-Powered NGFWs
- 7. History of Firewalls FAQs
- Firewall History Timeline
- Ancient History-1980s: Firewall Predecessors
- 1990s: First Generation of Firewalls—Packet Filtering Firewalls
- Early 2000s: Second Generation of Firewalls—Stateful Firewalls
- 2008: Third Generation of Firewalls—Next-Generation Firewalls
- 2020: Fourth Generation of Firewalls—ML-Powered NGFWs
- History of Firewalls FAQs
The History of Firewalls | Who Invented the Firewall?
- Firewall History Timeline
- Ancient History-1980s: Firewall Predecessors
- 1990s: First Generation of Firewalls—Packet Filtering Firewalls
- Early 2000s: Second Generation of Firewalls—Stateful Firewalls
- 2008: Third Generation of Firewalls—Next-Generation Firewalls
- 2020: Fourth Generation of Firewalls—ML-Powered NGFWs
- History of Firewalls FAQs
There is not one inventor of the firewall. The firewall is the result of network security advancements many experts made over time, including Jeff Mogul, Paul Vixie, Brian Reid, William Cheswick, Steven Bellovin, David Presotto, Marcus Ranum, David Pensak, Nir Zuk, Fred Avolio, and Brent Chapman.
The history of firewalls began in the 1980s with basic packet filtering firewalls, continually evolving into the modern next generation firewall of today.
Firewall History Timeline
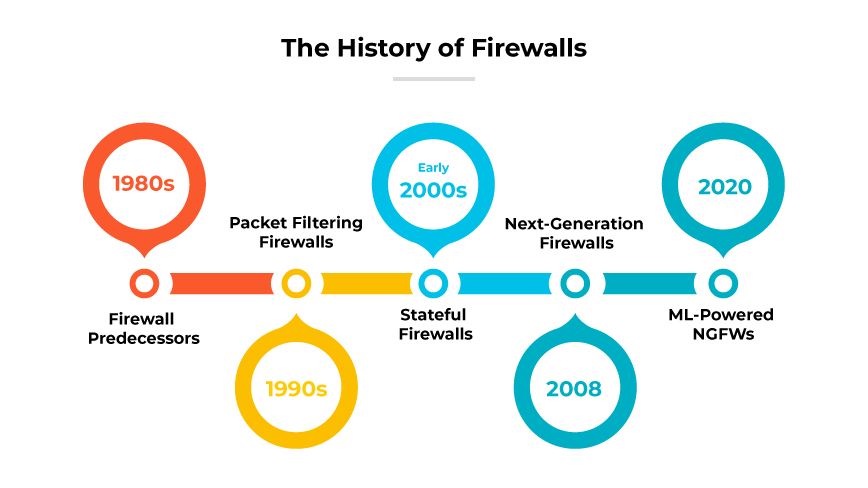
- Ancient history-1980s: Firewall predecessors
- 1990s: First generation of firewalls—Packet filtering firewalls
- Early 2000s: Second generation of firewalls—Stateful firewalls
- 2008: Third generation of firewalls—Next-generation firewalls
- 2020: Fourth generation of firewalls—ML-powered NGFWs
Ancient History-1980s: Firewall Predecessors
The genesis of firewall technology is rooted in age-old methods of physical defense when people first began building walls to stop intruders. Significant historical examples include the Great Wall of China and the moats and curtain walls of European castles.
Originally, the term “firewall” referred to partitions within buildings designed to confine fire hazards. Over time, this preventive concept was adapted for trains, which used iron walls to protect passenger sections from engine fires.1
Preceding the advent of firewalls, network routers emerged in the latter part of the 1980s. Network routers served as initial forms of network separation. These devices maintained basic isolation, ensuring any issues or chatty protocols did not cross from one side of the network to another. The foundational idea of segmentation further developed into what is known today as a firewall.
