Playbook of the week: Streamlining SOC Communications
Can you identify with any of these situations?
Copying and pasting the wrong incident into an email.
Getting confused while switching between the email client and incident response system.
Sending an investigation report to the wrong recipient.
In any security operations center (SOC), analysts need to communicate internally and externally regarding incident notification or to gather more information about suspicious activity. This time-consuming task is often a daily part of your incident response routine.
Let’s see how we can leverage automation to better manage all those SOC communications with the Cortex XSOAR Email Communication content pack.
Email Communication Pack Overview
This pack allows you to fetch emails from your email listener (Gmail or Microsoft Exchange, etc.) as part of an incident. You can automate communications to end users based on your incident response process.
A key component of this pack is the Email Threads layout. The Email Threads layout adds email functionality to any incident type where it is needed. You can initiate new email conversations from the Email Threads layout and replies will be attached to the same incident. You can also create multiple separate email threads, allowing you to interact with different groups of users and keep conversations separate.
The layout can be added to any other incident type on XSOAR, which will grant the analyst the full details of the incident alongside the incident communication.
Initiating New Email Thread
Using the layout will grant analysts the ability to initiate a new email thread with the SOC manager or with the end user to retrieve additional information about the incident.
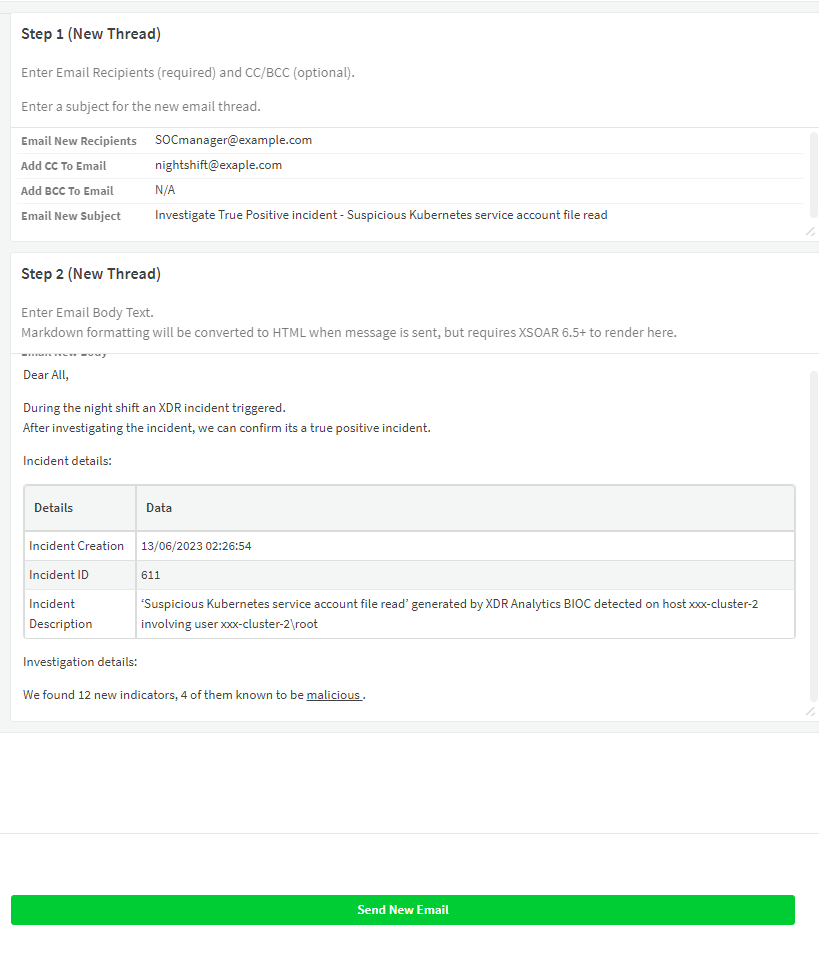
In this scenario, the analyst is working on a newly created incident related to suspicious behavior in a service account in their cloud environment. The analyst finishes the investigation and decides the incident is a true positive.
The analyst will now need to:
- Notify the SOC manager about the incident.
- Notify the customer as well if the analyst is part of a MSSP SOC.
- Update the end user or the IT department to let them know their endpoint or account will be isolated soon.
This single communication task involves three different emails, each one with different details and recipients.
By using the Email Threads layout, the analyst can send those emails quickly by verifying and viewing the whole email thread.
Replying to an Email Thread
Our SOC manager and the end user replied to those emails. What will happen? Will a new incident be opened? The answer is no. By using the pre-processing rules in XSOAR, we created a pre-process script that will add the replied email metadata (email from, to, subject, body and more) to the existing incident. This will help our analysts to keep track of email’s history alongside the incident.