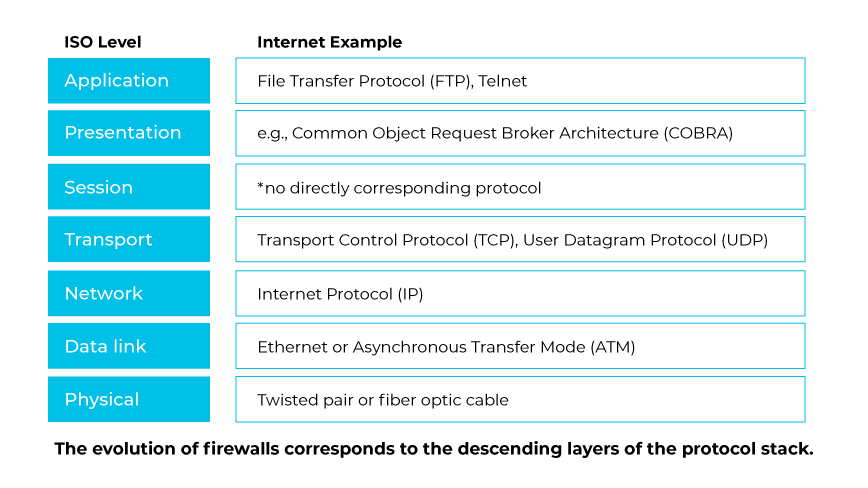
The history of firewall technology reflected a descending traversal of the networking protocol layers. Preliminary firewall systems concentrated on traffic filtering from the application level down to the transport and network level. These initial steps set the groundwork for the advanced network security measures embodied in modern firewalls.
AT&T Bell Laboratories played a crucial role in the history of firewalls by developing the first circuit-level gateway around 1989-1990. The concept AT&T Bell Labs introduced laid important groundwork for the next generation of firewalls. Over time, security experts continued expanding on these ideas and integrated them into the broader firewall technology that we are familiar with today.
1990s: First Generation of Firewalls—Packet Filtering Firewalls
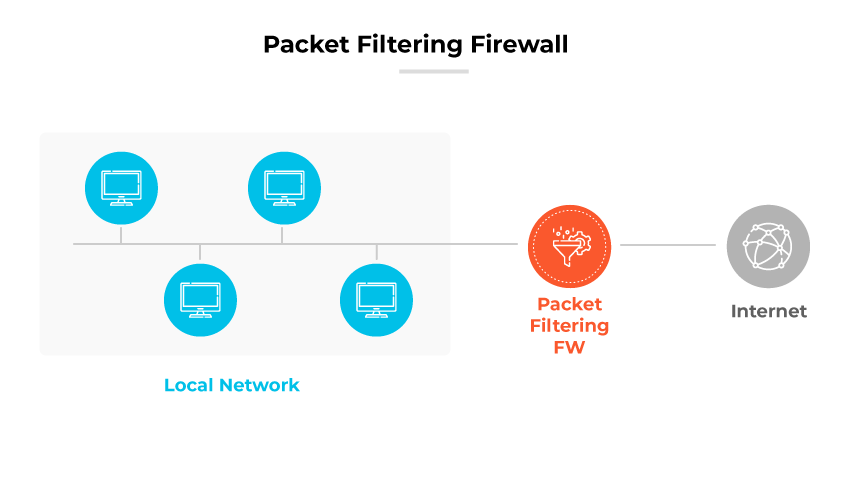
During the 1990s, the landscape of network security underwent a significant transformation with the introduction of the first generation of firewalls: packet filtering firewalls, a type of network firewall. The need for systems that could enforce security policies at the network level was becoming more pronounced as the use of interconnected networks expanded.
Packet filtering firewalls operate at a fundamental level by inspecting data packets that travel across the network. These firewalls would assess packets based on predefined rules that often considered the source and destination IP addresses, port numbers, and the protocol used, such as TCP or UDP. This process was akin to a mailroom sorting letters based on the address on the envelope, without opening the letters themselves.
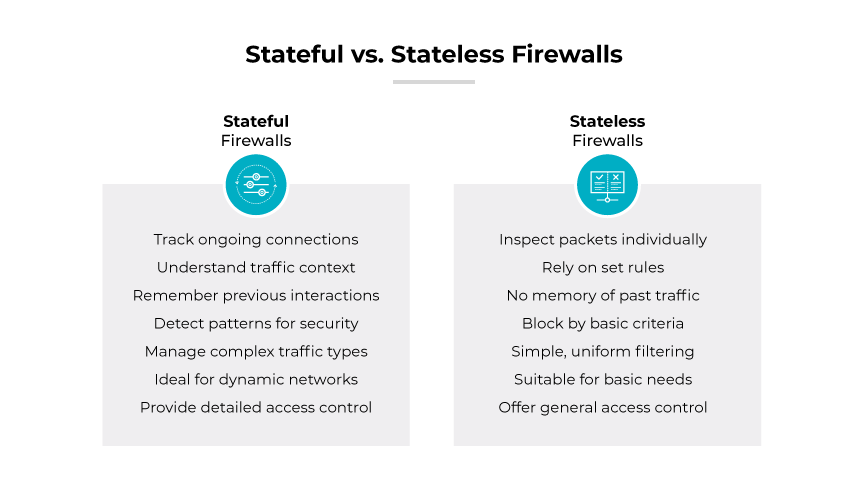
One of the critical attributes of these early firewalls was their stateless nature. They did not retain memory of previous packets, treating each new packet in isolation. Each packet's acceptance or rejection was based solely on the set of rules without the context of the packet's place in a communications sequence. This was a simple yet somewhat effective way to control incoming and outgoing network traffic.

However, this simplicity also led to vulnerabilities. Stateless firewalls could not understand the connection state, which made them susceptible to certain types of network threats that took advantage of the lack of historical data. For instance, stateless firewalls could not ensure incoming packets were part of an established and legitimate connection. This deficiency left networks open to various forms of spoofing and session hijacking attacks.
Despite these limitations, the development of packet filtering firewalls in the 1990s laid the groundwork for more sophisticated security measures. They represented the initial step toward recognizing and addressing the need for network security in an increasingly connected world. As the decade progressed, the limitations of packet filtering firewalls became clear, paving the way for the next generation of firewalls with stateful inspection capabilities.
Early 2000s: Second Generation of Firewalls—Stateful Firewalls
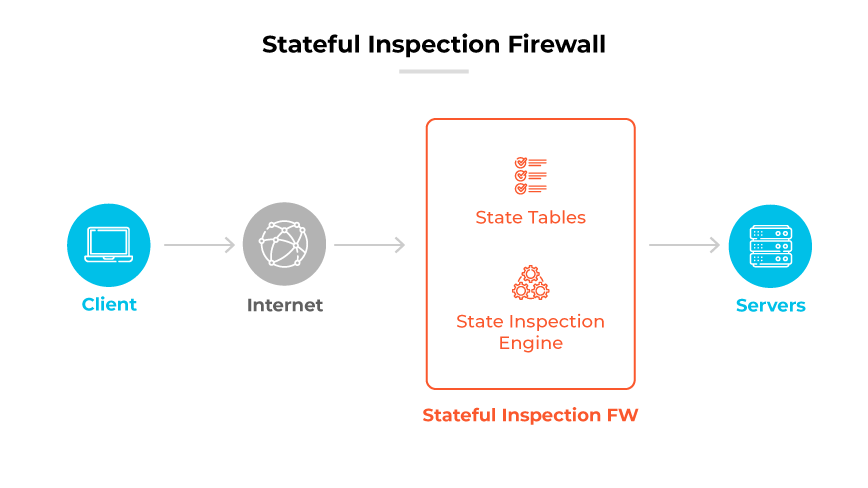
In the early 2000s, stateful firewalls emerged, ushering in the second generation in firewall technology. These systems represented a significant evolution from their predecessors, the simple packet filters. Stateful firewalls brought about a paradigm shift in network security by monitoring the state of active connections and determining the context of network traffic.
The design principle behind stateful firewalls was based on the concept that not all packets are independent entities; many are part of a larger conversation between hosts. By maintaining context-awareness, stateful firewalls could make more informed decisions about which packets to allow or deny. They assessed not just the packet itself, but also its relationship to previous packets in the same session. This was analogous to understanding not just sentences but the entire conversation in a dialogue.
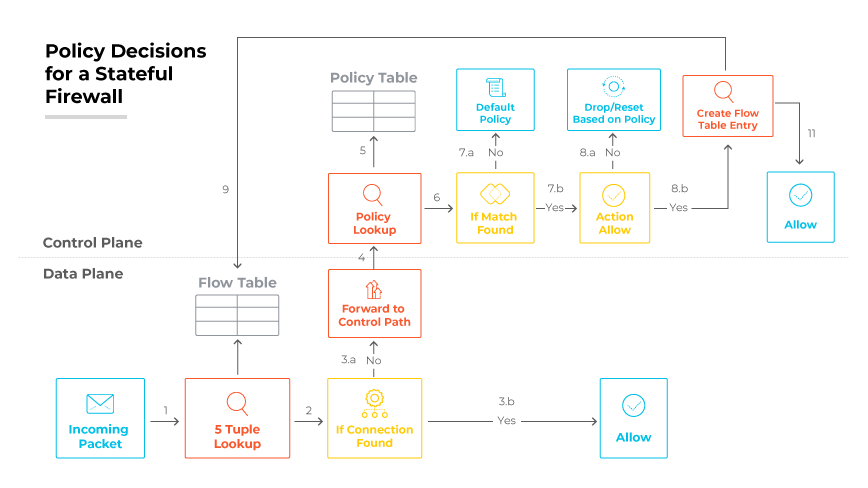
Stateful firewalls were able to track the state of network connections—such as TCP streams or UDP communication—by maintaining a state table. This table recorded all ongoing connections and could ascertain if an incoming packet was part of an established session. By doing so, they could prevent unauthorized access attempts that stateless packet filters could not. Stateful firewalls were providing a robust mechanism against a variety of network attacks that exploited legitimate connections.