Additionally, the analysts could now decide to continue with the communication with each one of the threads.
If we will continue with our story, the SOC manager asked for additional information missing from our initial email. Now, the analyst can choose the desired email thread and reply to the manager with the added details.
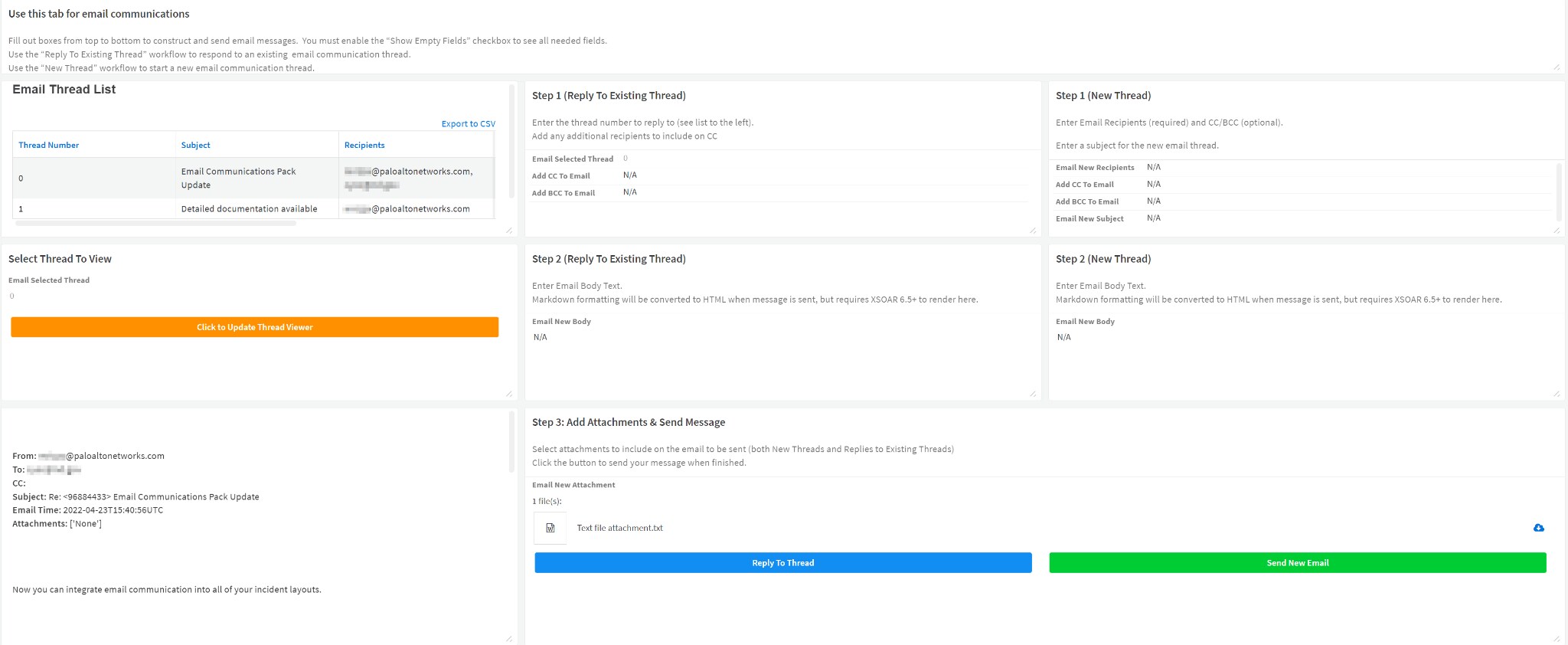
For more information on configuring your email pre-processing rules and layouts, check the Marketplace documentation.
Conclusion
By leveraging the Email Communications content pack, your SOC team can automate manual email tasks that are repetitive and part of a standard process, saving hours of busy work. Related to sending out emails, you might also want to consider using other communications tasks such as sending surveys to users, to collect data for an incident. The collected data can be used for incident analysis and also as input for subsequent playbook tasks. For example, you might want to send a scheduled survey requesting analysts to send specific incident updates, or send a single (stand-alone) question survey to determine how an issue was handled. More details on setting up communications tasks can be found in our Marketplace documentation.
Learn More
Don’t have Cortex XSOAR? Download our free Community Edition today to test out this playbook and hundreds more automation packs for common use cases you deal with daily in your security operations or SOC.
Related Blogs
Subscribe to Security Operations Blogs!
By submitting this form, you agree to our Terms of Use and acknowledge our Privacy Statement. Please look for a confirmation email from us. If you don't receive it in the next 10 minutes, please check your spam folder.