Concurrent with the development of stateful firewalls, the early 2000s also saw the advent of application firewalls. With the increasing need for application-level security due to the rise of sophisticated web-based attacks, vendors enhanced stateful firewalls with additional features to analyze and filter traffic based on application data, leading to the creation of Unified Threat Management (UTM) systems. UTMs combined the traditional firewall capabilities with gateway antivirus, intrusion detection, and spam filtering into a cohesive platform that not only allowed or denied traffic based on state but also on content, thus significantly improving security measures.
The UTMs’ stateful packet inspection allowed inbound and outbound traffic on the network, while a web proxy filtered content and scanned with antivirus services. A separate intrusion prevention system (IPS) detected and blocked malicious traffic. Virtual private network (VPN) servers incorporated into the UTM could connect remote offices and allow remote users to access corporate resources. Finally, spam filtering acted on junk emails and phishing attempts.
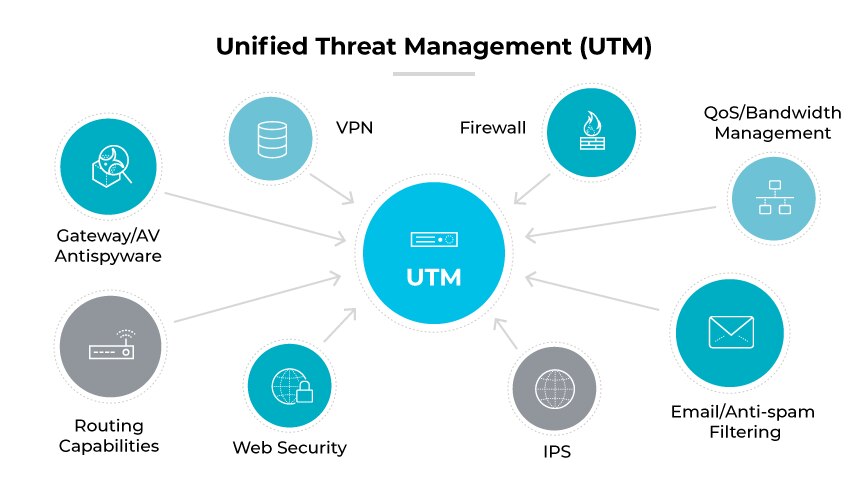
UTMs brought many disparate network security technologies together into a single appliance for ease of deployment and lower cost. However, there was no native integration between the different "modules" or "blades," which led to gaps in security, low performance, and complex policy management.
In essence, the development of stateful firewalls during this era was a direct response to the limitations of the first-generation packet filters. Security requirements had become more complex, and stateful inspection met the demands for enhanced security by inspecting the network at a deeper level. Despite their increased complexity, stateful firewalls managed to strike a balance between security and performance—a balance that would define network security measures for years to come.
The legacy of stateful firewalls is still evident today. They laid the foundation for modern security systems that continue to safeguard digital infrastructures. Their inception was not just an upgrade but a transformation that redefined the perimeter security of networked environments.
2008: Third Generation of Firewalls—Next-Generation Firewalls
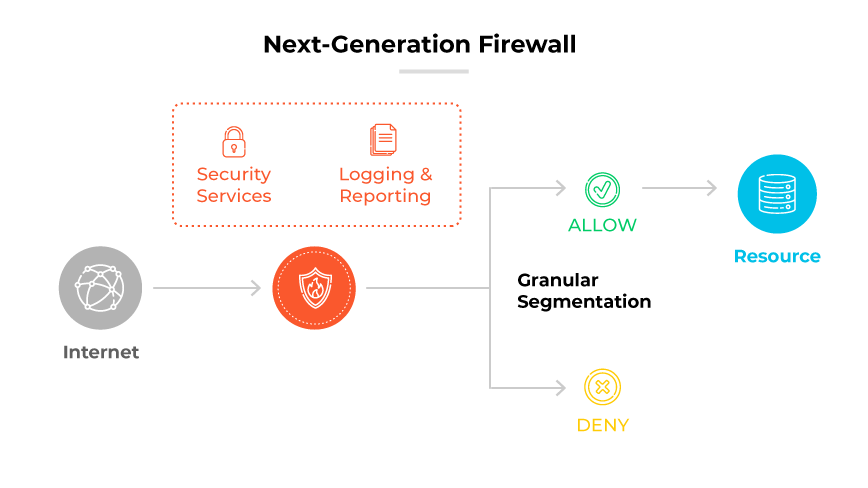
In 2008, Palo Alto Networks delivered the industry’s first next-generation firewall (NGFW). This marked the beginning of a new era in network security technology. Firewalls were no longer merely filtering ports and IP addresses but were also capable of deeper inspection to make informed decisions about what traffic can pass through a network.
The NGFWs introduced integrated intrusion prevention systems (IPS), full-stack visibility, and the ability to enforce security policies based on applications, users, and content. This level of control was essential because, by 2008, applications were increasingly using standard web ports to bypass traditional firewalls. This made it difficult to control unwanted or potentially malicious traffic.
NGFWs distinguished themselves by decoding applications regardless of port and protocol, offering full visibility into all applications crossing the network. This allowed administrators to create comprehensive, precise security policies. These policies were not just network-centric, but accounted for the nature of the traffic, applications involved, and users behind them.
With the ability to see and understand the content, NGFWs added a new dimension to firewall policies, enabling them to block malicious content and support corporate policies around data transmission. This was particularly important in a time when data leaks and breaches were becoming more frequent.
The NGFWs were capable of SSL decryption, allowing them to inspect encrypted traffic, which was a growing percentage of all internet traffic by 2008. This was critical because, without it, encrypted traffic would be a significant blind spot in network defenses.
Overall, the development of NGFWs in 2008 represented a significant shift from passive network devices. As NGFWs became the norm, network security systems became capable of performing deeper inspection and making real-time security decisions based on comprehensive data analysis. This was a key step in the evolution of firewalls, aligning network security more closely with the complex and dynamic nature of modern internet traffic and threats.
2020: Fourth Generation of Firewalls—ML-Powered NGFWs
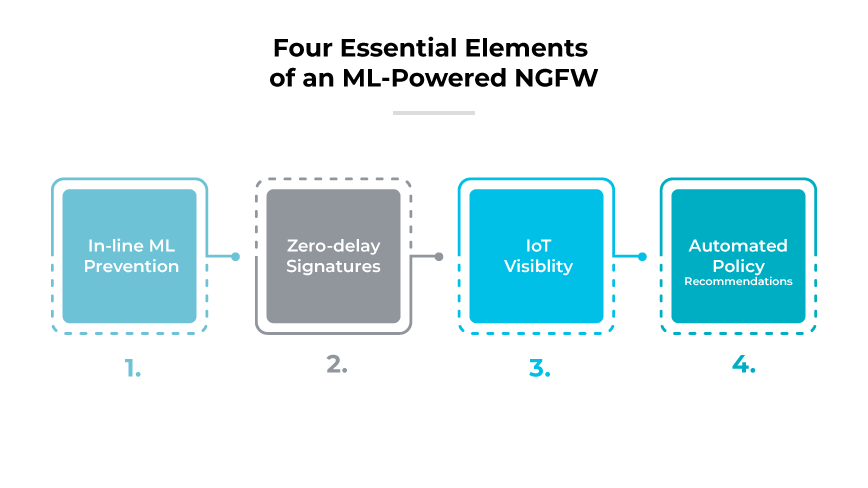
The latest firewall to date made its debut in 2020, when Palo Alto Networks introduced the first ML-powered next-generation firewall. This firewall uses machine learning to deliver proactive, real-time, and inline zero-day protection.
These NGFWs go beyond traditional threat detection by applying machine learning to analyze network traffic patterns and identify anomalies that could indicate new types of cyberattacks. This provides a dynamic defense mechanism that adapts to evolving threats without relying solely on known threat signatures.
With comprehensive device visibility and behavioral anomaly detection, ML-powered NGFWs are particularly adept at securing IoT devices. They do so by generating and enforcing security policies based on continuous learning from network traffic, which significantly reduces the exposure window to new threats. This proactive security strategy helps organizations safeguard networks against previously unencountered sophisticated attacks.
ML-powered NGFWs also streamline security management by recommending policy updates derived from network telemetry data, minimizing administrative overhead. These recommendations facilitate quick adaptation to security challenges, reduce human error, and ensure security protocols are always up-to-date. As a result, organizations can maintain a robust security posture, capable of responding to threats as they emerge.